Security Bank Credit Card Due Date But IT security also includes physical security measures for example locks ID cards surveillance cameras required to protect buildings and devices that house data and IT
Even limited security might provide significant cost savings Those with limited AI security reported an average data breach cost of USD 4 04 million USD 400 000 less than API security is a subset of application security that prioritizes securing individual endpoints and managing access with fine grained permissions so that every data exchange is
Security Bank Credit Card Due Date
Security Bank Credit Card Due Date
https://visionplatform.ai/wp-content/uploads/2024/01/AI-security-camera.png

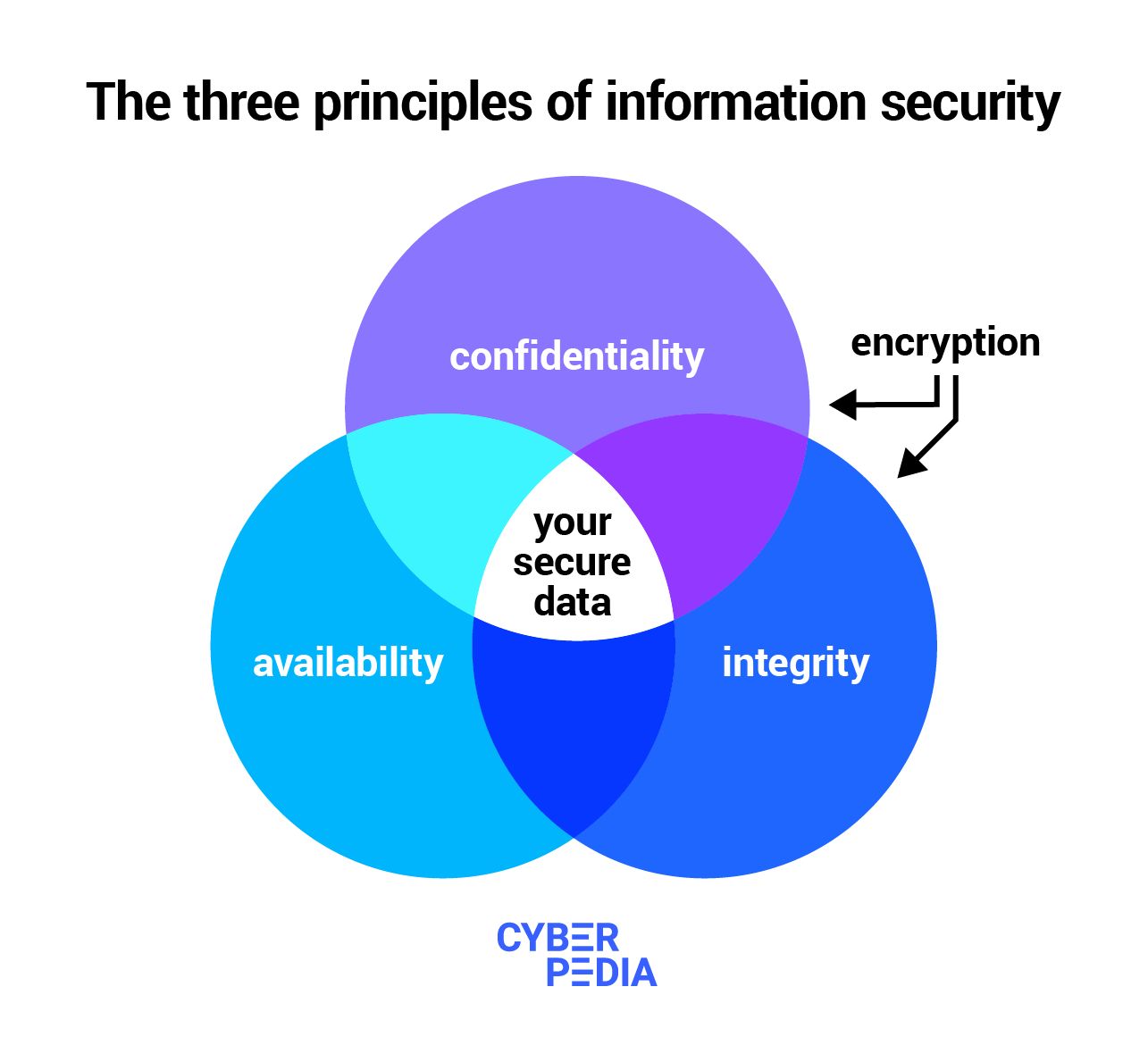
What Is Data Encryption Bitdefender Cyberpedia
https://blogapp.bitdefender.com/cyberpedia/content/images/2022/08/Principles-of-information-security.jpg

Best Cyber Security Awareness Tips InfosecTrain
https://www.infosectrain.com/wp-content/uploads/2022/10/Best-Cybersecurity-Awareness-Tips-1.jpg
Chief information security officers CISOs who oversee information security efforts have become a fixture of corporate C suites Demand is rising for information security analysts A security solution is only as strong as its weakest link Therefore you should consider multiple layers of security controls also known as a defense in depth strategy to
SOAR technology arose as a consolidation of three earlier security tools According to Gartner which first coined the term SOAR in 2015 SOAR platforms combine the functions of security Database software security Always use the latest version of your database management software and apply all patches when they are issued Application and web server security
More picture related to Security Bank Credit Card Due Date
![]()
Secure Icon Png
https://static.vecteezy.com/system/resources/previews/010/056/214/original/security-icon-anti-virus-sign-design-free-png.png
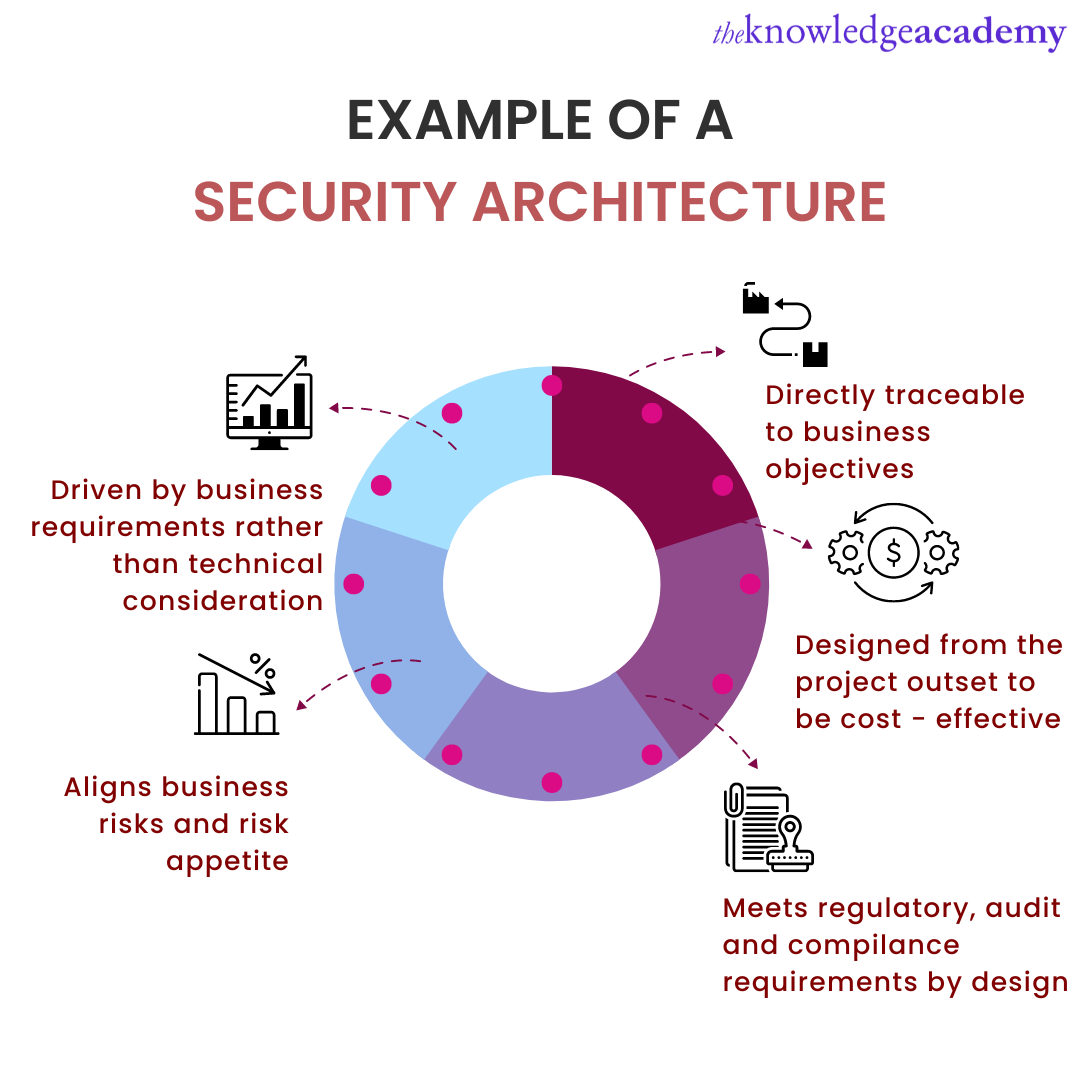
Cyber Security Architecture And Its Benefits
https://www.theknowledgeacademy.com/_files/images/Example_of_a_Security_Architecture.png

Security Concept Secure Information 3D Render Personal Data 11015345 PNG
https://static.vecteezy.com/system/resources/previews/011/015/345/original/security-concept-secure-information-3d-render-personal-data-free-png.png
Static application security testing SAST This AST uses solutions that analyze application source code without executing the program SAST can identify potential security A comprehensive data security strategy incorporates people processes and technologies Establishing appropriate controls and policies is as much a question of organizational culture
[desc-10] [desc-11]
.png)
Importance Of Cyber Security For Business In 2023
https://www.theknowledgeacademy.com/_files/images/Importance_of_Cyber_Security_in_Business(1).png
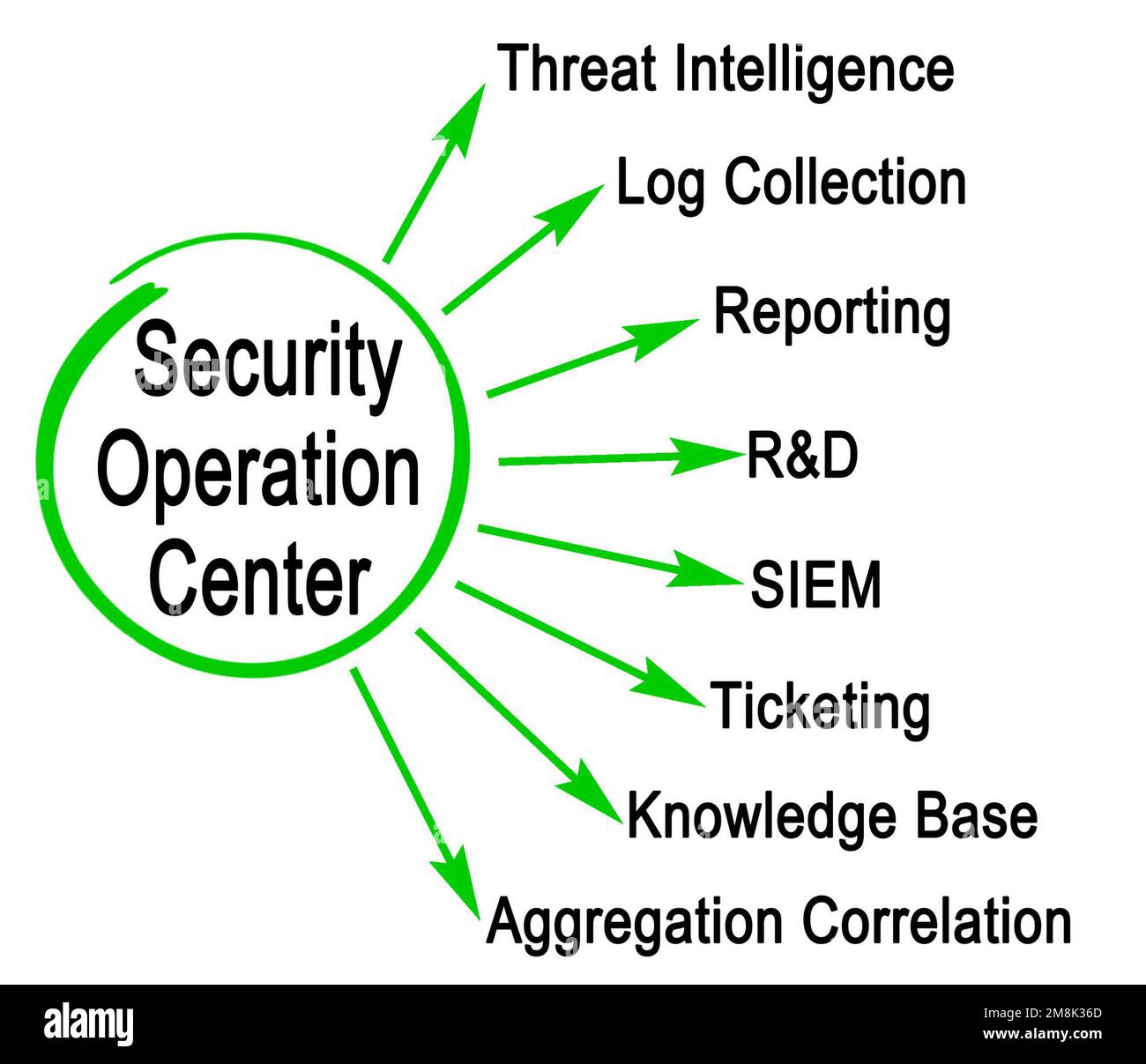
Functions Of Security Operation Center Stock Photo Alamy
https://c8.alamy.com/comp/2M8K36D/functions-of-security-operation-center-2M8K36D.jpg
https://www.ibm.com › think › topics › it-security
But IT security also includes physical security measures for example locks ID cards surveillance cameras required to protect buildings and devices that house data and IT
https://www.ibm.com › think › topics › ai-security
Even limited security might provide significant cost savings Those with limited AI security reported an average data breach cost of USD 4 04 million USD 400 000 less than

Eight Tips Parents Can Teach Their Kids About Cyber Security Sherwood
.png)
Importance Of Cyber Security For Business In 2023
Security Services Logo Vector

Cyber Security RoadMap In 2023 Learn Computer Science

Protect Your Business With Technomine Proactive Security Measures

CPCSC Archives Cyber Security Canada

CPCSC Archives Cyber Security Canada
Cyber Security Icon Vector Security Logo Artificial Intelligence
Document

Cctv Security Company Logo
Security Bank Credit Card Due Date - A security solution is only as strong as its weakest link Therefore you should consider multiple layers of security controls also known as a defense in depth strategy to