What Is Computer Security Threats And Its Types On your computer go to gmail Enter your Google Account email address or phone number and password If information is already filled in and you need to sign in to a different account
How to install Chrome Important Before you download you can check if Chrome supports your operating system and other system requirements If you re new to Google Drive this article will help you get started by covering the most important and useful things you can do from learning how to use Drive and keeping your files organized
What Is Computer Security Threats And Its Types
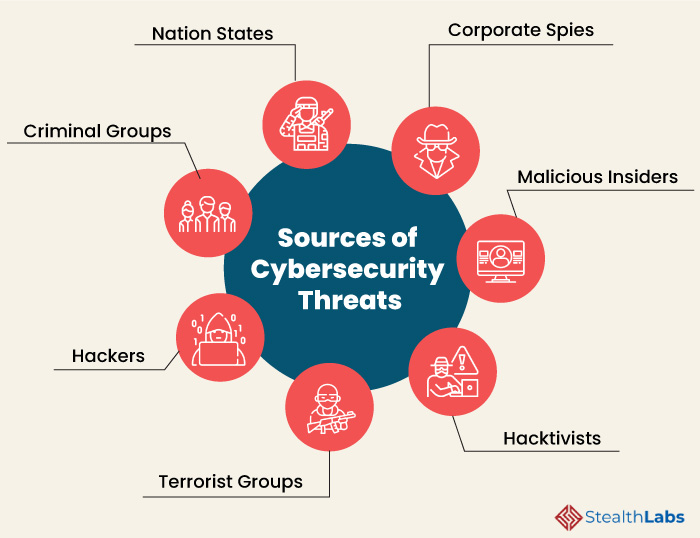
What Is Computer Security Threats And Its Types
https://cdn1.byjus.com/wp-content/uploads/2021/07/cybersecurity-700x538.png

Common Cyber Threats Computer Science Programming Learn Computer
https://i.pinimg.com/originals/e0/6d/d0/e06dd08592634692dca4cbbe76f6bb4d.jpg

Threats Stock Illustrations 9 698 Threats Stock Illustrations
https://thumbs.dreamstime.com/b/data-security-threats-infographics-information-r-risks-concept-technology-vector-illustration-black-neon-blue-color-background-106746653.jpg
After you add contacts to your Android device you can make changes or delete them Contacts saved to your Google Account will sync with Google Contacts and all your Android devices Inloggen bij Gmail Als je Gmail wilt openen kun je inloggen vanaf een computer of je account toevoegen aan de Gmail app op je telefoon of tablet Zodra je bent ingelogd open je je inbox
ffnen Sie Gmail auf Ihrem Computer Geben Sie die E Mail Adresse oder die Telefonnummer und das Passwort Ihres Google Kontos ein Falls Informationen vorausgef llt sind Sie sich Visit the Learning Center Using Google products like Google Docs at work or school Try powerful tips tutorials and templates Learn to work on Office files without installing Office
More picture related to What Is Computer Security Threats And Its Types

Cyber Attack Cheat Sheet Infographic
https://infographicjournal.com/wp-content/uploads/2020/04/types-of-cyberattacks-feat.jpg

Insider Threats Risks Identification And Prevention
https://threatcop.com/blog/wp-content/uploads/2021/12/Insider-Threats.png
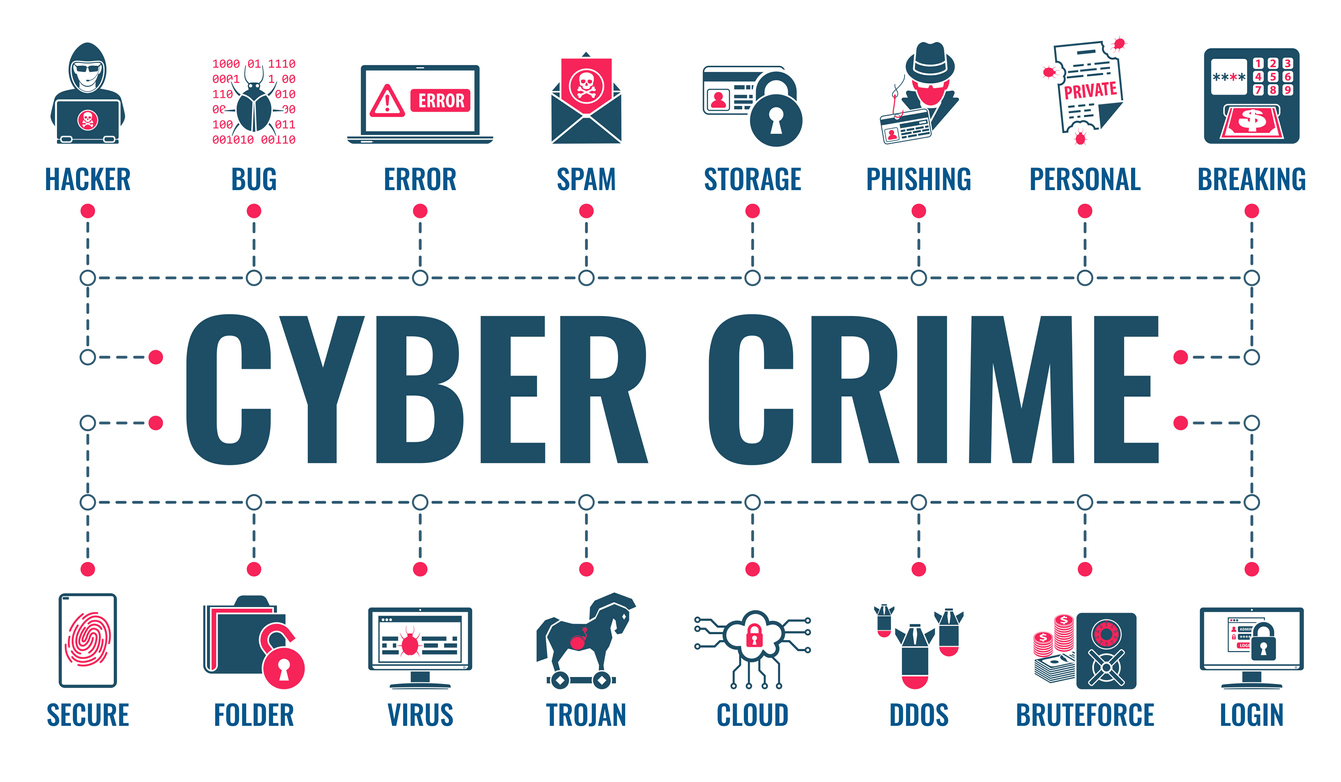
Cybercrime Attacks The 5 Most Common Types WP Farm
https://www.wpfarm.com/wp-content/uploads/iStock-1201162639.jpg
On your computer you can upload from drive google or your desktop You can upload files into private or shared folders On your computer go to drive google At the top left click Google Duo and Google Meet have been combined into a new Meet app for video calling and meetings You can access your meetings in the new Meet app
[desc-10] [desc-11]

Things You Need To Know About Cyber Attacks Threats Risks Ecosystm
http://blog.ecosystm360.com/wp-content/uploads/2019/03/Types-of-cyber-attacks.jpg
.png)
What Are The Different Types Of Cyber Security
https://www.theknowledgeacademy.com/_files/images/Types_of_Cyber_Security(1).png
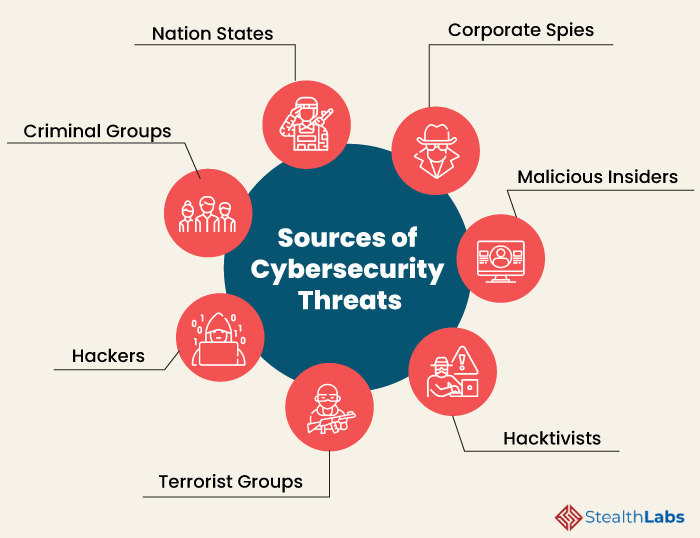
https://support.google.com › mail › answer
On your computer go to gmail Enter your Google Account email address or phone number and password If information is already filled in and you need to sign in to a different account

https://support.google.com › chrome › answer › download-and-install-go…
How to install Chrome Important Before you download you can check if Chrome supports your operating system and other system requirements
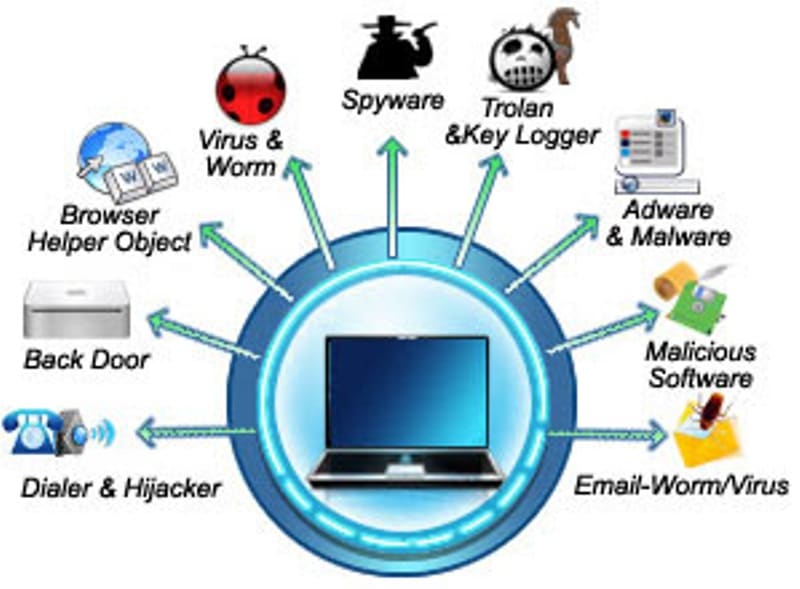
How To Prevent The Unethical Uses Of Computers

Things You Need To Know About Cyber Attacks Threats Risks Ecosystm
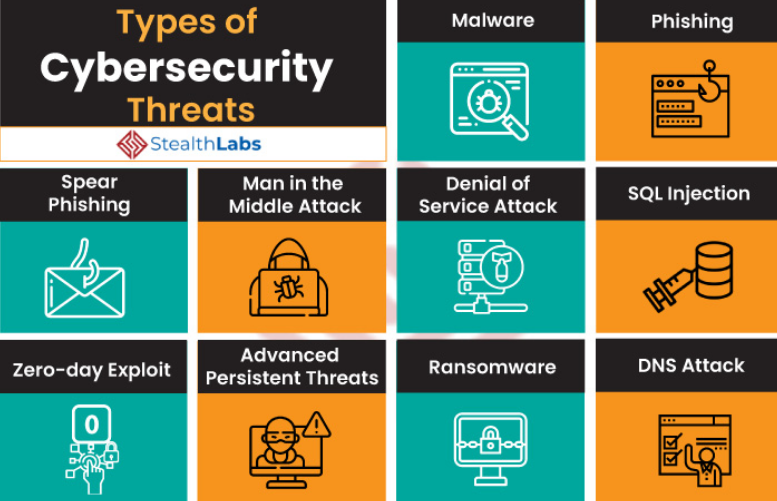
Cyber Security Threats And Attacks AIESEC Help Center
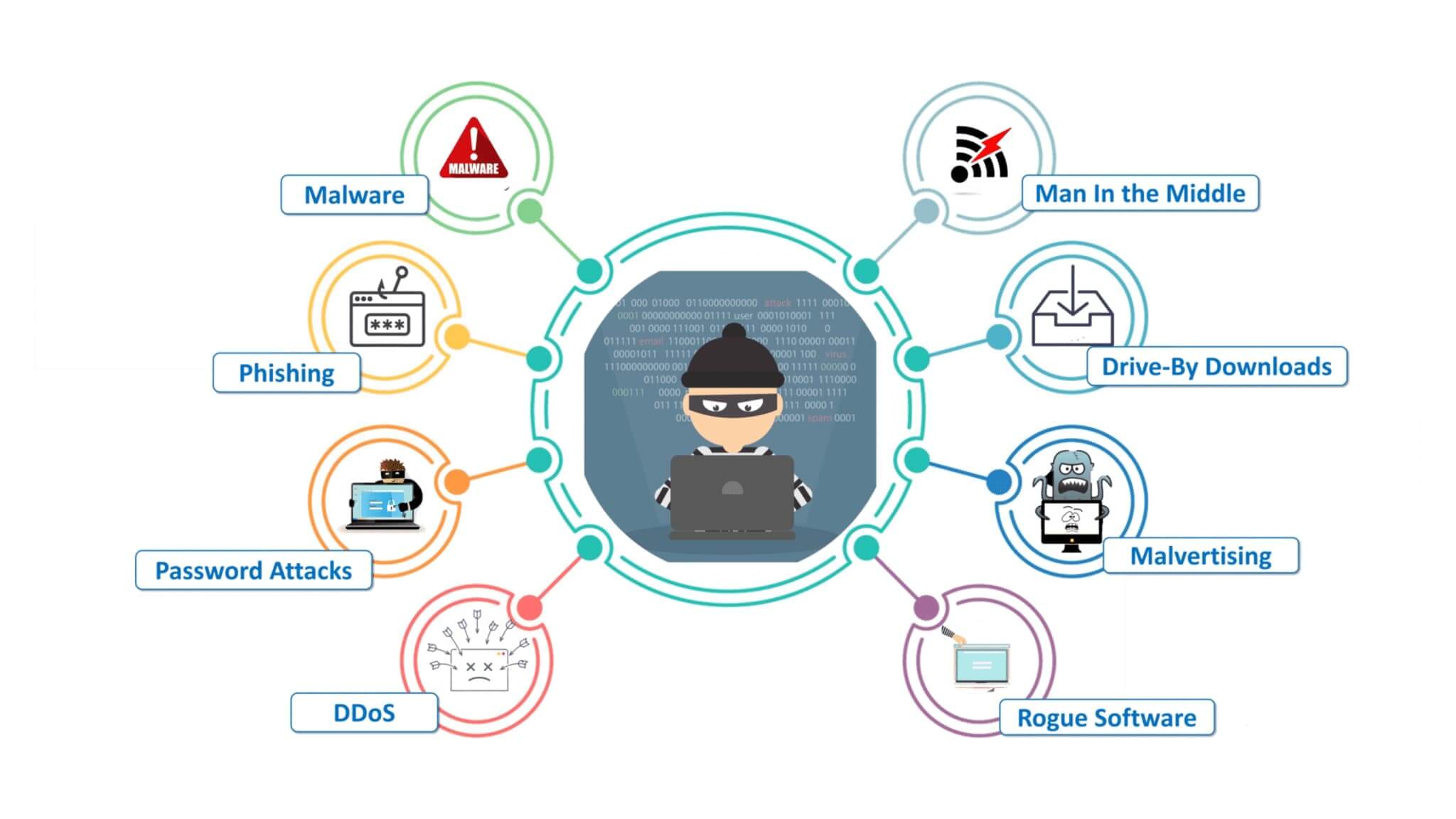
Advantages Disadvantages Of Learning Ethical Hacking

Top 8 Network Security Threats Best Practices

Combating Seven Common Threat Techniques In 2018 IT Security Guru

Combating Seven Common Threat Techniques In 2018 IT Security Guru
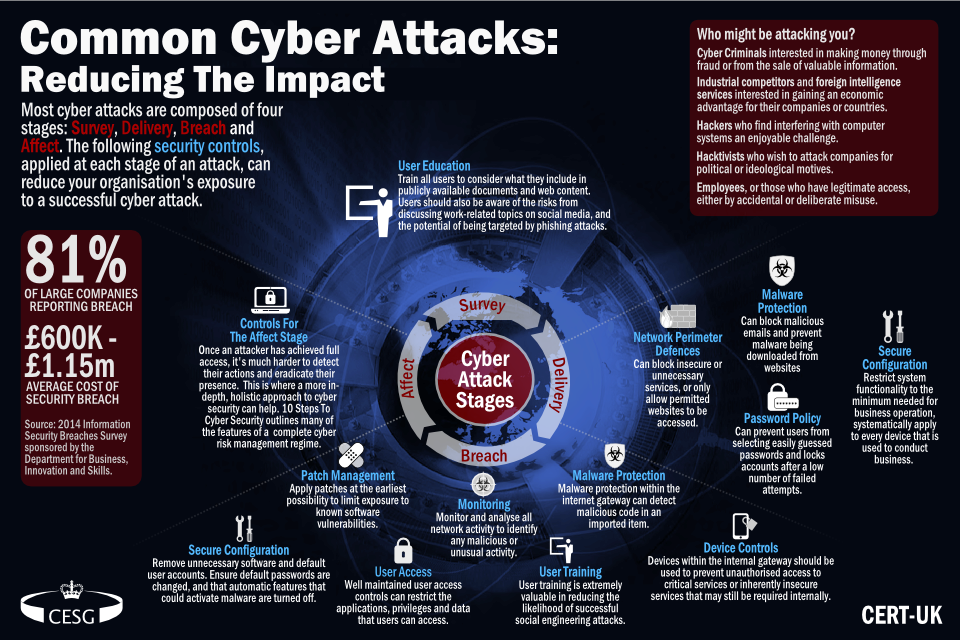
What Does The Cac Contain Cyber Awareness

TechBytes Blog

Types Of Cybersecurity Attacks And How To Prevent Them
What Is Computer Security Threats And Its Types - Inloggen bij Gmail Als je Gmail wilt openen kun je inloggen vanaf een computer of je account toevoegen aan de Gmail app op je telefoon of tablet Zodra je bent ingelogd open je je inbox