Security Posture Assessment Checklist Security validates the core skills required for a career in IT security and cybersecurity Learn about the certification available training and the exam
Information security is also referred to as information security infosec It includes strategies for managing the processes tools and policies that protect both digital and 30 demonstrators were killed in clashes with the security forces over the weekend The tighter security measures precautions include video cameras throughout the city centre The
Security Posture Assessment Checklist

Security Posture Assessment Checklist
https://images.template.net/wp-content/uploads/2019/08/Safety-and-Security-Assessment-Checklist.jpg
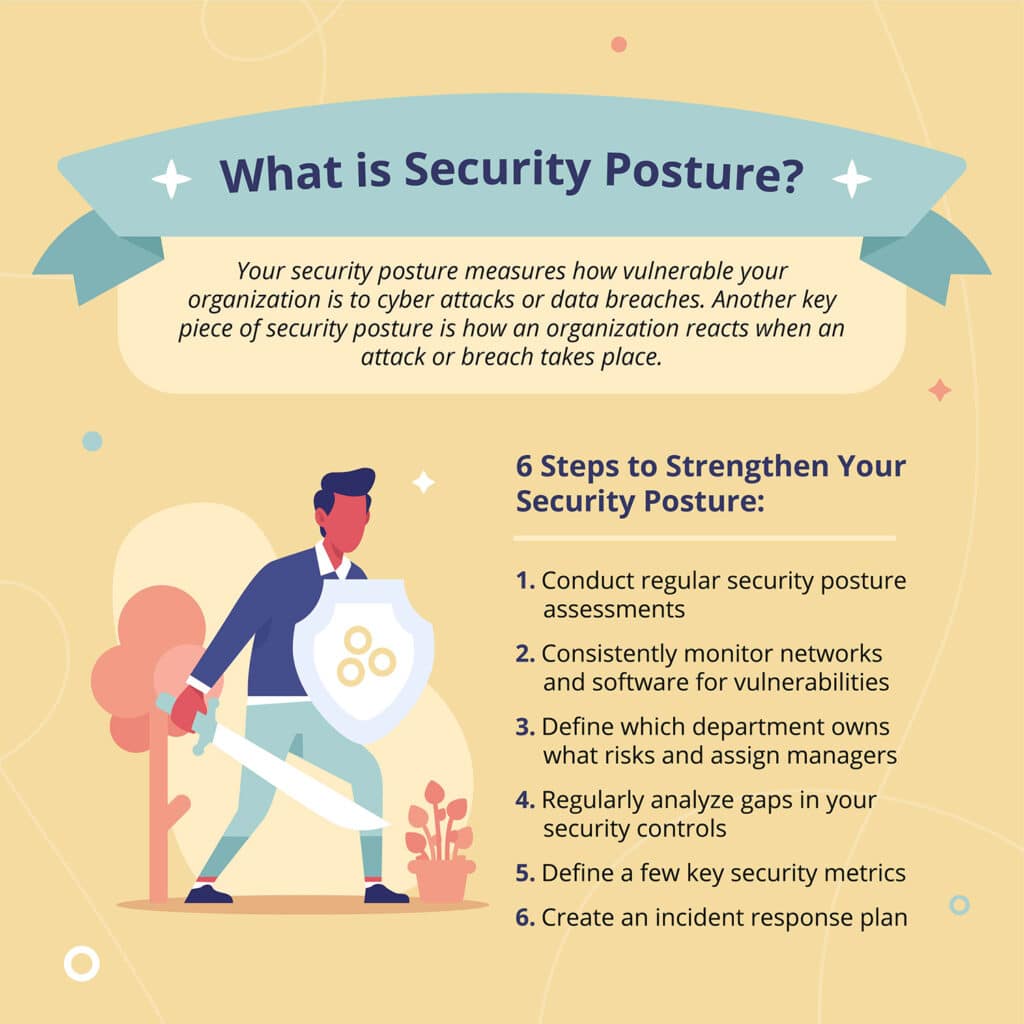
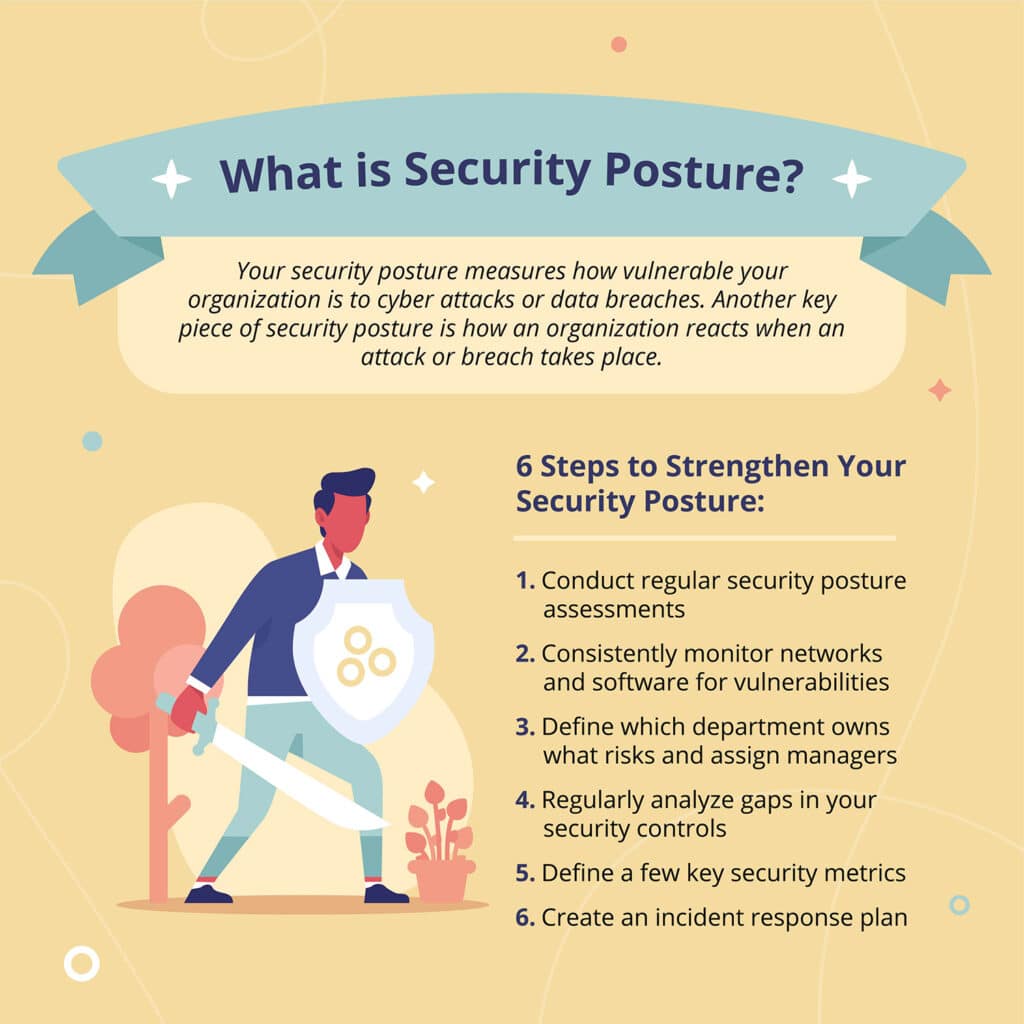
Understanding Cyber Security Posture Assess And Strengthen Your
https://hyperproof.io/wp-content/uploads/2021/11/Hyperproof_Graphic_What_Is_Security_Posture-1024x1024.jpg

Audit Risk Assessment Template NoemiqoGordon
https://i.pinimg.com/736x/b3/74/11/b374114d39058780880e41f2e6047ba6.jpg
Cybersecurity is all about protecting your computer phone or any digital device from hackers and online threats It keeps your personal information bank details files and We called security when we found the door open The meeting was held under tight security The prisoner was being kept under maximum security I like the security of knowing there will be
At its core security refers to the measures taken to protect physical digital or psychological well being from threats and danger It also denotes the systems or procedures While you cannot avoid security threats but you can stay aware and alert Various cybersecurity standards protect information and data providing measures for redressal when
More picture related to Security Posture Assessment Checklist
Why A Security Posture Assessment Is Critical For Modern Organizations
https://insight.ieeeusa.org/wp-content/uploads/sites/2/2023/08/security-posture-assessment.jpg

5am Self care Morning Routine Checklist Healthy Routines Healthy
https://i.pinimg.com/originals/2d/3b/83/2d3b830042f530cc33f65405ededa416.webp
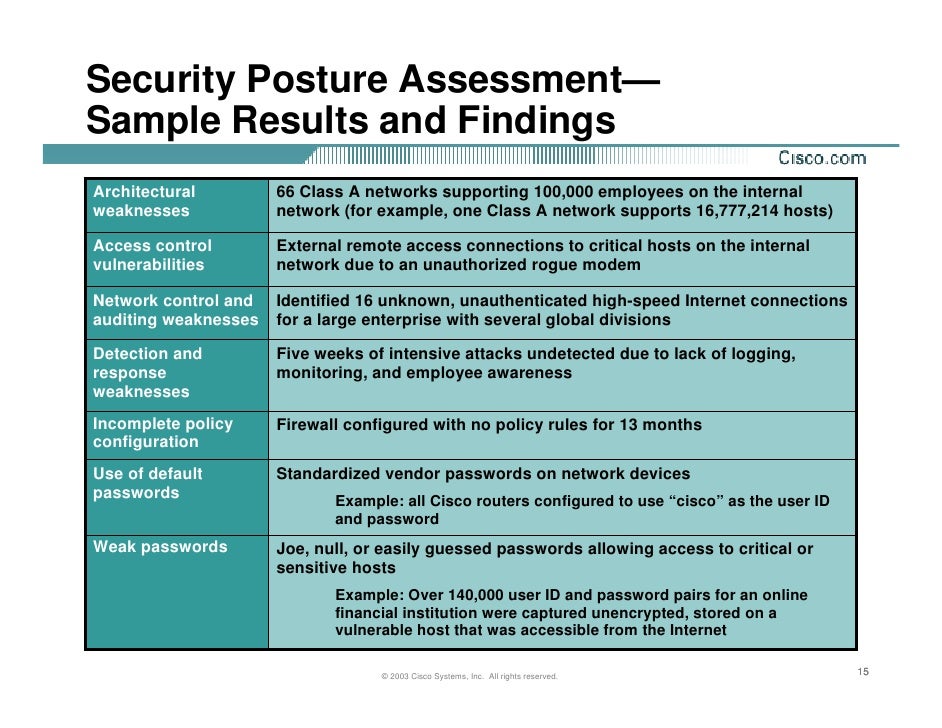
Ccmigration 09186a008033a3b4
https://image.slidesharecdn.com/ccmigration09186a008033a3b4-24507/95/ccmigration09186a008033a3b4-15-728.jpg?cb=1195291042
Cybersecurity is the combination of methods processes tools and behaviors that protect computer systems networks and data from cyberattacks and unauthorized access Although Cybersecurity is the practice of protecting systems networks and programs from digital attacks These cyberattacks are usually aimed at accessing changing or destroying sensitive
[desc-10] [desc-11]

Cloud Risk Assessment Checklist Mobiz
https://mobizinc.com/wp-content/uploads/2023/09/Cloud-Risk-Assessment-Checklist.jpg
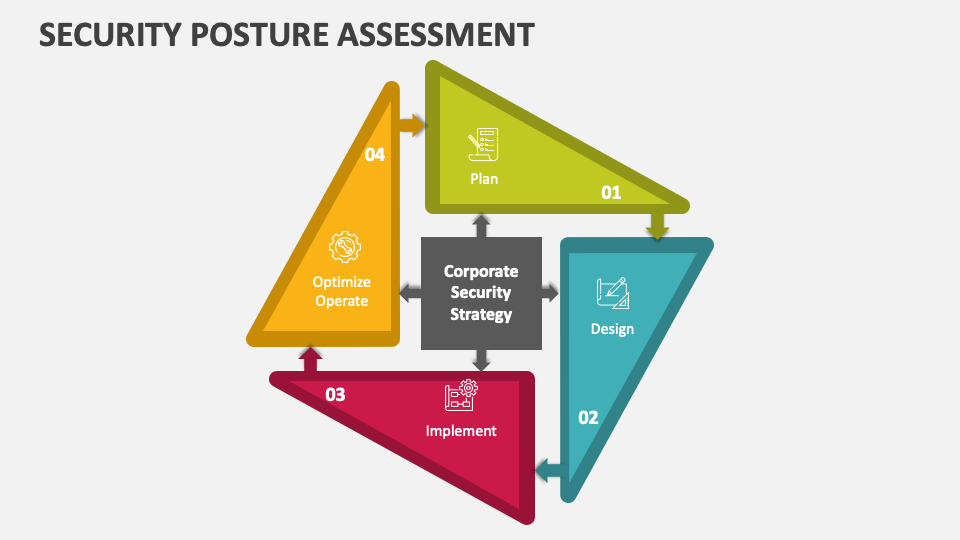
Security Posture Assessment PowerPoint Presentation Slides PPT Template
https://www.collidu.com/media/catalog/product/img/e/3/e3b990e0950f81b3147a593f47137b7d0bf8e915bdd29ec51f2f7529fadcf727/security-posture-assessment-slide6.png

https://www.comptia.org › certifications › security
Security validates the core skills required for a career in IT security and cybersecurity Learn about the certification available training and the exam
https://www.techtarget.com › searchsecurity › definition › security
Information security is also referred to as information security infosec It includes strategies for managing the processes tools and policies that protect both digital and
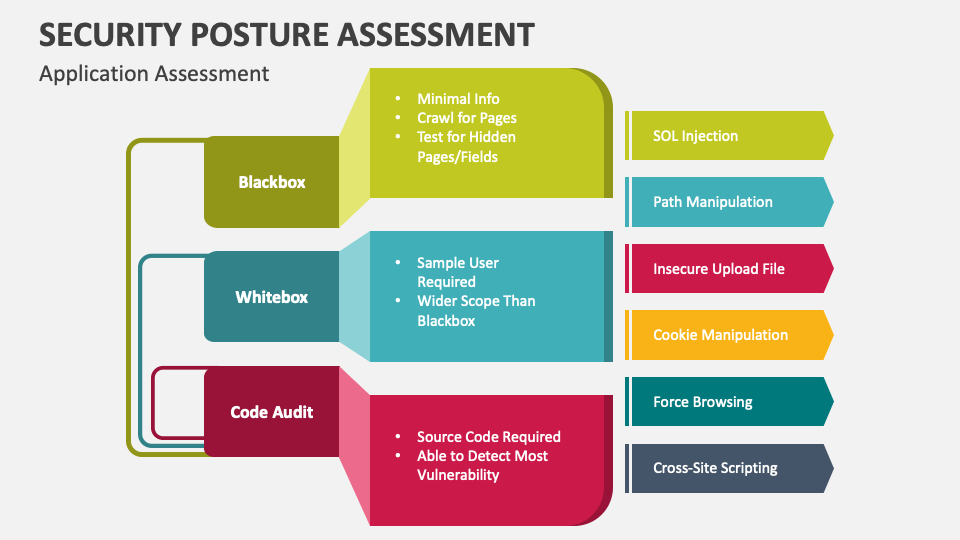
Security Posture Assessment PowerPoint Presentation Slides PPT Template

Cloud Risk Assessment Checklist Mobiz
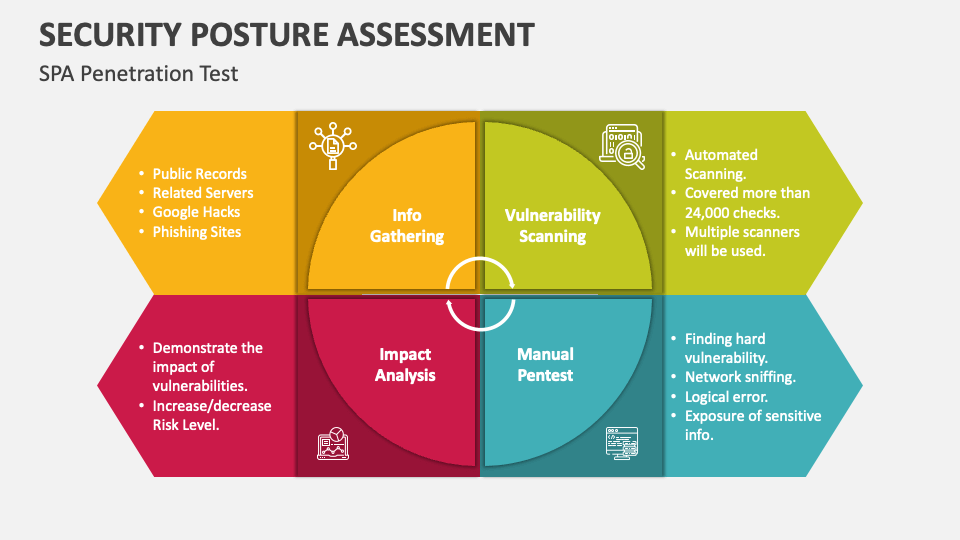
Security Posture Assessment PowerPoint Presentation Slides PPT Template
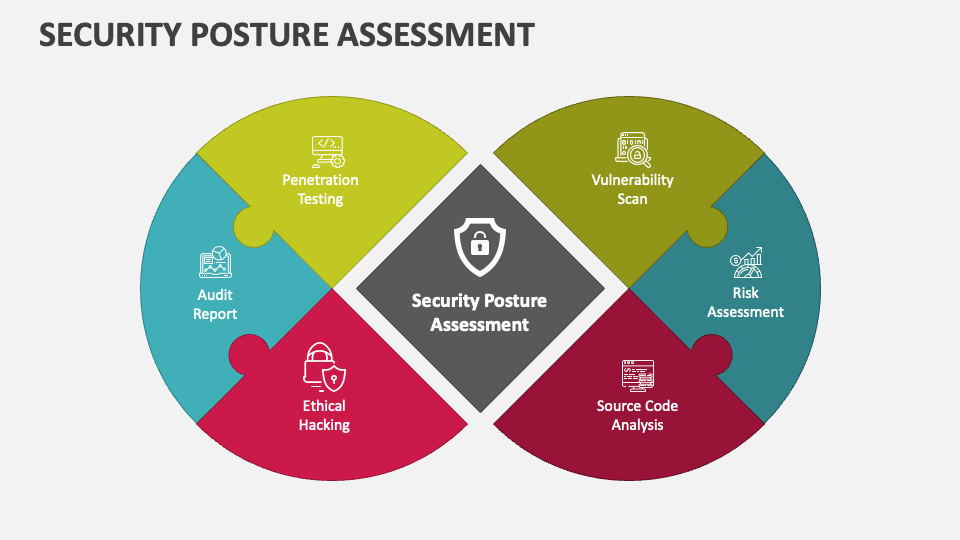
Security Posture Assessment PowerPoint Presentation Slides PPT Template
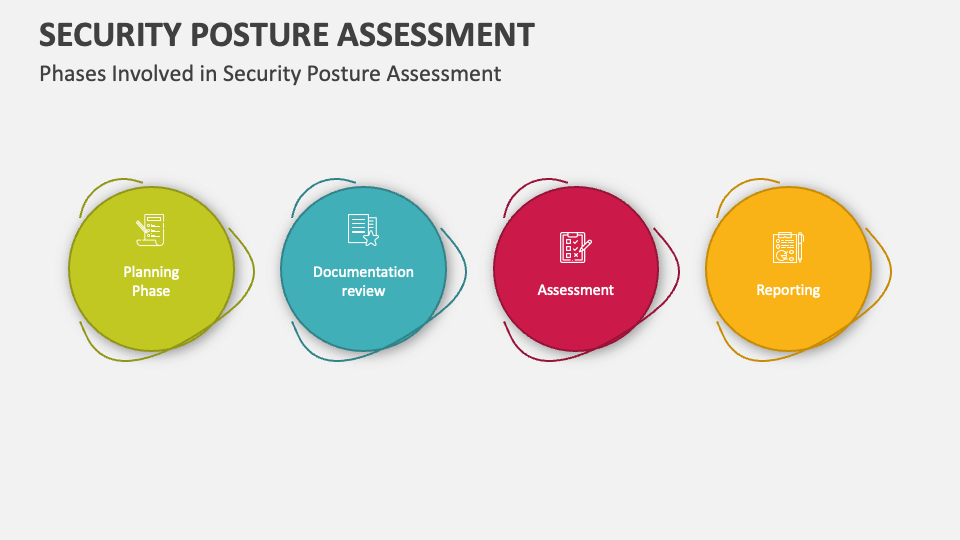
Security Posture Assessment PowerPoint Presentation Slides PPT Template

Facility Condition Assessment Checklist And Guide For Building Owners

Facility Condition Assessment Checklist And Guide For Building Owners

Risk Assessment Early Years Course ELearn Here
Checklist To Do List APK For Android Download

Assessment Checklist Icon Feedback Or Checklist Concept Vector
Security Posture Assessment Checklist - While you cannot avoid security threats but you can stay aware and alert Various cybersecurity standards protect information and data providing measures for redressal when