Security Risk Management Courses In South Africa Requirements But IT security also includes physical security measures for example locks ID cards surveillance cameras required to protect buildings and devices that house data and IT
Even limited security might provide significant cost savings Those with limited AI security reported an average data breach cost of USD 4 04 million USD 400 000 less than To make an account on an official government website a user must enter their Social Security number SSN The website sends the Social Security number to a
Security Risk Management Courses In South Africa Requirements

Security Risk Management Courses In South Africa Requirements
https://i.ytimg.com/vi/SkvoHnL8ZdQ/maxresdefault.jpg

Risk Management Courses Risk Management Online Courses Introduction
https://i.ytimg.com/vi/QvvO1x3zRa0/maxresdefault.jpg

IRC J Informatic Research Center Journal
https://irc.stmik-im.ac.id/public/site/images/pherwanto/irc-j-cover.png
API security is a subset of application security that prioritizes securing individual endpoints and managing access with fine grained permissions so that every data exchange is Security keys are the ultimate physical security measure for protecting your online accounts We tested and ranked the best security keys that combine security affordability and
SOAR technology arose as a consolidation of three earlier security tools According to Gartner which first coined the term SOAR in 2015 SOAR platforms combine the functions of security Chief information security officers CISOs who oversee information security efforts have become a fixture of corporate C suites Demand is rising for information security analysts
More picture related to Security Risk Management Courses In South Africa Requirements

SERVICES JOINTECH ENTERPRISE PTE LTD
https://jointech.support/wp-content/uploads/2024/03/2019061716405111192.webp

Short Courses South Africa IT Courses South Africa School Of IT
https://www.schoolofit.co.za/wp-content/uploads/2023/11/cism-courses-south-africa-1-531x326.png
![]()
Risk Management Generic Outline Color Icon
https://cdn-icons-png.flaticon.com/512/4501/4501570.png
Protect yourself this holiday season and going into 2025 with the best antivirus software in the market tested and recommended by our experts A comprehensive data security strategy incorporates people processes and technologies Establishing appropriate controls and policies is as much a question of organizational culture
[desc-10] [desc-11]
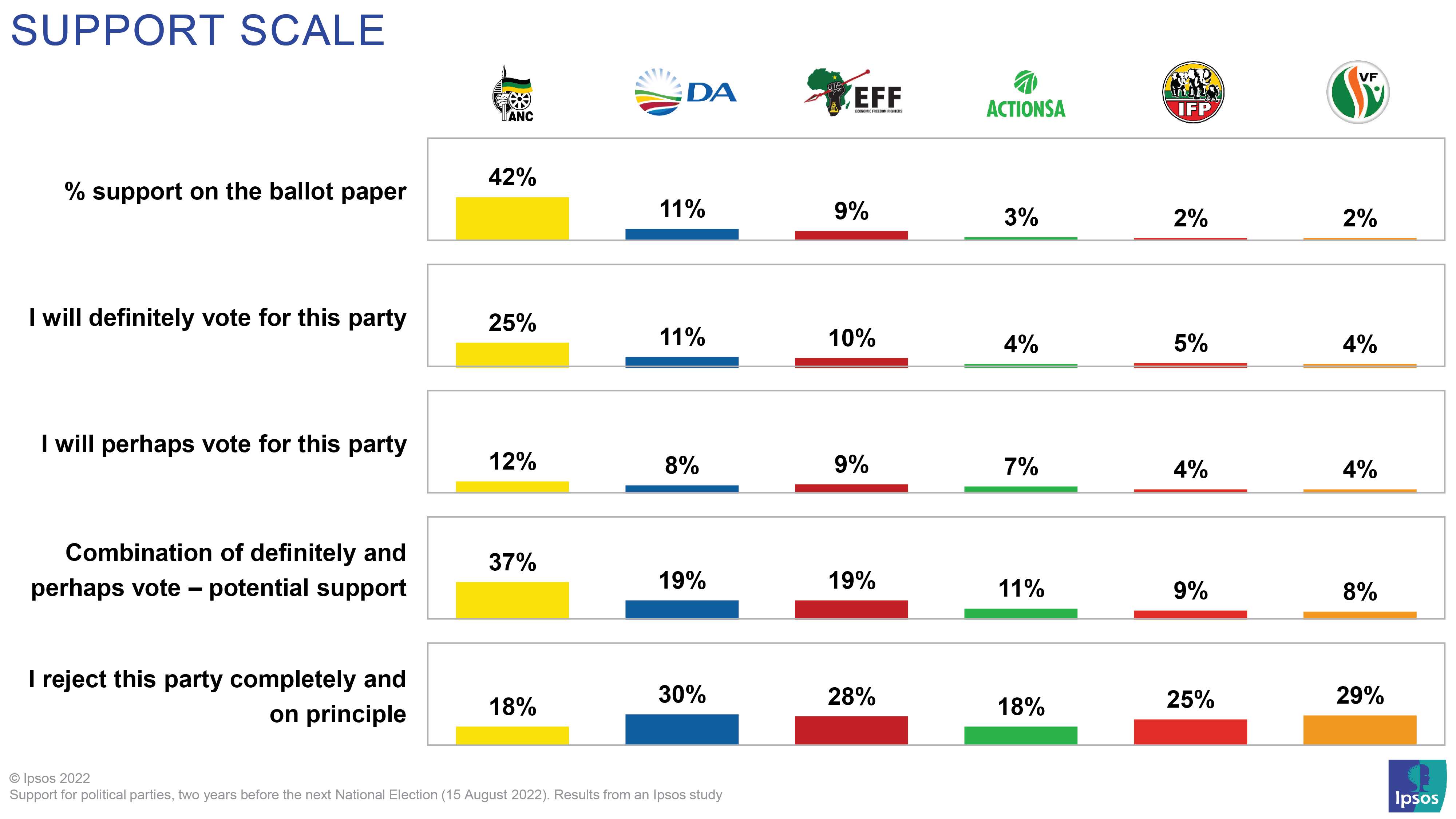
Latest Election Results Who Won
https://www.ipsos.com/sites/default/files/inline-images/Support for political parties%2C two years before the next National Election_0.jpg
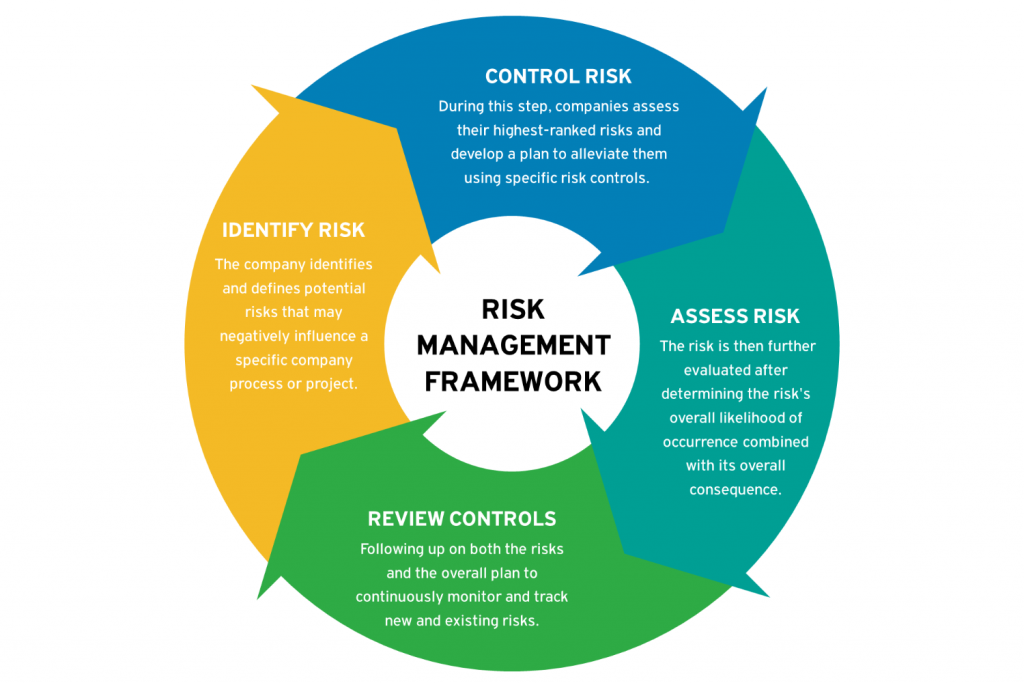
Introduction To Financial Risk Management Orion Training
https://oriontraining.eu/wp-content/uploads/2020/05/Risk-Management-FREE-COURSE-1024x683.png

https://www.ibm.com › think › topics › it-security
But IT security also includes physical security measures for example locks ID cards surveillance cameras required to protect buildings and devices that house data and IT

https://www.ibm.com › think › topics › ai-security
Even limited security might provide significant cost savings Those with limited AI security reported an average data breach cost of USD 4 04 million USD 400 000 less than

ADT OPERATOR TRAINING IN GAUTENG Gautech Training Institute

Latest Election Results Who Won

Why Wood Sawmilling South Africa
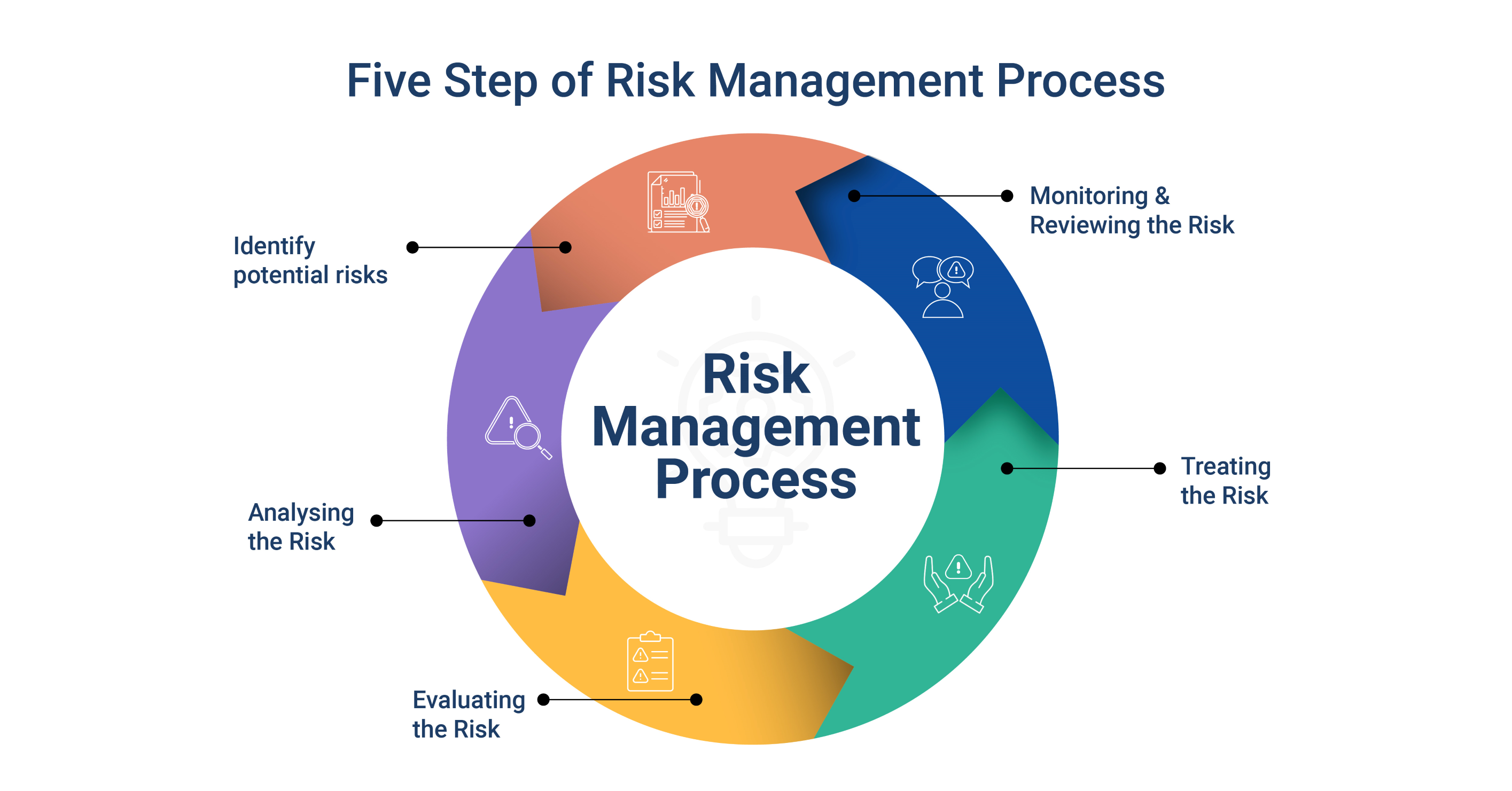
Risk Management

Damelin Online Courses South Africa How To Make Money From Home In

Fancourt s Montagu Golf Course George South Africa

Fancourt s Montagu Golf Course George South Africa

25 Best Risk Management Courses In Saudi Arabia 2025

Top Sports Science Courses In South Africa At Eta College

Business Management Courses In India After 12th Aimlay
Security Risk Management Courses In South Africa Requirements - [desc-14]