Hsm Key Management Best Practices There are no decent HSM Protection Profiles yet so at the least you re going to have to read the Security Problem Definition threats and assumptions before you have an idea what the
TPM Trusted Platform Module and HSM Hardware Security Module are considered as cryptoprocessor but what are the differences exactly Does one of them has What are the differences between a Hardware Security Module HSM and a Secure Element SE Can both terms be used interchangeably I came across various
Hsm Key Management Best Practices

Hsm Key Management Best Practices
https://i.ytimg.com/vi/n5TisbO-eYI/maxresdefault.jpg

Azure Key Vault Managed HSM Fundamental Design Aspects Public Cloud
https://i.ytimg.com/vi/skzcAh3lzDU/maxresdefault.jpg

What Is Key Management Key Management Best Practices Encryption
https://i.ytimg.com/vi/O0xXQ06NHG4/maxresdefault.jpg
Are there any Open Source Hardware Security Modules meeting OSHWA requirements I ve worked with Utimaco HSMs but I m not a big fan of closed source The Use of HSM s for Certificate Authorities HSM s are common for CA applications typically when a company is running there own internal CA and they need to
The Thales HSM tools allow the key to be split into segments each encrypted with a transport key so that individual key holders can make their way to the key ceremony I am considering using a HSM server for storing my private key for increased security but I want to keep the verification workflow the same for my users For example I
More picture related to Hsm Key Management Best Practices
SAFENET HSM
http://symmetric.al/web/images/Demo/portfolio/hspprod.PNG

BYOK AWS Security Blog
https://d2908q01vomqb2.cloudfront.net/22d200f8670dbdb3e253a90eee5098477c95c23d/2021/03/09/Demystifying-KMS-keys-2021-ForSocial.jpg
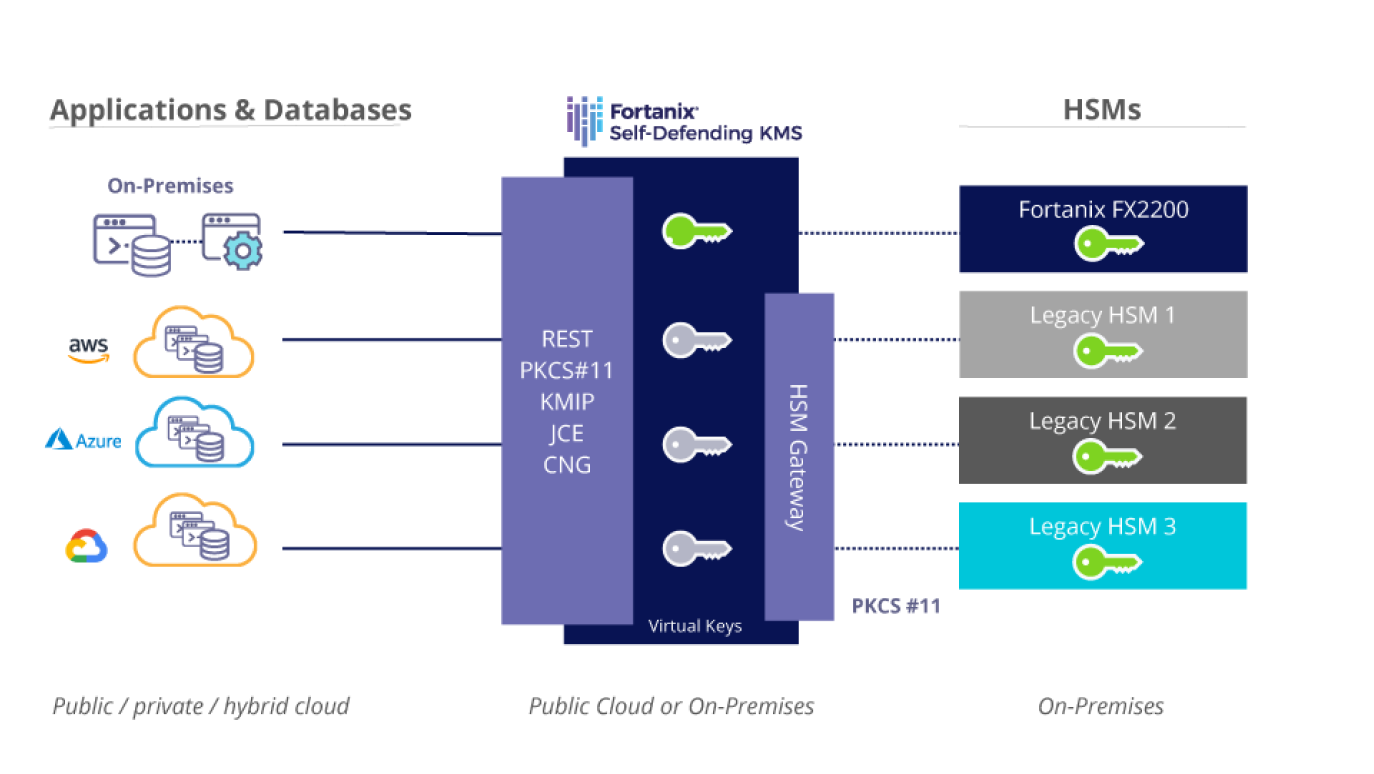
Hardware Security Module HSM Fortanix
https://cdn.aglty.io/fortanix/solutions/use-case/hardware-security-module/overview-image.png
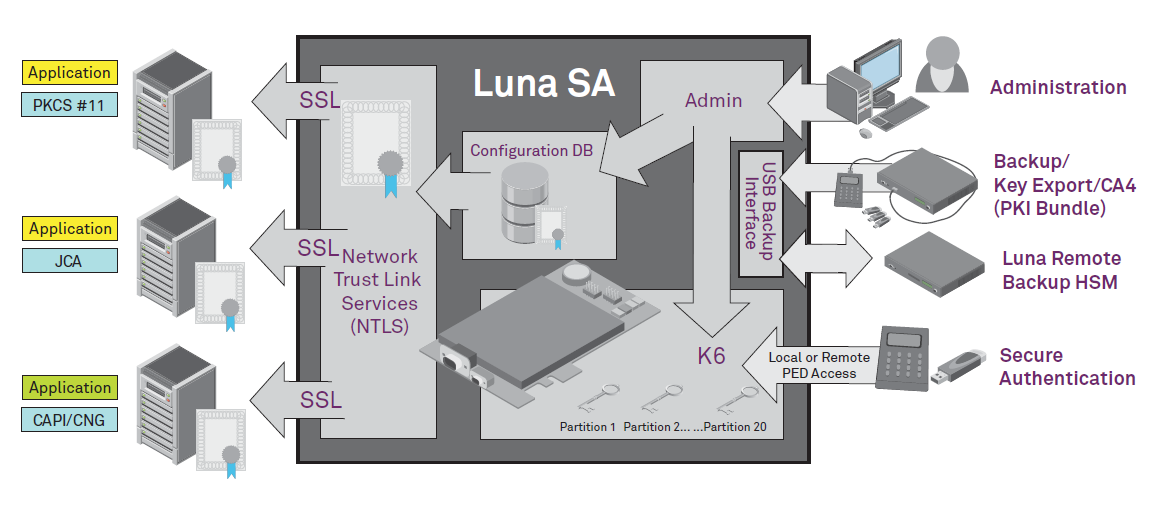
A hardware security module HSM is essentially a trusted computer that manages encryption keys or signing keys outside of the normal server operating system It doesn t provide the 85 DG HSM 85GM SAMYANG 85 85 DG DN GM 90g
[desc-10] [desc-11]
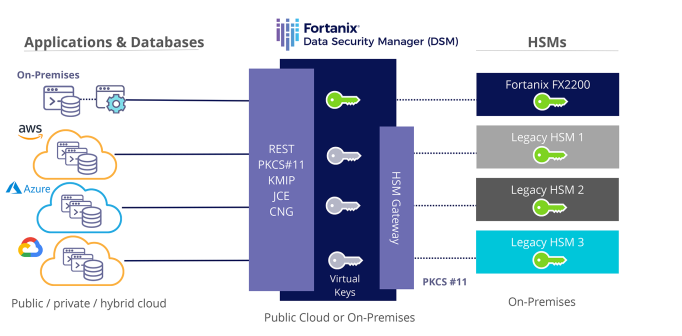
Hardware Security Module HSM Solutions Use Case Fortanix
https://cdn.aglty.io/fortanix/products/feature-pages/key-management-service/hsm-overview.png
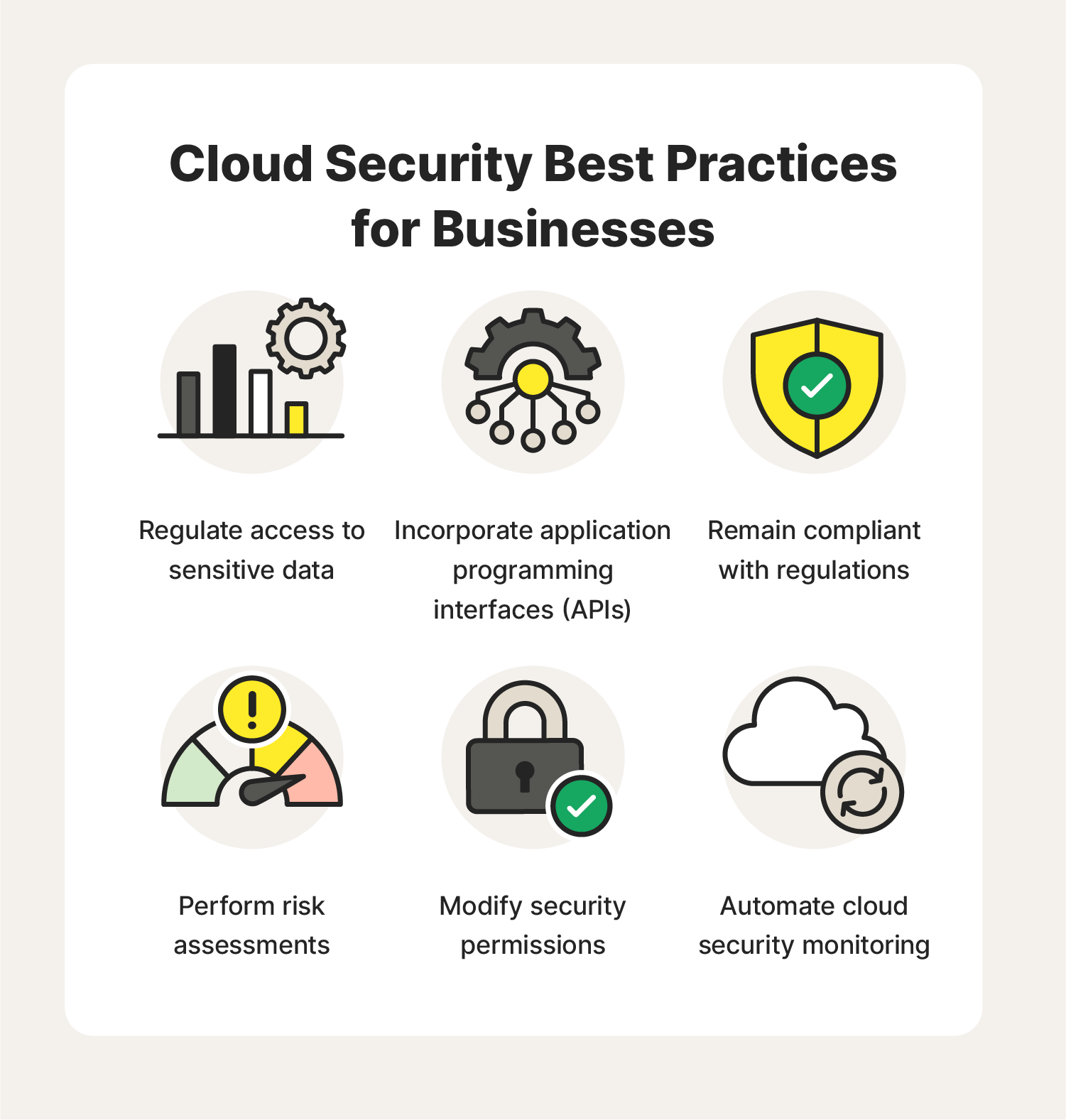
Cloud Security
https://us.norton.com/content/dam/blogs/images/norton/am/cloud-security-best-practices-for-businesses-New.png

https://security.stackexchange.com › questions
There are no decent HSM Protection Profiles yet so at the least you re going to have to read the Security Problem Definition threats and assumptions before you have an idea what the

https://security.stackexchange.com › questions
TPM Trusted Platform Module and HSM Hardware Security Module are considered as cryptoprocessor but what are the differences exactly Does one of them has
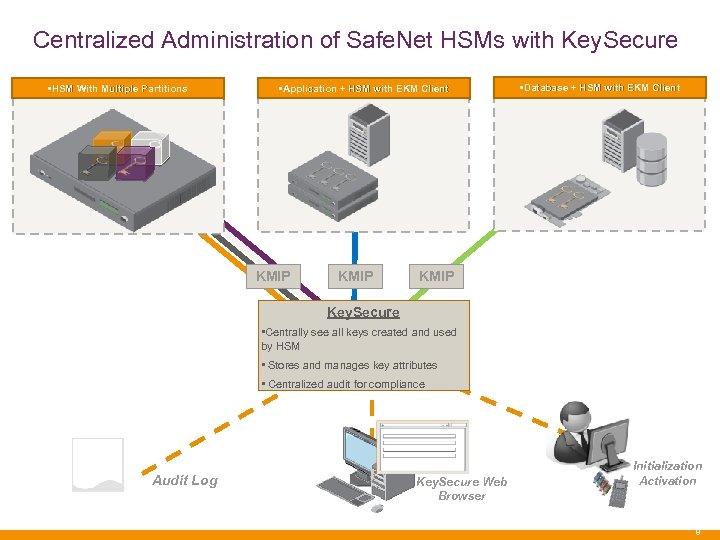
Safe Net Key Secure With Luna HSM Management

Hardware Security Module HSM Solutions Use Case Fortanix
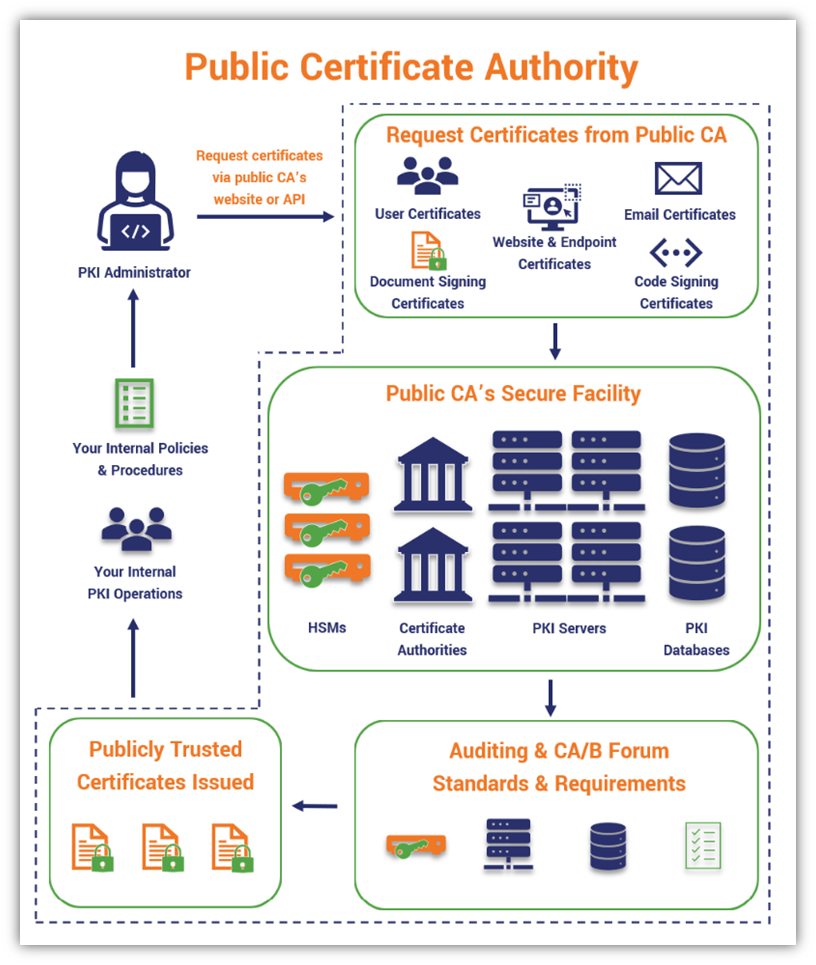
Public Certificate Authority
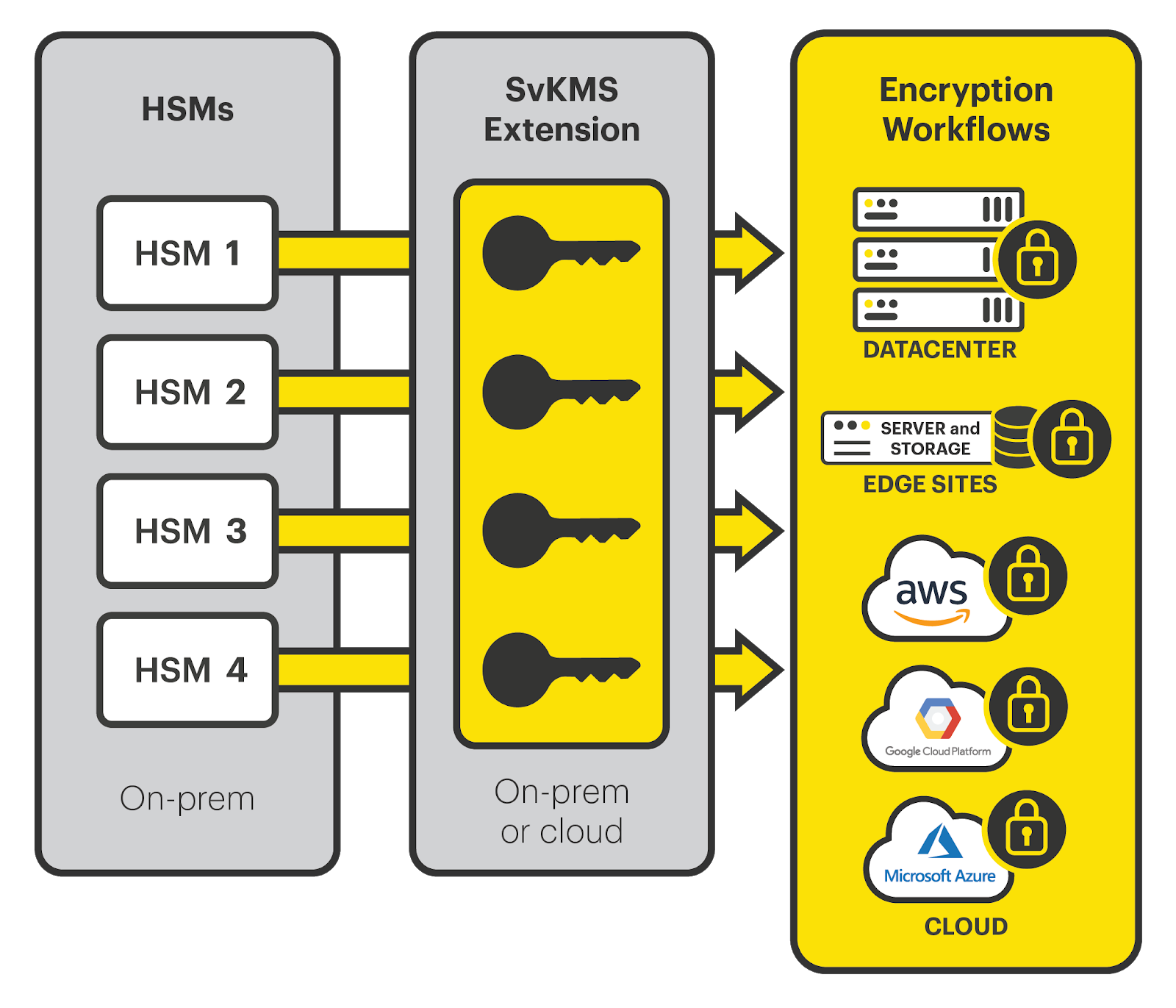
HSM Extension Flexible Key Management Features StorMagic

PCI HSM Thales
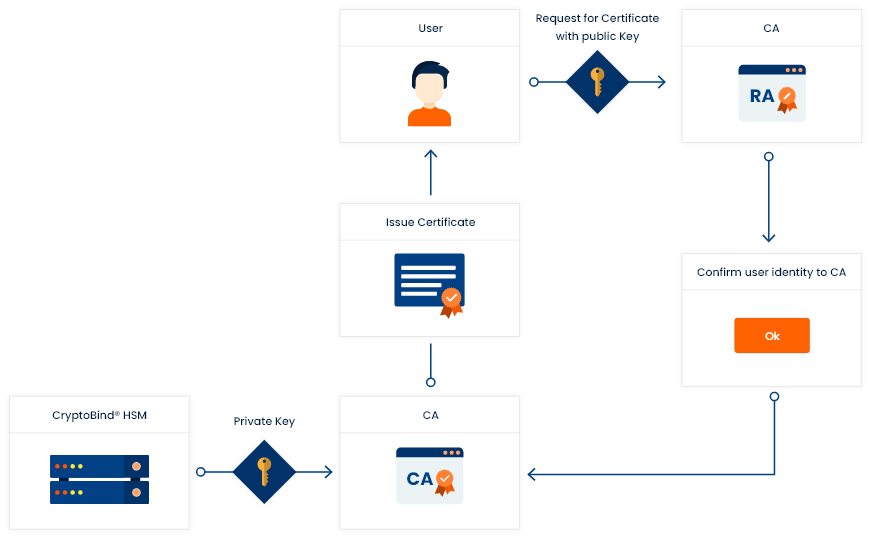
HSM PKI Use Case CryptoBind HSM HSM Vendors

HSM PKI Use Case CryptoBind HSM HSM Vendors

10 Enterprise Encryption Key Management Best Practices
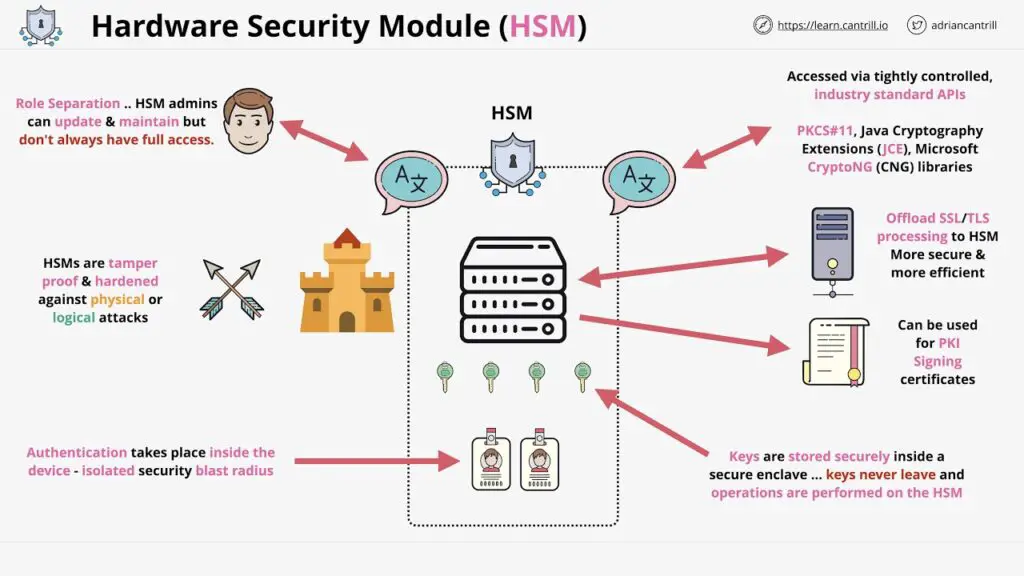
Mengenal Hsm Hardware Security Module Vrogue co
Encryption Key Management Benefits Tools Best Practices In 2024
Hsm Key Management Best Practices - [desc-14]