What Is Security Threats In Computer What is AI security Short for artificial intelligence AI security AI security is the process of using AI to enhance an organization s security posture With AI systems
What is IT security IT security which is short for information technology security is the practice of protecting an organization s IT assets computer systems networks digital What is information security Information security InfoSec is the protection of important information against unauthorized access disclosure use alteration or disruption It
What Is Security Threats In Computer

What Is Security Threats In Computer
https://i.pinimg.com/originals/43/aa/af/43aaaffac7cd2fdbb9d5f88ac663f3fc.png

Computer Security Threats YouTube
https://i.ytimg.com/vi/FpOrJ5CG8uI/maxresdefault.jpg

Cyber threat 21st Century Postal Worker
https://www.21cpw.com/wp-content/uploads/2016/11/cyber-threat.jpg
API security is a set of practices and procedures that protect application programming interfaces APIs and the data they transmit from misuse malicious bot attacks What is data security Data security is the practice of protecting digital information from unauthorized access corruption or theft throughout its entire lifecycle This concept
SOAR for security orchestration automation and response is a software solution that enables security teams to integrate and coordinate separate security tools automate repetitive tasks What are security controls Security controls are parameters implemented to protect various forms of data and infrastructure important to an organization Security controls
More picture related to What Is Security Threats In Computer

Pooquiet Blog
https://zvelo.com/wp-content/uploads/2018/10/zvelo-cyber-threat-network-security-definitions.jpg
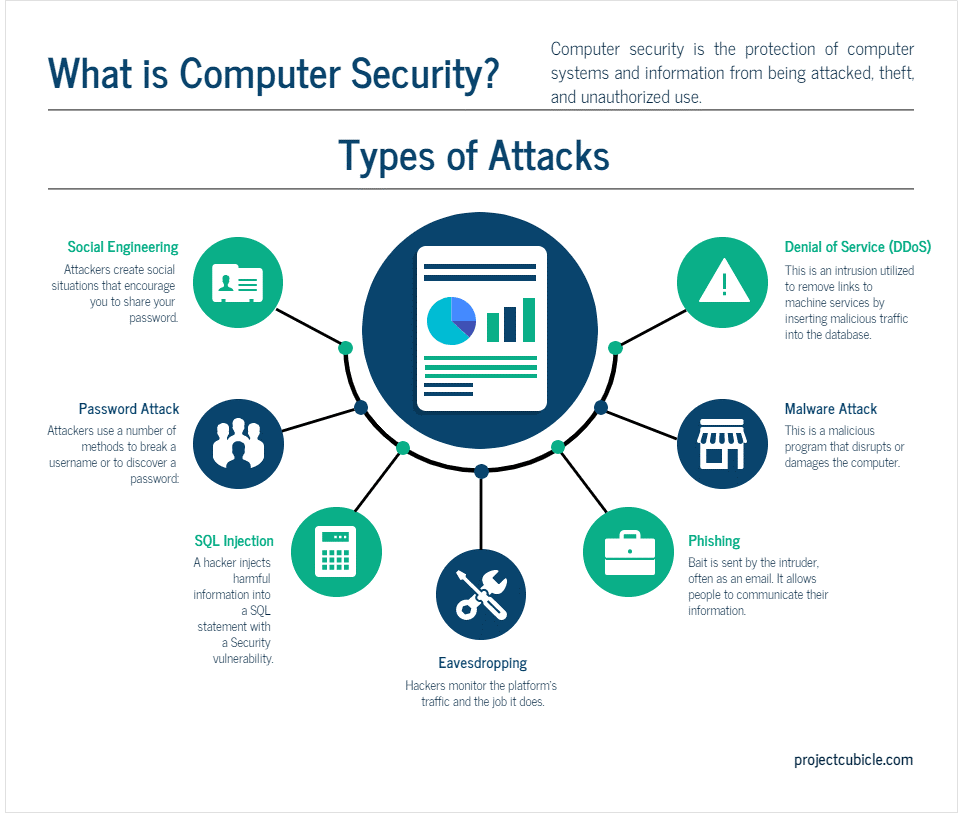
QIT
https://blog.qit.company/wp-content/uploads/2022/11/types-of-CS-threat.png

Cyber Threats
https://itsecuritywire.com/wp-content/uploads/2020/04/A-Look-Into-the-Top-Cyber-Security-Threats-in-the-Tech-Decade-of-2020-ITSW.jpg
Mobile device security refers to being free from danger or risk of an asset loss or data loss by using mobile computers and communication hardware Database security refers to the range of tools controls and measures designed to establish and preserve database confidentiality integrity and availability
[desc-10] [desc-11]
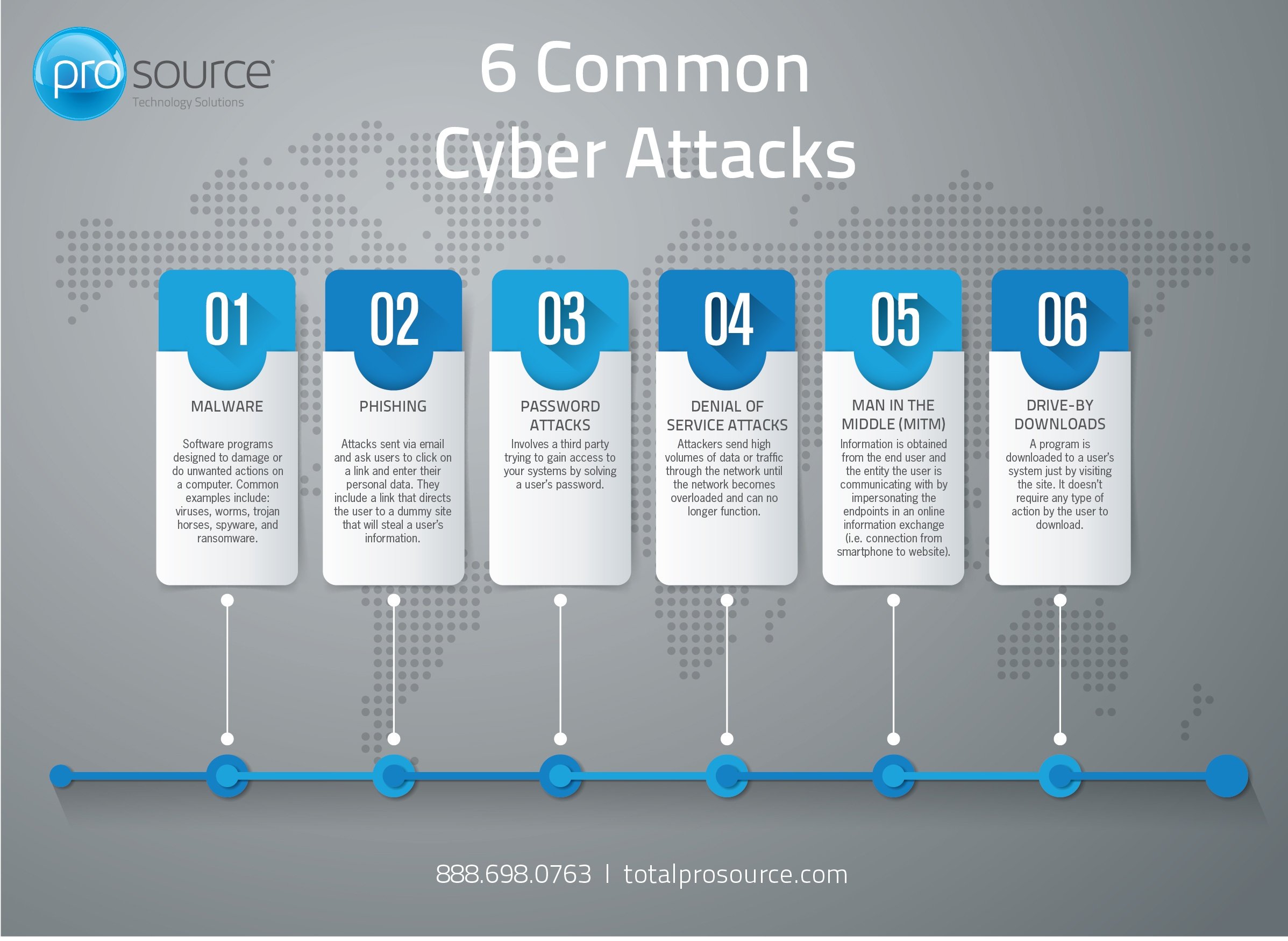
6 Common Types Of Cyber Attacks
https://cdn2.hubspot.net/hubfs/838527/6 Common Types of Cyber Attacks Infogrpahic.jpg

Cyber Threats As A Challenge To Internal Security Civilsdaily
https://d18x2uyjeekruj.cloudfront.net/wp-content/uploads/2022/10/WhatsApp-Image-2022-10-17-at-08.38.52.jpeg

https://www.ibm.com › think › topics › ai-security
What is AI security Short for artificial intelligence AI security AI security is the process of using AI to enhance an organization s security posture With AI systems

https://www.ibm.com › think › topics › it-security
What is IT security IT security which is short for information technology security is the practice of protecting an organization s IT assets computer systems networks digital

Cybersecurity Threats How To Protect Your Business From Cyber Attacks

6 Common Types Of Cyber Attacks

How To Prevent Computer Hackers Trackreply4
.jpg#keepProtocol)
Cyber Security How Can Your School Protect Itself From The Latest Threats

IT Threats 5 Biggest Threats To IT And The Best Solution To Help You

Unifying Privacy And Data Security Artofit

Unifying Privacy And Data Security Artofit
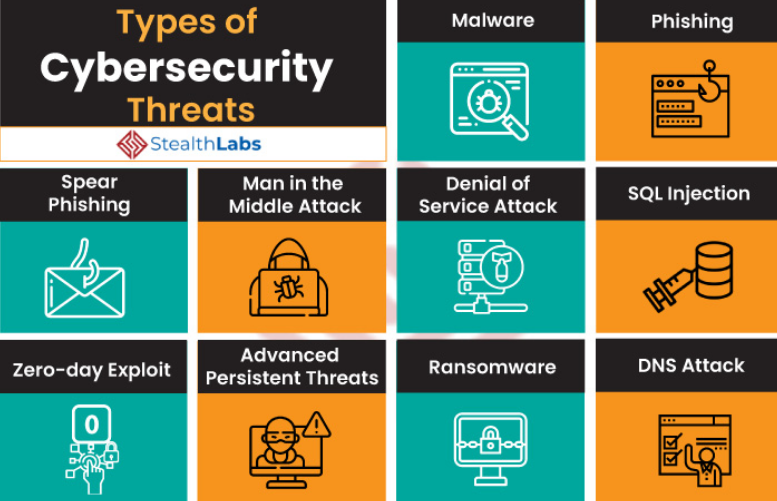
Cyber Security Threats And Attacks AIESEC Help Center
Understanding The Components Of Cyber Threat Analysis BLOCKGENI

Top 8 Network Security Threats Best Practices
What Is Security Threats In Computer - What are security controls Security controls are parameters implemented to protect various forms of data and infrastructure important to an organization Security controls