What Is Security Tag On Clothes What is information security Information security InfoSec is the protection of important information against unauthorized access disclosure use alteration or disruption It
Experience an integrated media property for tech workers latest news explainers and market insights to help stay ahead of the curve What is data security Data security is the practice of protecting digital information from unauthorized access corruption or theft throughout its entire lifecycle This concept
What Is Security Tag On Clothes

What Is Security Tag On Clothes
https://i.ytimg.com/vi/XQbNMxkkwGE/maxresdefault.jpg

How To Defeat The Red Target Security Tag On Clothing YouTube
https://i.ytimg.com/vi/1v8xRXFrHis/maxresdefault.jpg

Simplest Way To Remove Security Tag From Your Clothes How To Remove
https://i.ytimg.com/vi/opoA9rpvpn8/maxresdefault.jpg
News from the Gmail team Welcome to the new integrated Gmail Your new home where email messages tasks and calls come together Create a space Start a conversation with friends What is a cybersecurity risk assessment A cybersecurity risk assessment is a process used to identify evaluate and prioritize potential threats and vulnerabilities to an
What is IT security IT security which is short for information technology security is the practice of protecting an organization s IT assets computer systems networks digital A SOC usually pronounced sock and sometimes called an information security operations center or ISOC is an in house or outsourced team of IT security professionals dedicated to
More picture related to What Is Security Tag On Clothes

Removing Clothing Security Tag In A Rush Security Tag On Suit
https://i.ytimg.com/vi/rfaikKCRzlc/maxresdefault.jpg

How To Remove Target Security Tags In 1 Minute Without Ruining Your
https://i.ytimg.com/vi/uctzBTF-2wA/maxresdefault.jpg

How To Remove Target Red Security Tag From Clothing Garment At Home
https://i.ytimg.com/vi/NscUdIILaLQ/maxresdefault.jpg
Get the Cost of a Data Breach Report 2024 for the most up to date insights into the evolving cybersecurity threat landscape SOAR for security orchestration automation and response is a software solution that enables security teams to integrate and coordinate separate security tools automate repetitive tasks
[desc-10] [desc-11]

How To Remove Security Tag Of Shopping Mall Find Out What Is Inside
https://i.ytimg.com/vi/hCFitoarV6M/maxresdefault.jpg

Resources Bleachcyber
https://bleachcyber.com/wp-content/uploads/2023/07/Bleach-Logo-White.png

https://www.ibm.com › think › topics › information-security
What is information security Information security InfoSec is the protection of important information against unauthorized access disclosure use alteration or disruption It

https://www.ibm.com › think
Experience an integrated media property for tech workers latest news explainers and market insights to help stay ahead of the curve
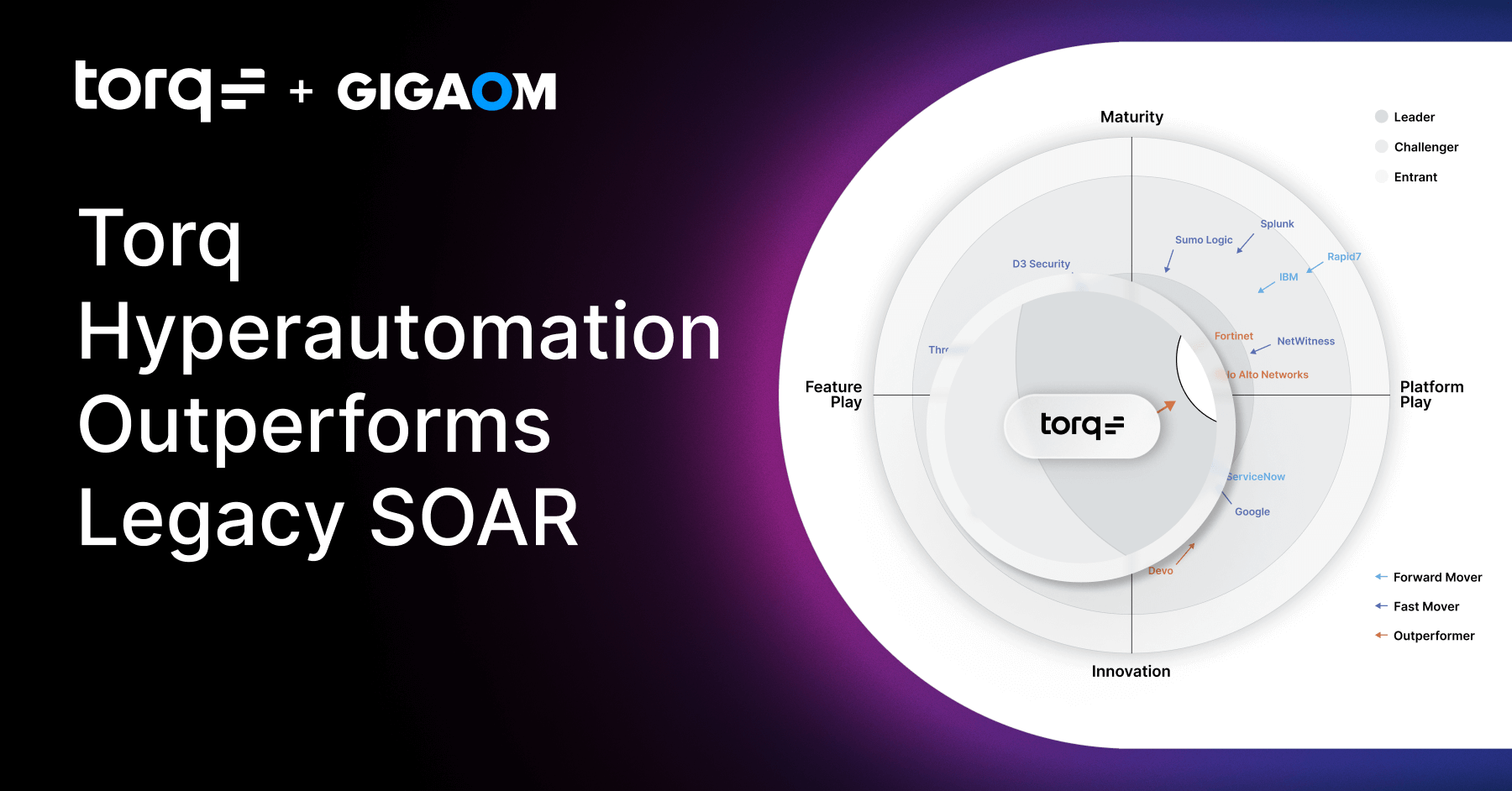
GigaOM Report Torq Hyperautomation Outperforms Legacy SOAR

How To Remove Security Tag Of Shopping Mall Find Out What Is Inside

Arkaprava Tripathi Zscaler Blog

Sree Koratala Zscaler Blog

NgOlfe Blog

Security Risk Assessment Idensic

Security Risk Assessment Idensic

Escape The SecOps Black Hole Torq

Security Services Ansec

Yesenia Barajas Zscaler Blog
What Is Security Tag On Clothes - What is a cybersecurity risk assessment A cybersecurity risk assessment is a process used to identify evaluate and prioritize potential threats and vulnerabilities to an