List Of Information Security Policies C C C STL
Python Python3 Python 1 reverse Python3 Python 0 1 Python 6
List Of Information Security Policies
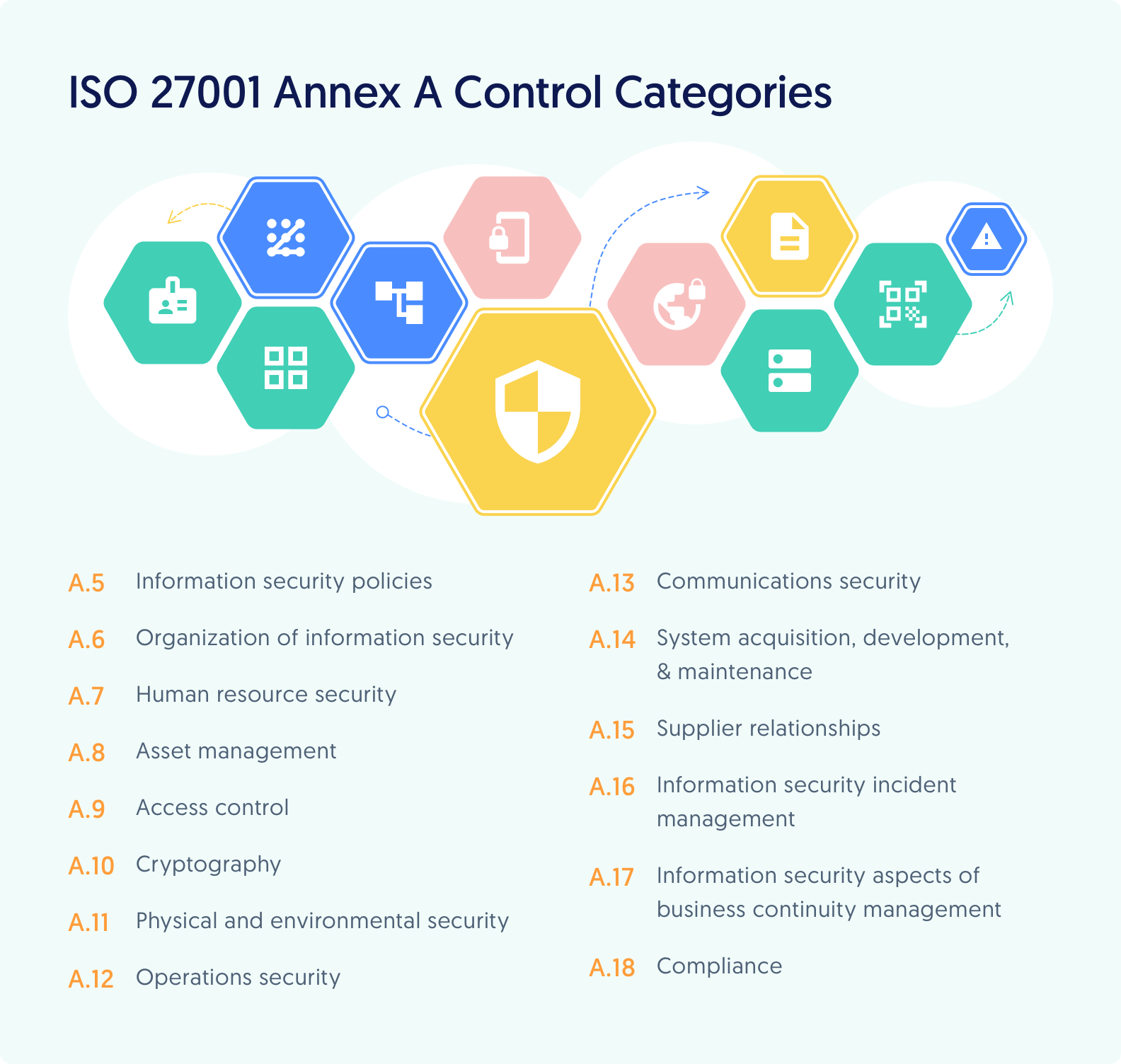
List Of Information Security Policies
https://images.prismic.io/secureframe-com/c27f2aaa-bc49-437d-81fe-20623e68d9bc_ISO+27001+controls+Updated+August+2022-+1%402x.png?auto=compress,format

Safety Policies And Procedures Safety Training And Consulting
https://safetytrainingandconsulting.ca/wp-content/uploads/2022/10/PPP.png

Musicloverwallpapersforandroid
https://s7280.pcdn.co/wp-content/uploads/2021/02/key-30.png
Python Python3 Python Java ArrayList Java ArrayList ArrayList AbstractList
Ollama Ollama CLI ollama help Large language model runner Usage ollama Python Python3 Python
More picture related to List Of Information Security Policies

Cyber Security Policy Template
https://www.cm-alliance.com/hs-fs/hubfs/CTA_Images/CTA Images 1080 x 1080/Cybersecurity Policy Template Cover.png?width=2631&name=Cybersecurity Policy Template Cover.png

CYBER SECURITY EXPO
https://cisomag.com/wp-content/uploads/2021/07/boxbanner-1.gif

Clients And Statistics UtilPoints
https://utilpoints.app/wp-content/uploads/sites/4/2024/04/history-statics-big-2.png
Python List sort Python sort Linux apt get Linux apt get Debian Ubuntu Debian Linux apt get Advanced Packaging Tool APT
[desc-10] [desc-11]
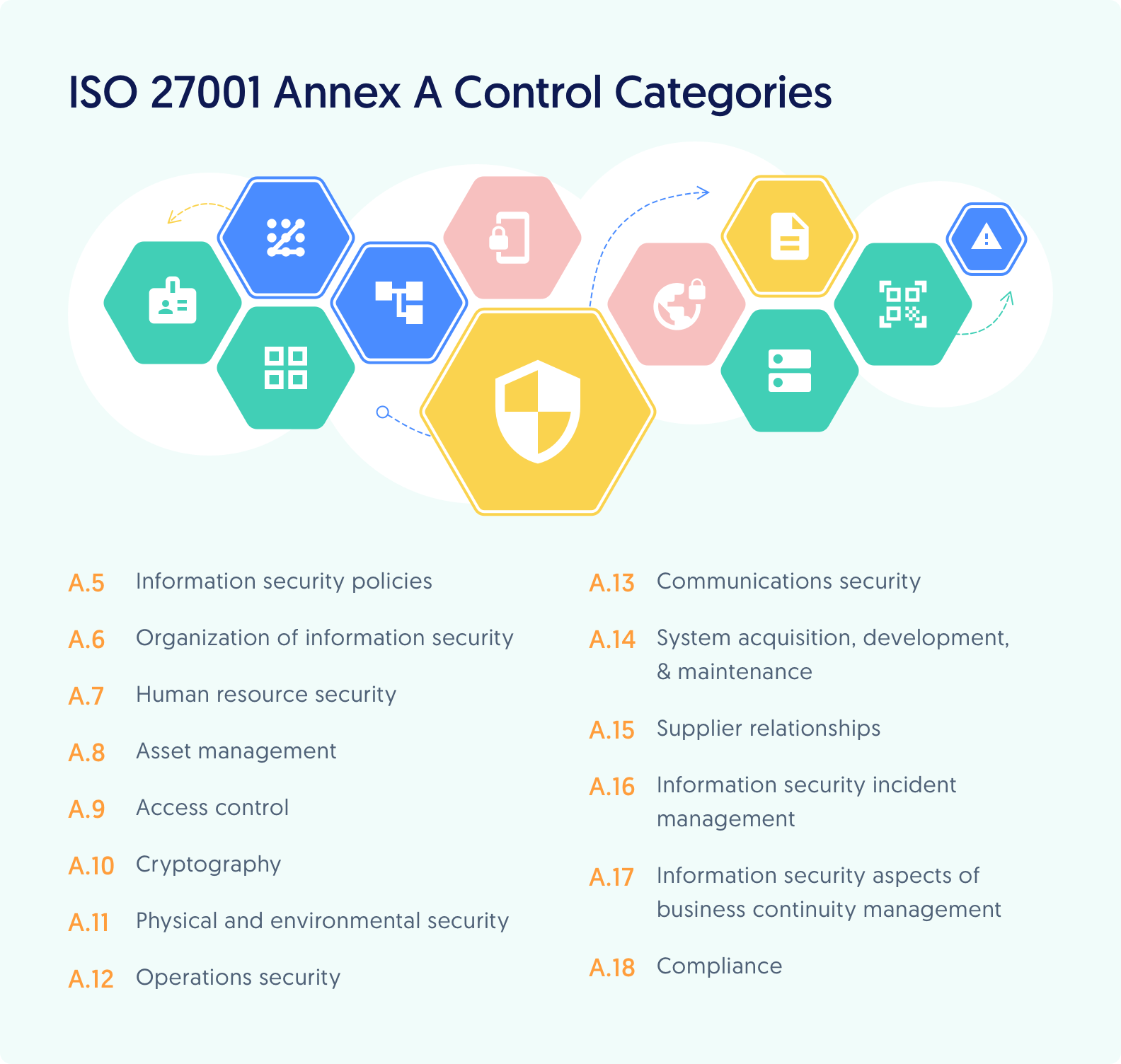
Security Policies List Of 6 Most Useful Security Policies
https://cdn.educba.com/academy/wp-content/uploads/2019/12/Security-Policies-1-768x427.jpg

Cloud Foundations Security Capabilities
https://d1.awsstatic.com/Getting Started/tutorials/cloudfoundation-security-categories.c9312f2e8dc6ae9ddc15da19bb5b57a0675ea3a9.png

https://www.runoob.com › python-reverse-list.html
Python Python3 Python 1 reverse
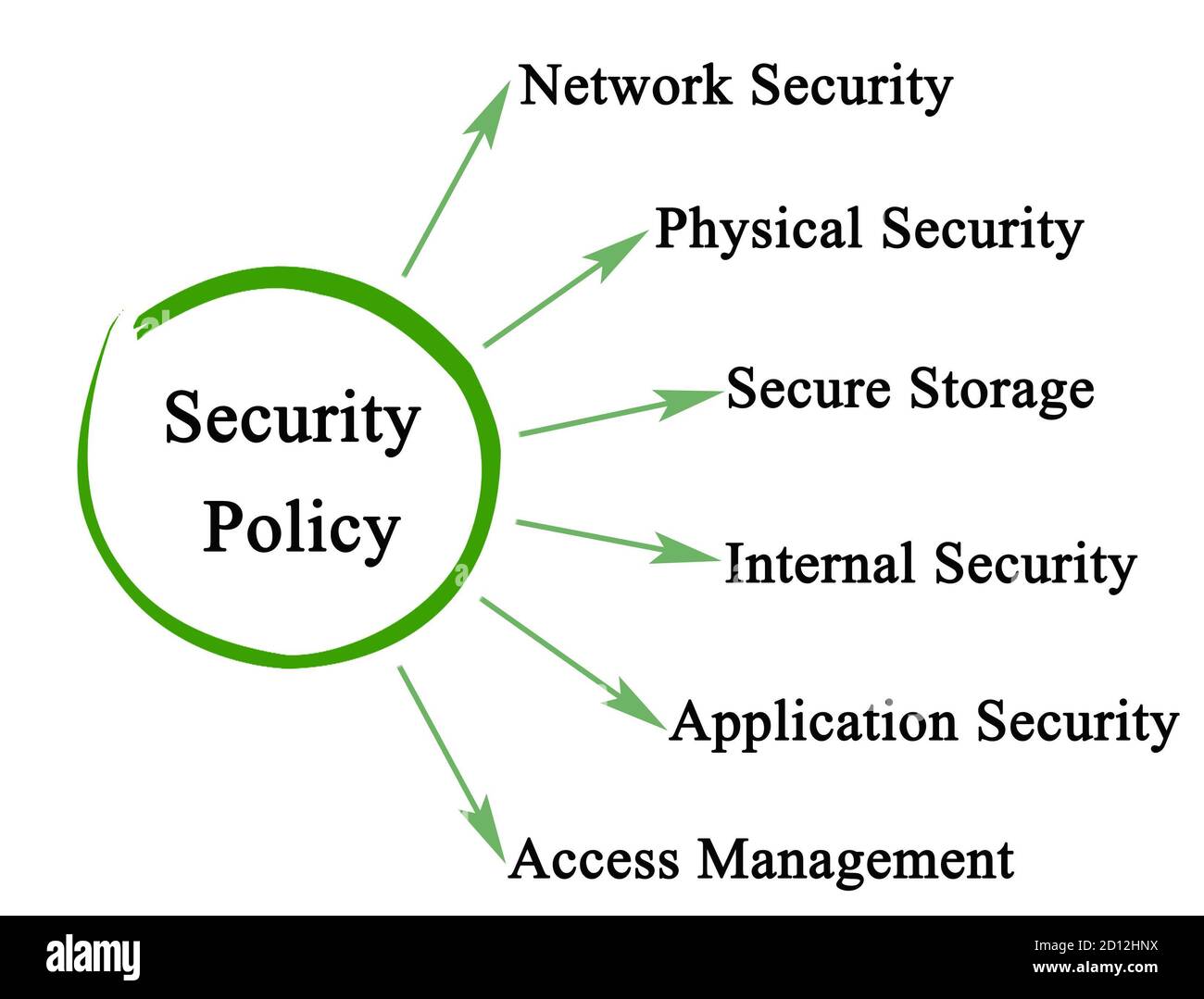
Six Types Of Security Policy Stock Photo Alamy

Security Policies List Of 6 Most Useful Security Policies
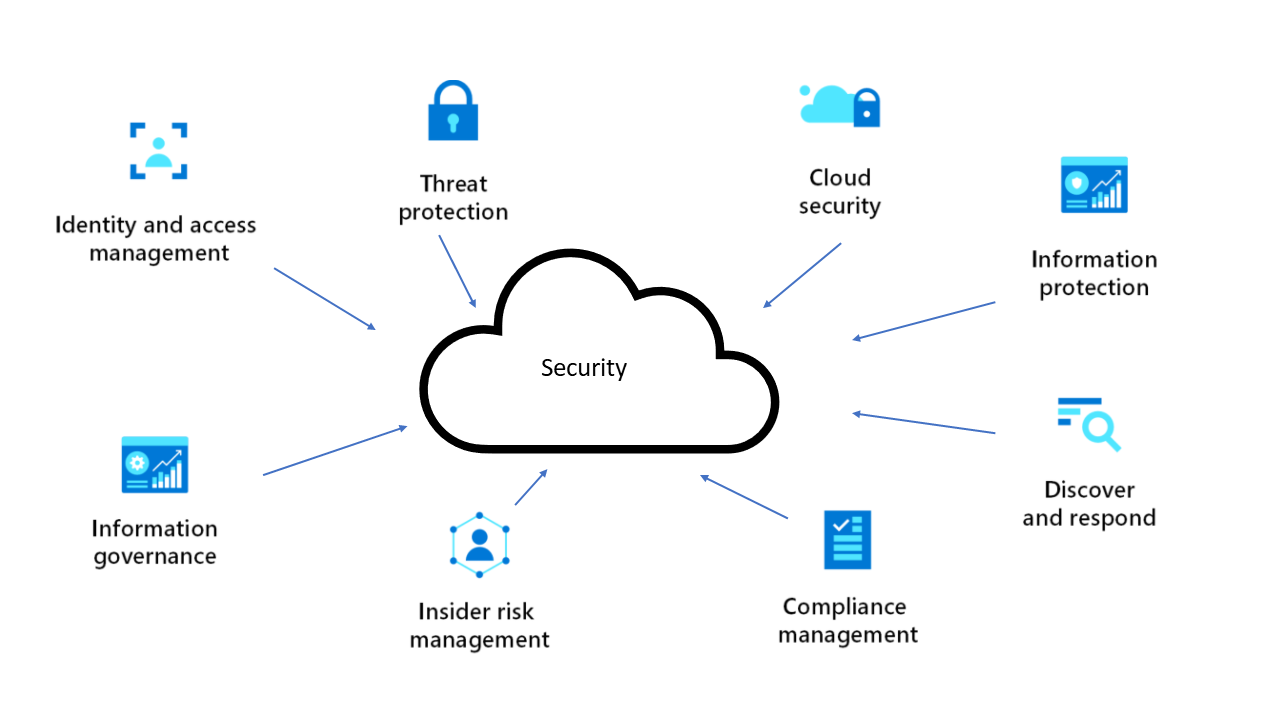
Safeguarding Your Digital Horizon
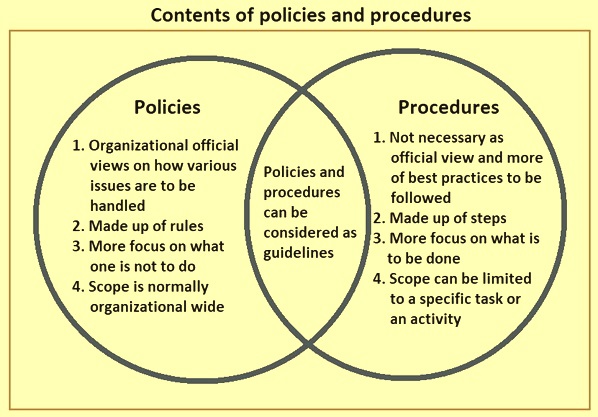
Policies And Procedures Australian Medical Association

Help With Cursor Application Log In Issue Discussion Cursor
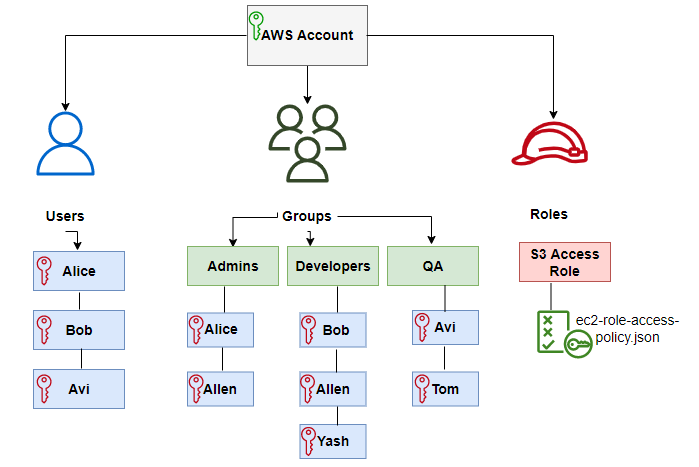
Aws IAM md At Main Gil son aws GitHub

Aws IAM md At Main Gil son aws GitHub
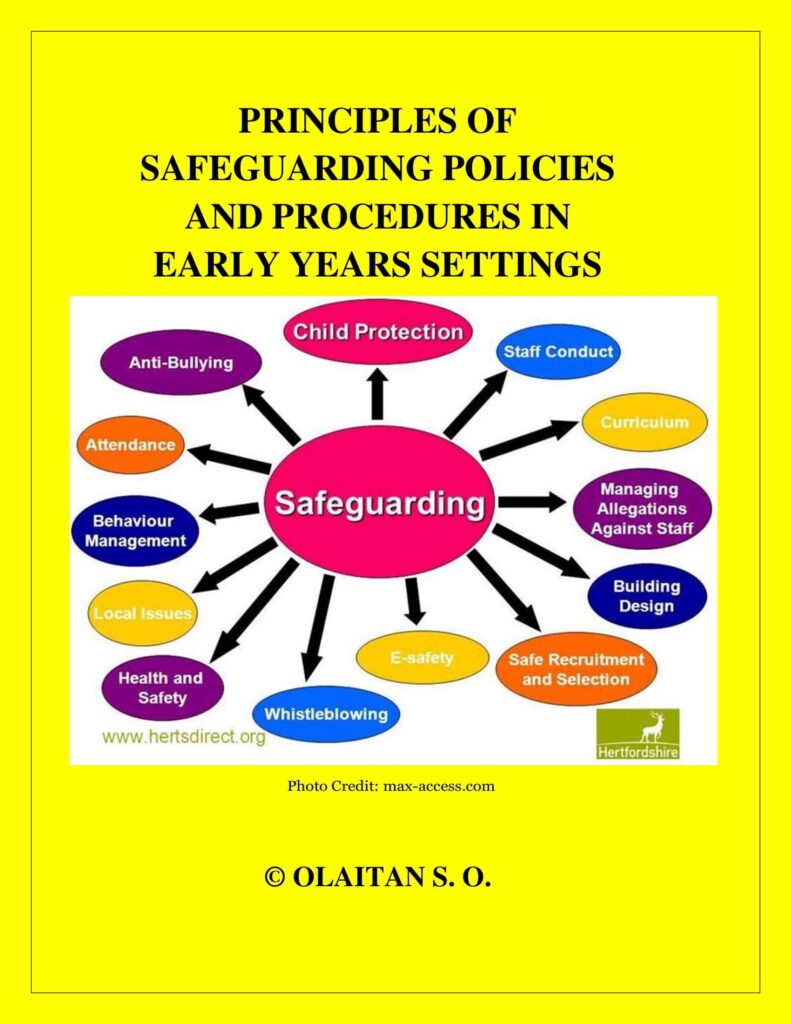
Management In Early Years Settings Management And Leadership In The

Sergey Kozlov

Written Security Plan Template
List Of Information Security Policies - [desc-12]