What Is The Chisholm Trail Named After Caesar cipher Encode and decode online Method in which each letter in the plaintext is replaced by a letter some fixed number of positions down the alphabet The method is named after
Nuestra herramienta de cifrado C sar online combina la criptograf a hist rica con funcionalidad moderna Descubre c mo funciona este cifrado simple pero influyente y c mo nuestra Codifique o decodifique el mensaje con Cifrado C sar seg n el turno seleccionado El cifrado C sar es uno de los m todos de cifrado de texto m s simples Consiste en sustituir cada letra
What Is The Chisholm Trail Named After

What Is The Chisholm Trail Named After
https://www.freebeerandhotwings.com/wp-content/uploads/2022/11/Childish-Gambino-Is-The-Alias-Of-What-Actor-And-Comic.jpg

The Chisholm Trail Part 3 Of 4 YouTube
https://i.ytimg.com/vi/dfsOBSFnnj0/maxresdefault.jpg

Photo Map Of The Old Chisholm Cattle Trail
https://www.hmdb.org/Photos2/267/Photo267376o.jpg
Free online translator for Caesar cipher Decoder and Encoder Easily encode and decode messages with this classic substitution cipher Free online Caesar cipher encoder and decoder tool Encrypt and decrypt text using the classic shift cipher Interactive visualization multiple alphabets and brute force decryption
El Cifrado C sar una t cnica antigua de encriptaci n se hizo famoso a trav s de Julio C sar el renombrado general y pol tico romano Utiliz este m todo para proteger comunicaciones The Caesar cipher is one of the earliest and simplest ciphers that were invented It works like this First choose some text that you want to encrypt Let s choose the text eat Next pick a
More picture related to What Is The Chisholm Trail Named After

An Old Map Shows The Route Of The Railroad System
https://i.pinimg.com/736x/1d/9f/a8/1d9fa8a9a2f006e34132160da6631803--wild-west-texas-maps.jpg

Image Result For Shirley Chisholm First Black President Running For
https://i.pinimg.com/originals/7a/8b/39/7a8b3974fc1d96e97a7e71948e488dc5.jpg

Historians Chisholm Trail Heritage Center
https://onthechisholmtrail.com/wp-content/uploads/2020/10/chisholm_trail_map.jpg
Herramienta para codificar y decodificar con el cifrado C sar un cifrado por desplazamiento simple y famoso que reemplaza cada letra por otra m s adelante en el alfabeto Compatible Are you unsure that your cipher is a Caesar cipher Use the Cipher Identifier to find the right tool You can decode decrypt or encode encrypt your message with your key If you don t have
[desc-10] [desc-11]

Celebrating Shirley Chisholm Fellowship Housing
https://images.squarespace-cdn.com/content/v1/5ba26030f8370a4e368ba351/2b588d11-a32d-4b94-92b3-b670a1ecb01a/Shirley+SQ.jpg
Life And Career Of Shirley Chisholm C SPAN
https://ximage.c-spanvideo.org/eyJidWNrZXQiOiJwaWN0dXJlcy5jLXNwYW52aWRlby5vcmciLCJrZXkiOiJGaWxlc1wvZWQ1XC8yNTI1LTM4Mjc0LTEuanBnIiwiZWRpdHMiOnsicmVzaXplIjp7ImZpdCI6ImNvdmVyIiwiaGVpZ2h0Ijo1NzYsIndpZHRoIjoxMDI0fX19

https://cryptii.com › pipes › caesar-cipher
Caesar cipher Encode and decode online Method in which each letter in the plaintext is replaced by a letter some fixed number of positions down the alphabet The method is named after

https://caesar-cipher.com › es › cifrado-cesar
Nuestra herramienta de cifrado C sar online combina la criptograf a hist rica con funcionalidad moderna Descubre c mo funciona este cifrado simple pero influyente y c mo nuestra

Chisholm Western National Historic Trails Western Region Property

Celebrating Shirley Chisholm Fellowship Housing

Found This 1870 Map Of The Cattle Trails Of The West Cattle Trails

The Chisholm Trail Named For Jesse Chisholm Was Used In The Late 19th

Native Americans Chisholm Trail

Chrisholm Trail Texas Named For Jesse Chrisholm A Half Cherokee

Chrisholm Trail Texas Named For Jesse Chrisholm A Half Cherokee
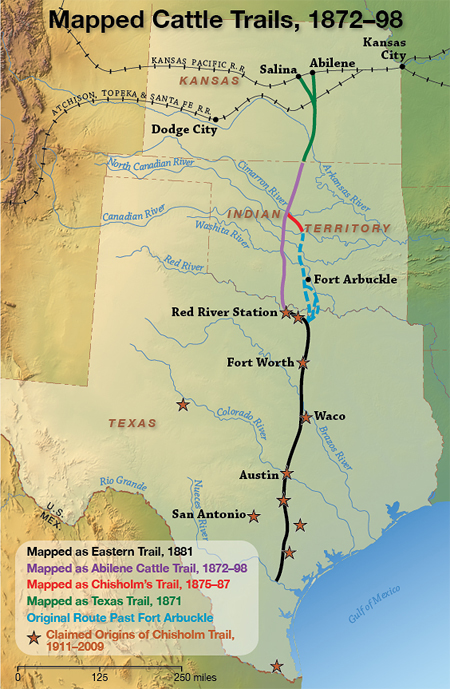
Old Chisholm Trail Map
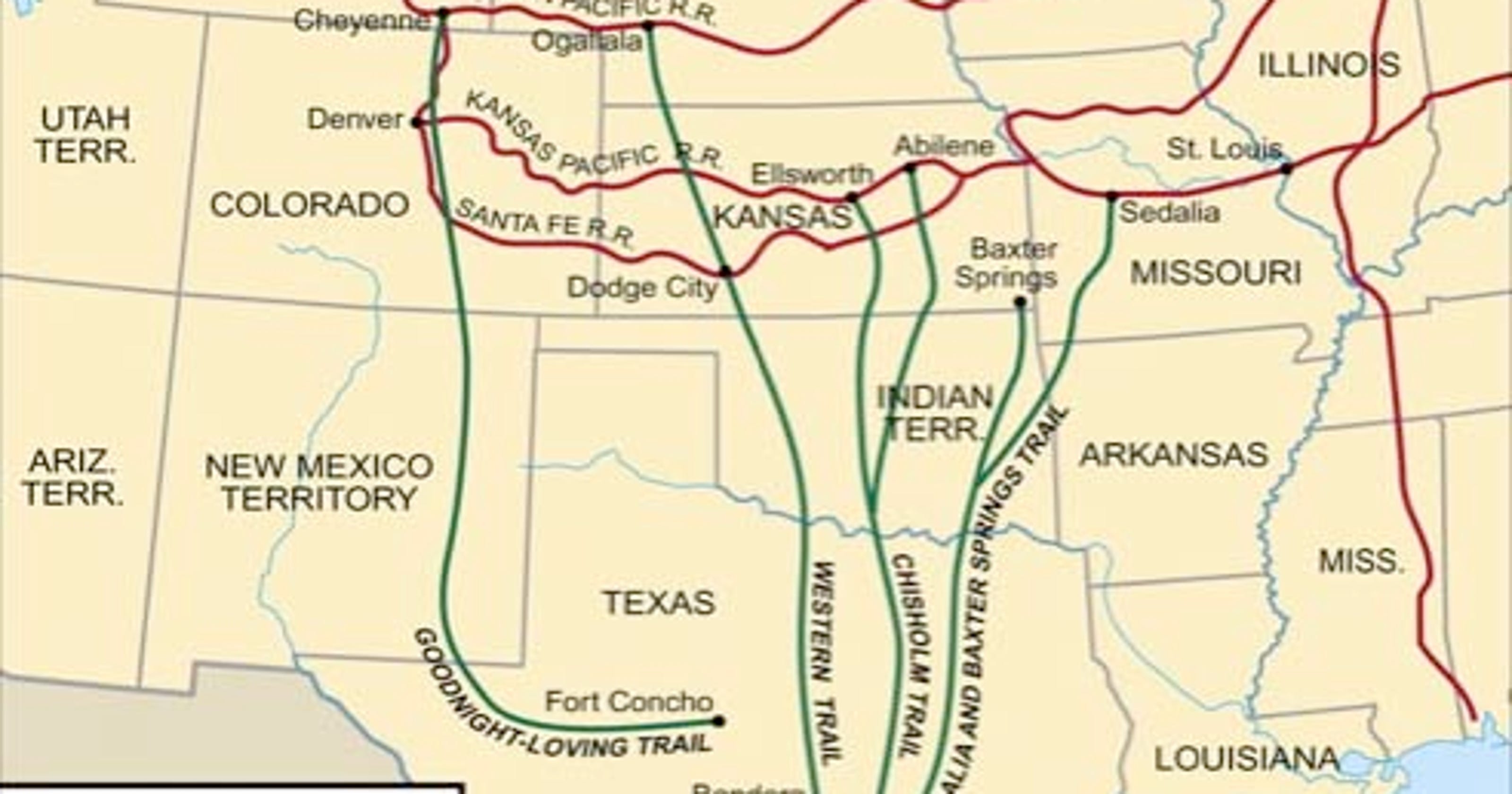
Old Chisholm Trail Map

Maps Westward Expansion Westward Atchison The Expanse
What Is The Chisholm Trail Named After - Free online Caesar cipher encoder and decoder tool Encrypt and decrypt text using the classic shift cipher Interactive visualization multiple alphabets and brute force decryption