What Is Security Attacks And Its Types What is tokenization In data security tokenization is the process of converting sensitive data into a nonsensitive digital replacement called a token that maps back to the
IT security protects an organization s computer systems networks an digital data from unauthorized access data breaches cyberattacks and other malicious activity La seguridad inform tica protege los sistemas inform ticos las redes y los datos digitales de una organizaci n contra el acceso no autorizado las filtraciones de datos los ataques cibern ticos
What Is Security Attacks And Its Types

What Is Security Attacks And Its Types
https://pbs.twimg.com/media/Fltz1VMXgAILwmV.png

Cyber Threats
https://d2ds8yldqp7gxv.cloudfront.net/Blog+Explanatory+Images/Top+Cybersecurity+Threats+1.webp

Social Engineering Attacks Anybody Could Fall Victim To Help Net Security
https://img.helpnetsecurity.com/wp-content/uploads/2022/10/17162548/social_engineering_attacks.jpg
Information security InfoSec is the protection of important information against unauthorized access disclosure use alteration or disruption API security is a set of practices and procedures that protect application programming interfaces APIs and the data they transmit from misuse malicious bot attacks
Most of us think of cybersecurity as a purely digital affair but cyberattacks can actually begin right here in the physical world Don t want to fork over 30 for a one year subscription to Windows 10 Extended Security Updates Microsoft is offering a couple of ways to avoid the fee But there is a catch
More picture related to What Is Security Attacks And Its Types

Dos Attack
https://us.norton.com/content/dam/blogs/images/norton/am/ddos-attacks-explained11.png

Phishing Attacks
https://wesecureapp.com/wp-content/uploads/2022/09/Phishing-Attacks.png

Are You Cyber Secured Be Aware Of Potential Cyber Attacks ECS
https://www.ecsbiztech.com/wp-content/uploads/2020/09/Section-2.png
DevOps security or DevSecOps is a developmental approach where security processes are prioritized and executed during each stage of the software development ZDNET news and advice keep professionals prepared to embrace innovation and ready to build a better future
[desc-10] [desc-11]
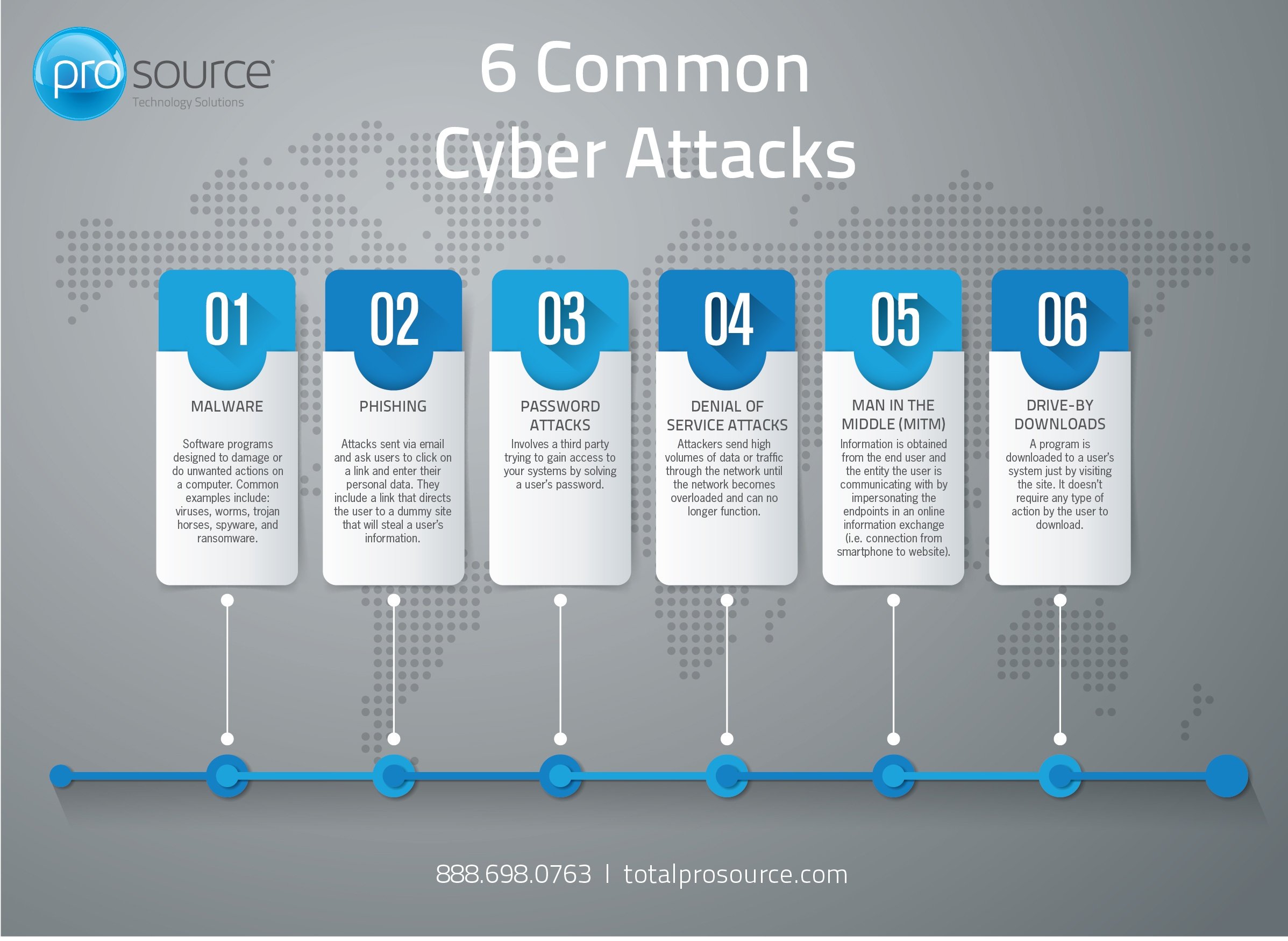
6 Common Types Of Cyber Attacks
https://cdn2.hubspot.net/hubfs/838527/6 Common Types of Cyber Attacks Infogrpahic.jpg

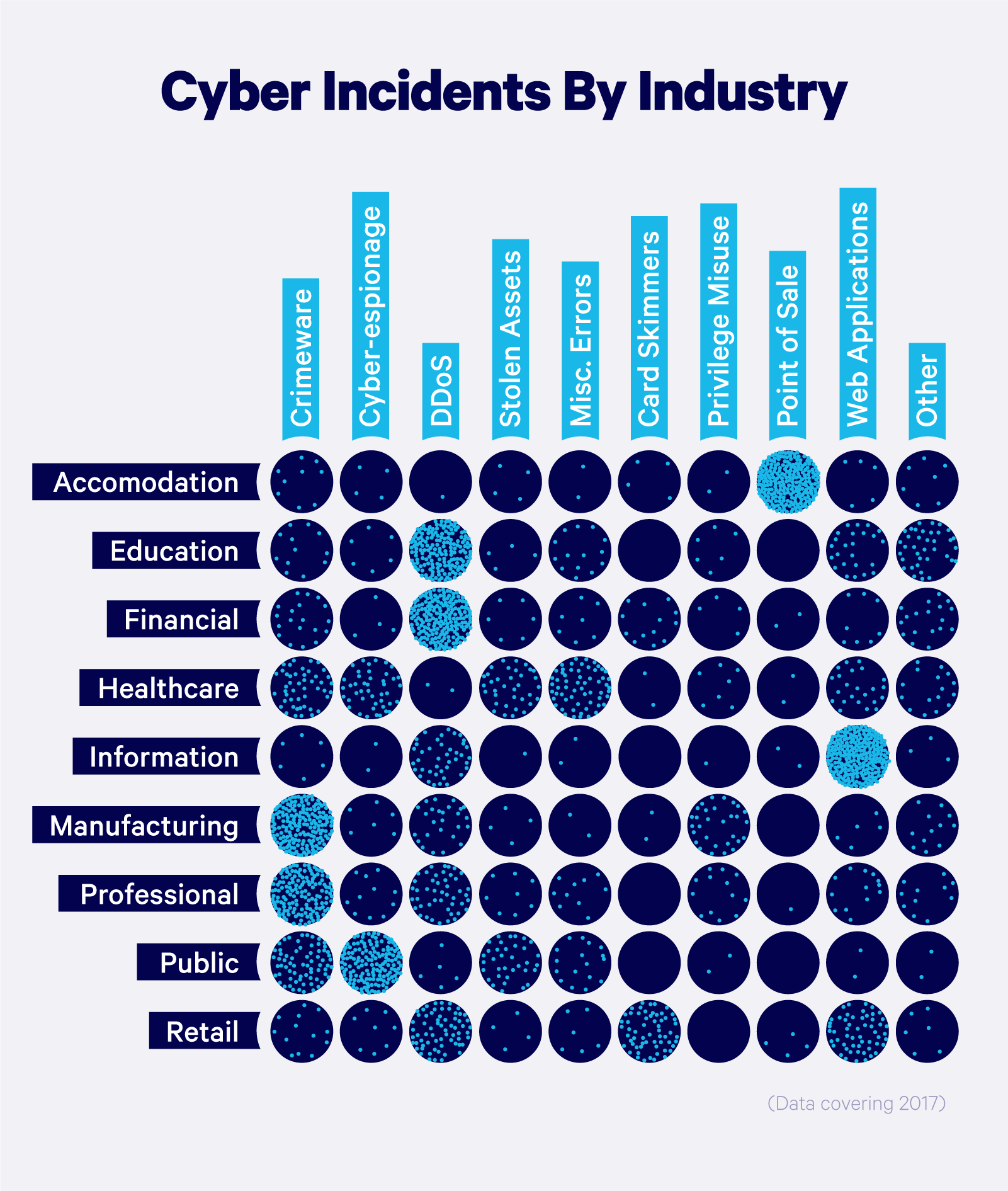
Recent Breaches 2024 Elvira Celestina
https://static.wixstatic.com/media/87060e_6b0f1db0351541dabb8ffce8e12d046b~mv2.png/v1/fill/w_980,h_980,al_c,q_90,usm_0.66_1.00_0.01,enc_auto/87060e_6b0f1db0351541dabb8ffce8e12d046b~mv2.png

https://www.ibm.com › think › topics › tokenization
What is tokenization In data security tokenization is the process of converting sensitive data into a nonsensitive digital replacement called a token that maps back to the
https://www.ibm.com › think › topics › it-security
IT security protects an organization s computer systems networks an digital data from unauthorized access data breaches cyberattacks and other malicious activity

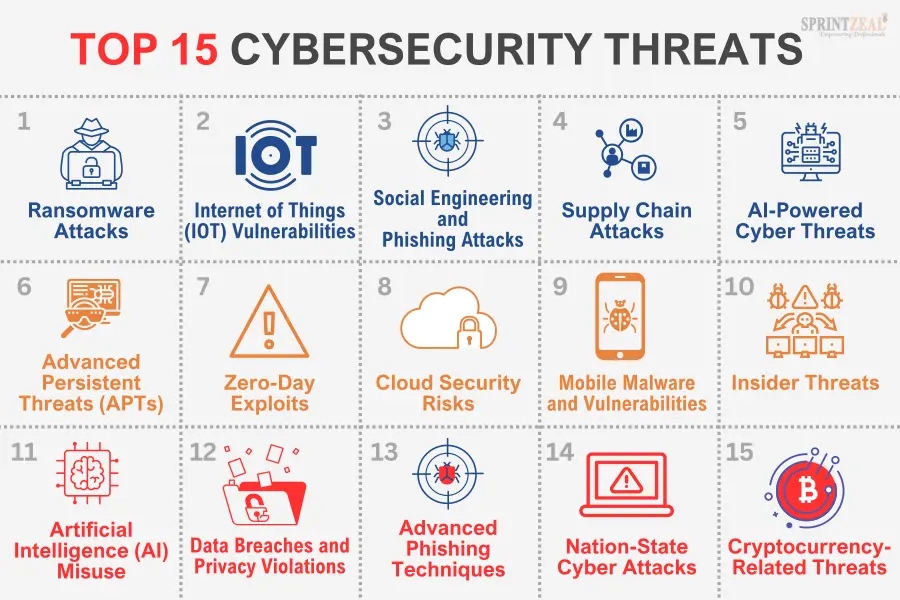
Cyber Attack Statistics

6 Common Types Of Cyber Attacks
The Biggest Cyber Attacks In History
Report 2022 Must Know Cyber Attack Statistics And Trends I AML
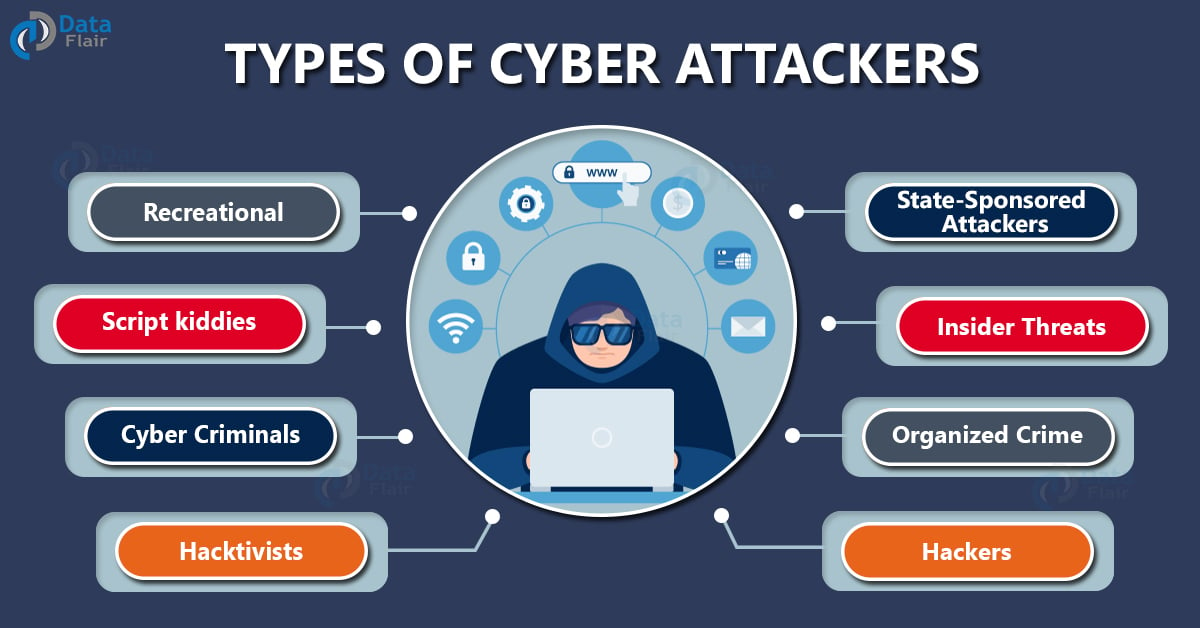
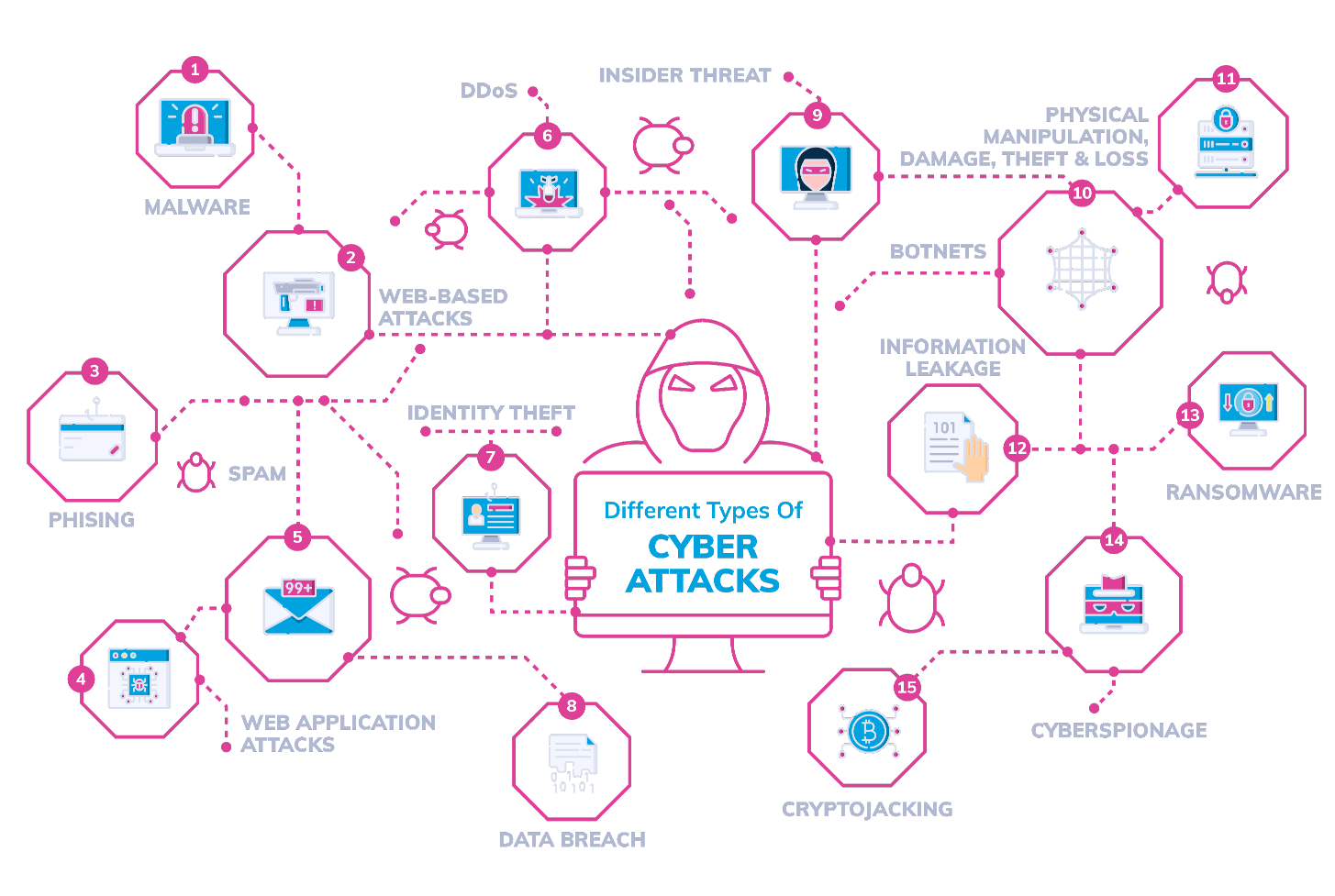
Types Of Cyber Crime

OSI Model 7 Layers Common Security Attacks Stackscale

OSI Model 7 Layers Common Security Attacks Stackscale
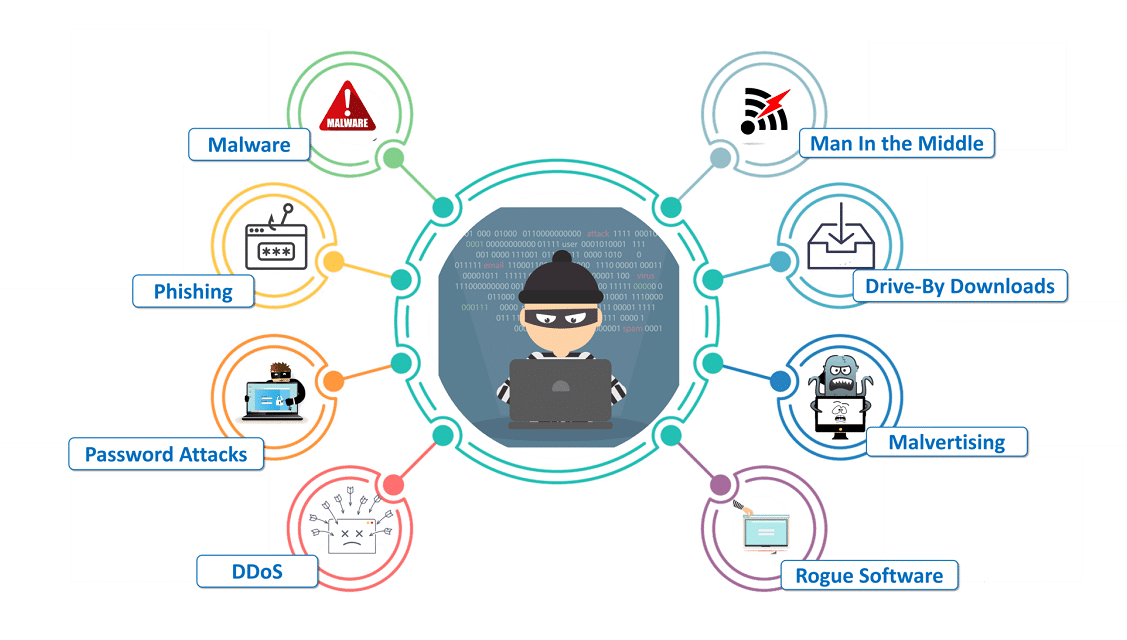
Web Application Security Best Practices EiqnetWorkS

TYPES OF ARP IP With Ease
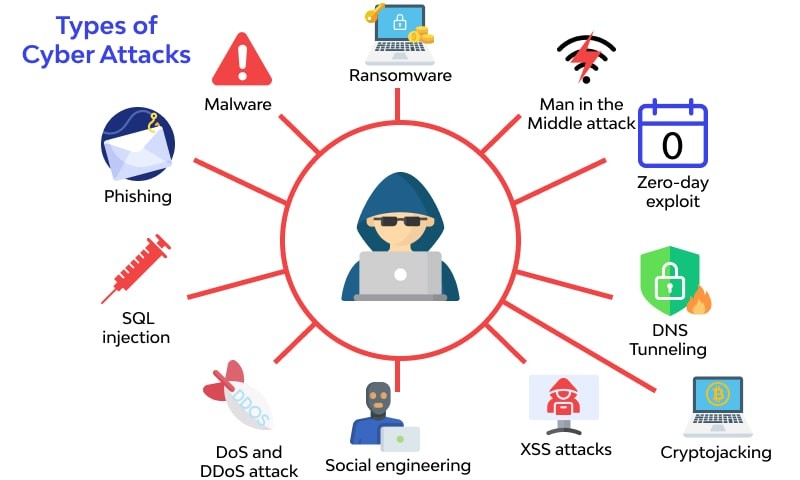
Cyber Security Attacks
What Is Security Attacks And Its Types - [desc-13]