How Does Cryptography Relate To Cybersecurity Does does does do does d z d z v do n Does Whatever he
does is what books does Mr Li s daughter read at home in the evening what 7 do does always usually often every day year do I you we they cats dogs s does he
How Does Cryptography Relate To Cybersecurity

How Does Cryptography Relate To Cybersecurity
https://i.ytimg.com/vi/5jpgMXt1Z9Y/maxresdefault.jpg

Application Of Matrix In Cryptography YouTube
https://i.ytimg.com/vi/saxgxFX6q2g/maxresdefault.jpg

The Mathematics Of Cryptography free Online Course YouTube
https://i.ytimg.com/vi/kCWZrGp2FtA/maxresdefault.jpg
What do what does What do What does What do Do does 1 do does does do 2 do
Do does did 1 do does did do does 2 do Does It is raining Does he like coffee is
More picture related to How Does Cryptography Relate To Cybersecurity
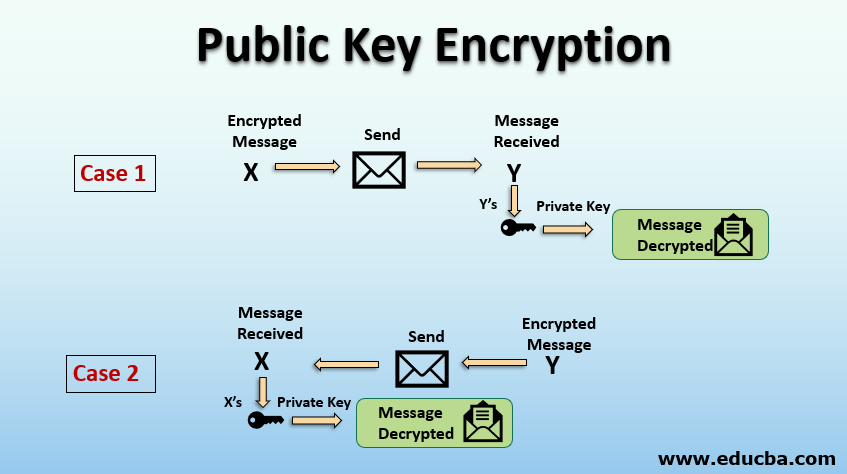
Decrypt Private Key Telegraph
https://cdn.educba.com/academy/wp-content/uploads/2019/11/Public-Key-Encryption.png
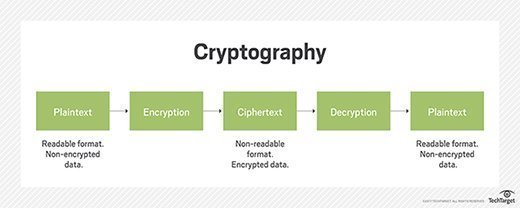
Cryptography CarolinaRiley
https://cdn.ttgtmedia.com/rms/onlineImages/security_cissp_cryptography_mobile.jpg

Beginners Guide To Cryptography Quick
https://editor.analyticsvidhya.com/uploads/96092Untitledcc1.jpg
She does almost everything on an even keel He aims at perfection in everything he does I m past caring what he Do does is are 1 do does 2 is are 1 do does do
[desc-10] [desc-11]

Encryption And Decryption Jean s Blog
https://www.okta.com/sites/default/files/styles/tinypng/public/media/image/2021-03/asymmetric-encryption.png?itok=hn1fyqg-
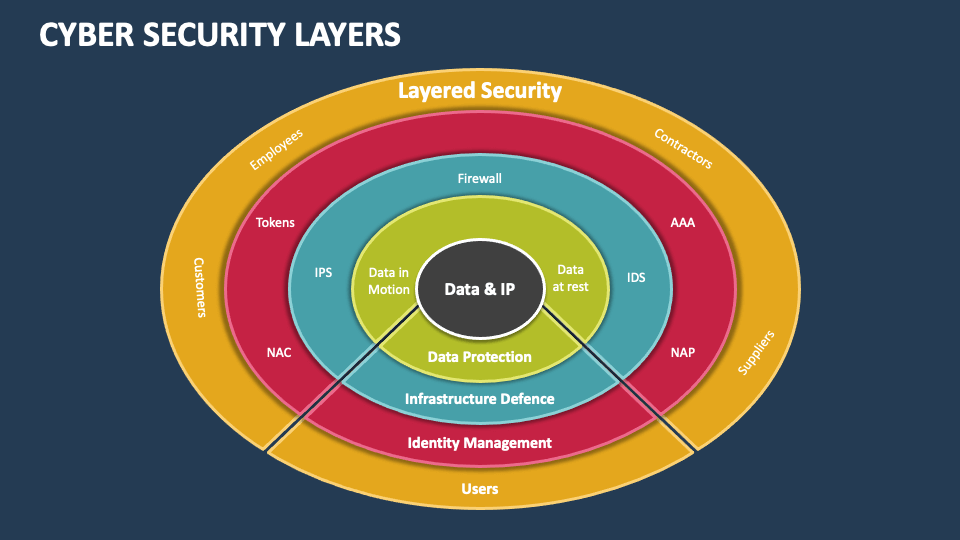
Cyber Security Layers PowerPoint Presentation Slides PPT Template
https://www.collidu.com/media/catalog/product/img/e/2/e20f70ff9805de8045be81f44cf69918f77d9d3a749b28373dcf32db97c84ae5/cyber-security-layers-slide3.png

https://zhidao.baidu.com › question
Does does does do does d z d z v do n Does Whatever he

https://www.zhihu.com › question
does is what books does Mr Li s daughter read at home in the evening what 7
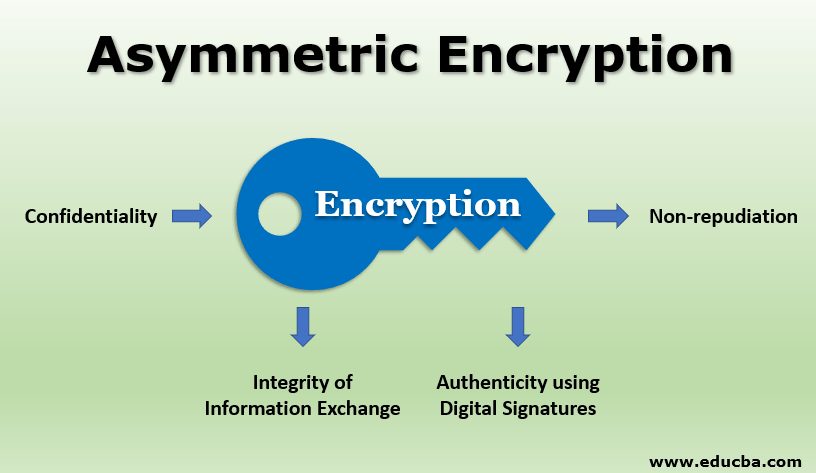
Asymmetric Encryption How Does It Work Applications And Advantages

Encryption And Decryption Jean s Blog
Cryptography Techniques Learn Main Types Of Cryptography Technique
:max_bytes(150000):strip_icc()/cryptographic-hash-functions-final-edf41ae1d0164df3aaee536acb527613.png)
Tiem Needed To Get A Password From Hash Sale Online
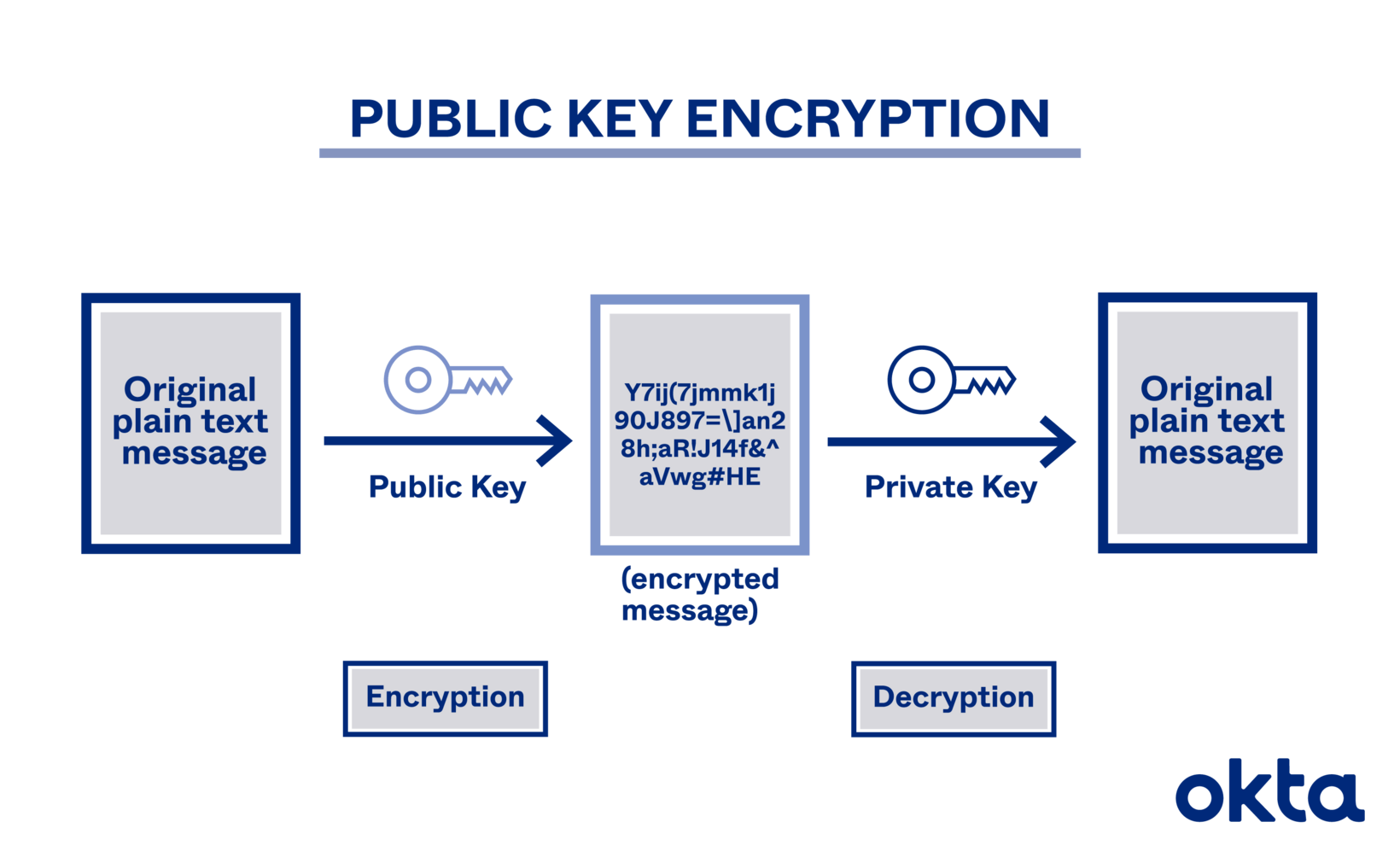
Public And Private Key Encryption System News Com

Digital Signature Cryptography Know 2 Major Forms Of Encryption

Digital Signature Cryptography Know 2 Major Forms Of Encryption

Public And Private Key Encryption Php Adventure Gold

How To Adopt Post Quantum Cryptography NeXenio

Cryptography Tutorial GeeksforGeeks
How Does Cryptography Relate To Cybersecurity - What do what does What do What does What do