What Is Security Threat Assessment Learn what a threat assessment is and how it is performed in cybersecurity Find out the difference between threat assessment and vulnerability assessment and see an example of a threat assessment process
The threat assessment is one of the most efficient tools security teams use to recognize and respond to physical security threats or information technology risks One of the most significant benefits of threat vulnerability A security threat assessment is the process by which threats to an organization s information systems and data are described determined and broadened This is supplemented by capabilities for identifying and prioritizing
What Is Security Threat Assessment

What Is Security Threat Assessment
https://www.ferrarisinvestigations.com/wp-content/uploads/Security-Assessment.jpg

Quantitative Metrics And Risk Assessment The Three Tenets Model Of
https://i.pinimg.com/originals/66/dd/a5/66dda5d255428a8d18c1f407ef0a62f7.png

Threat Assessment B4Secure
https://www.b4secure.co.uk/wp-content/uploads/2021/01/Threat-Assessment-Page-Image-1.jpg
What is a threat assessment A threat assessment is a process of identifying analyzing and evaluating potential threats to an organization The goal of a threat assessment is to identify What Makes Comprehensive Security Assessments So Valuable Security threats do not exist in silos they span physical digital operational and even geopolitical domains A
Learn how to identify prioritize and mitigate security risks in a computing system using a 5 step process Find out the difference between risk management and security risk assessment and It undertakes security threat information analysis in support of the SRM framework such as Threat Assessments Threat Profiles Security Threat Information STI Alerts and Notices Topic
More picture related to What Is Security Threat Assessment
Ethical Hacking PPT
https://image.slidesharecdn.com/ethicalhacking-200225123508/85/Ethical-hacking-4-638.jpg

Ethical Hacking PPT Free Download
https://image.slidesharecdn.com/ethicalhacking-200225123508/85/Ethical-hacking-3-638.jpg

Threat Levels ProtectUK
https://www.protectuk.police.uk/sites/default/files/inline-images/UK Threat level - Substantial graphic.png
A risk assessment sometimes called a risk audit or physical risk evaluation is designed to give businesses a realistic understanding of their security threats and the Cybersecurity vulnerability assessment demands a proactive mindset forcing you to think like an attacker anticipate threats and methodically reduce risk What Is a Cyber
A threat assessment identifies potential threats to an organization evaluates their seriousness and plans mitigation strategies to reduce risks and impacts Key Components of Threat A Security Threat Assessment is a critical process used to identify evaluate and mitigate potential threats to an organization s assets including its people information and infrastructure
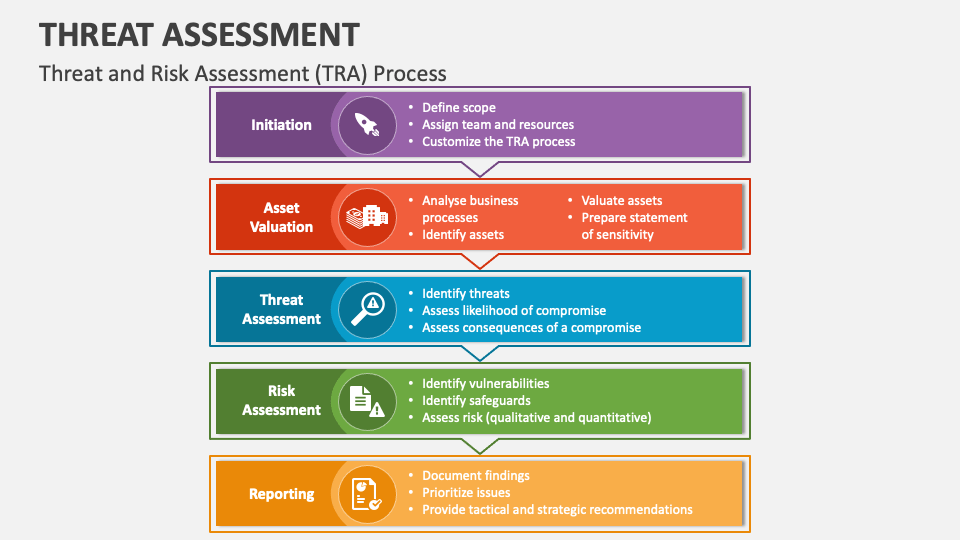
Threat Assessment PowerPoint Presentation Slides PPT Template
https://www.collidu.com/media/catalog/product/img/b/d/bde673d1322729dee9800437a34abc196a464f8afc3d9446ca944e3493c21397/threat-assessment-slide3.png

SECURITY RISK MANAGEMENT Threat Analysis Group
https://www.threatanalysis.com/wp-content/uploads/2022/02/Security-Risk-Assessment-v3-1-1024x768.png

https://www.hypr.com › security-encyclo…
Learn what a threat assessment is and how it is performed in cybersecurity Find out the difference between threat assessment and vulnerability assessment and see an example of a threat assessment process

https://ontic.co › resources › learn › threat-a…
The threat assessment is one of the most efficient tools security teams use to recognize and respond to physical security threats or information technology risks One of the most significant benefits of threat vulnerability

Threat Assessment We Generally Consider Intent And Capability When

Threat Assessment PowerPoint Presentation Slides PPT Template

The Importance Of Cyber Security

Security Infrastructure Examples

Tabel Risk Assessment

A Risk Manager s Approach To Cyber Security Compass Cyber Security

A Risk Manager s Approach To Cyber Security Compass Cyber Security
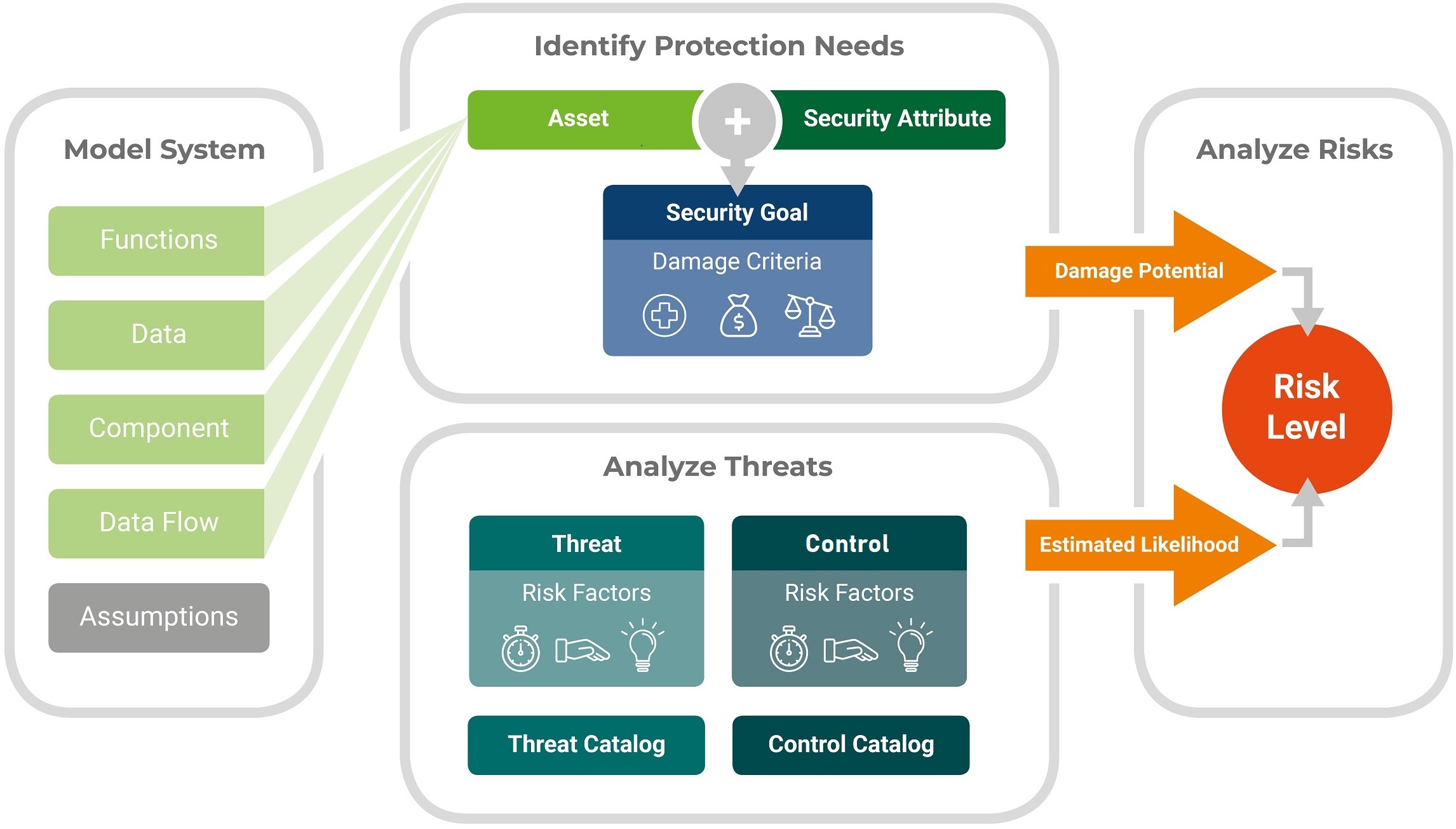
Threat Analysis And Risk Assessment
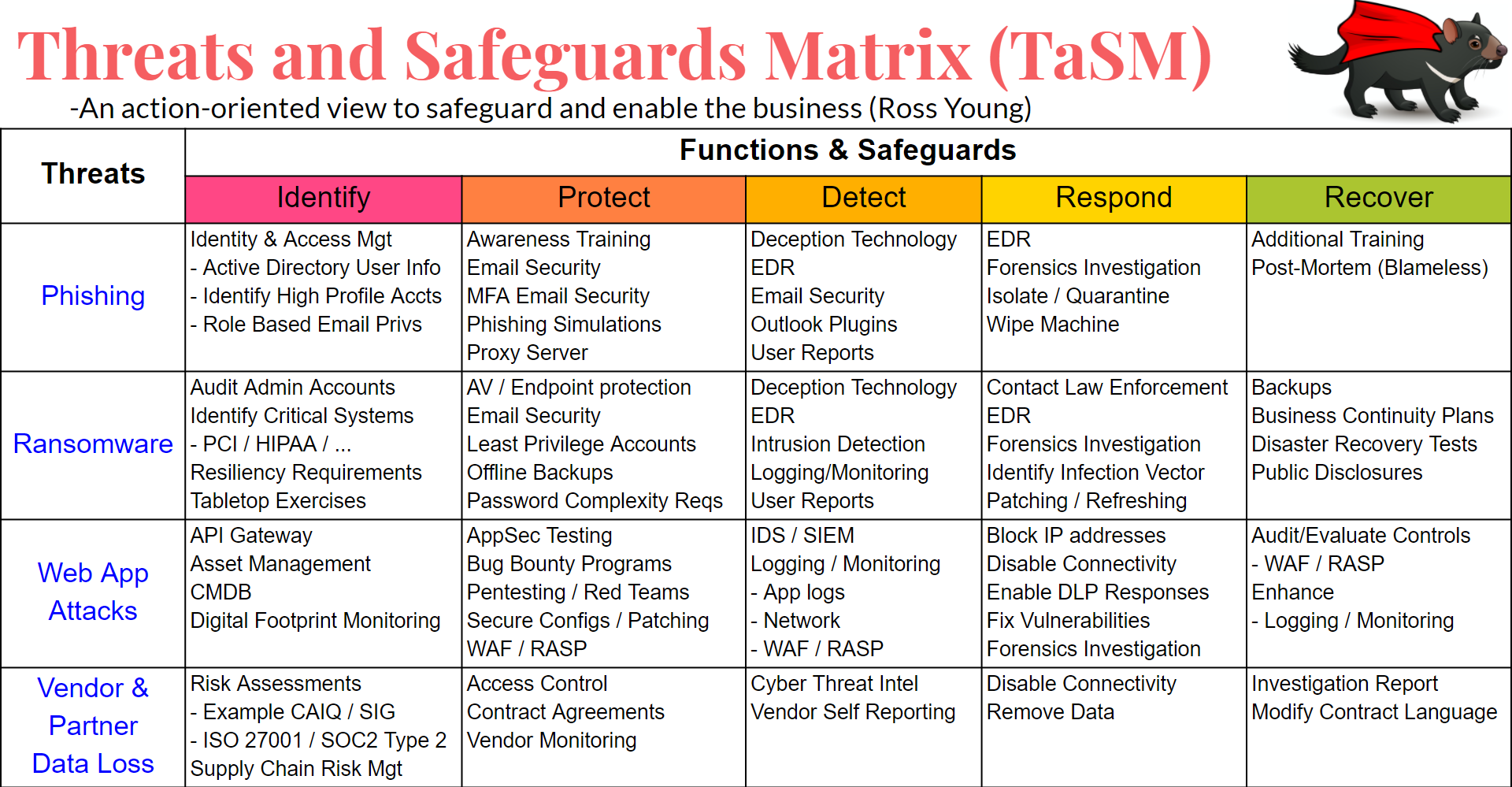
OWASP Threat And Safeguard Matrix TaSM OWASP Foundation
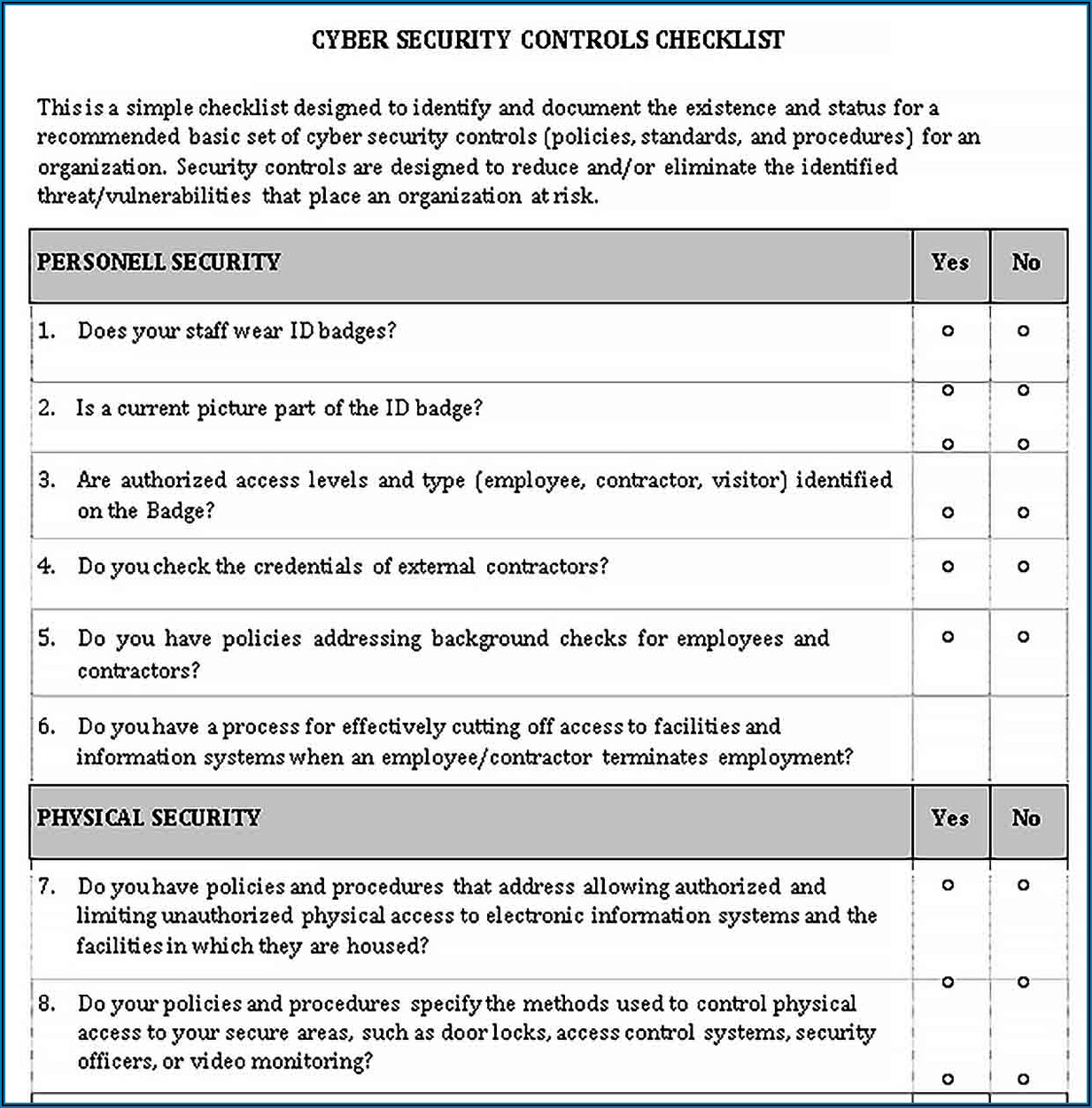
Security Vulnerability Assessment Template Template 1 Resume
What Is Security Threat Assessment - It undertakes security threat information analysis in support of the SRM framework such as Threat Assessments Threat Profiles Security Threat Information STI Alerts and Notices Topic