What Constitutes Bullying And Harassment At Work The Common Vulnerabilities and Exposures CVE Program s primary purpose is to uniquely identify vulnerabilities and to associate specific versions of code bases e g software and
Vulnerabilities are flaws or weaknesses in a system s design implementation or management that can be exploited by a malicious actor to compromise its security Common Vulnerabilities and Exposures CVE deutsch Bekannte Schwachstellen und Anf lligkeiten ist ein vom US amerikanischen National Cybersecurity FFRDC betriebenes und
What Constitutes Bullying And Harassment At Work

What Constitutes Bullying And Harassment At Work
https://d28j9ucj9uj44t.cloudfront.net/uploads/2021/08/Bectu_BandH_flowchart_A4_poster_v03-3-1086x1536.jpg
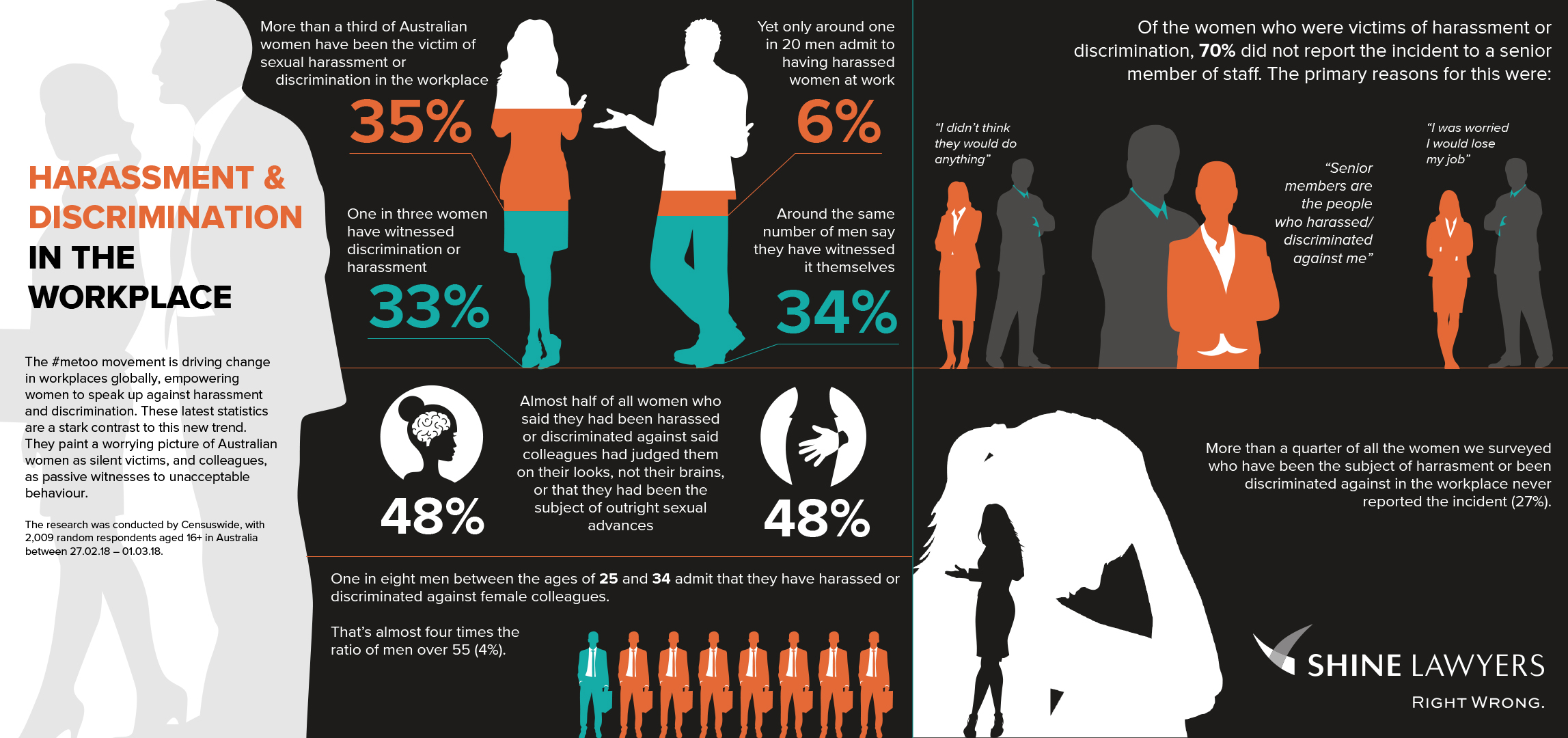
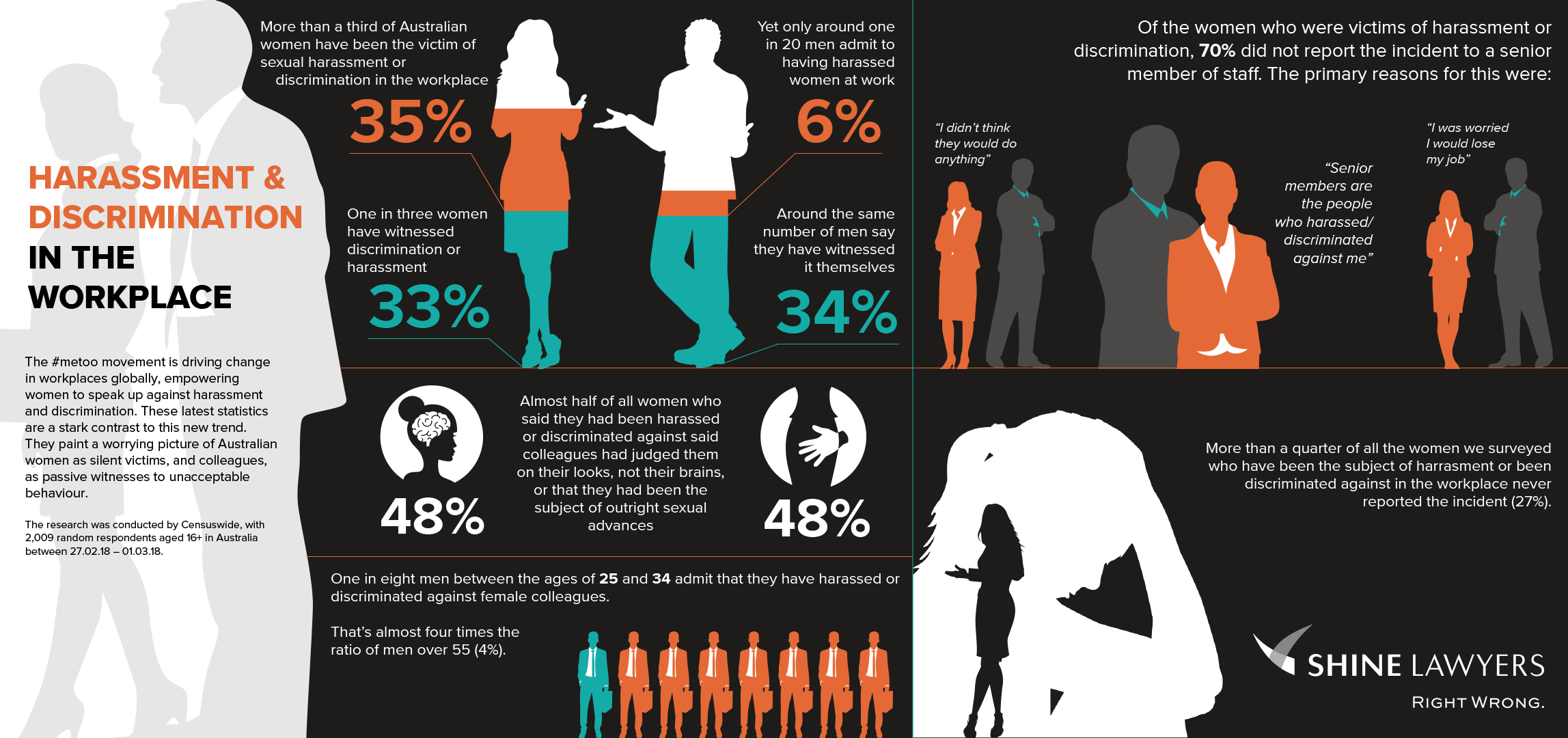
Infographic Examples About Bullying Feryub
https://shinestore.blob.core.windows.net/shine-lawyers-media/2018/03/CENSUSWIDE-GRAPHIC-1-lines-AS2.jpg

Bullying It s Not Just In Schools HR Resolutions
https://www.hrresolutions.com/wp-content/uploads/2017/10/bullying.jpg
You can read about the top vulnerabilities and download a paper that covers them in detail Many organizations and agencies use the Top Ten as a way of creating awareness about application Datenbanken des Common Vulnerabilities and Exposures CVE Das amerikanische Pendant zum WID vergibt automatisch IDs f r neu erkannte Sicherheitsl cken
Vulnerabilities can be exploited by a variety of methods including SQL injection buffer overflows cross site scripting XSS and open source exploit kits that look for known This article talks about what are vulnerabilities their types causes and details how to implement a winning vulnerability management strategy
More picture related to What Constitutes Bullying And Harassment At Work

Sexual Harassment Assault And Abuse At Office Illustration Set Men
https://as2.ftcdn.net/v2/jpg/03/78/72/17/1000_F_378721774_0sPWriKy2zTC1u4Lk0nseSbiOQLoqshg.jpg

Workplace Harassment How Do We Stop It
https://www.lawyer-monthly.com/Lawyer-Monthly/wp-content/uploads/2018/04/Workplace-Harassment-How-Do-We-Stop-It.jpg

1 Day Preventing Sexual Harassment And Harassment At Work
https://www.bmf.org.uk/images/training/harassment.jpg
Security vulnerabilities are weaknesses that can be exploited by attackers to compromise systems and data Our guide explores the different types of vulnerabilities their Security vulnerabilities are found and fixed through formal vulnerability management programs Vulnerability management comprises cross team best practices and
[desc-10] [desc-11]

How To Prevent Bullying And Harassment At Work Praxis42
https://www.praxis42.com/wp-content/uploads/2022/03/bullying-and-harassment-at-work.jpg
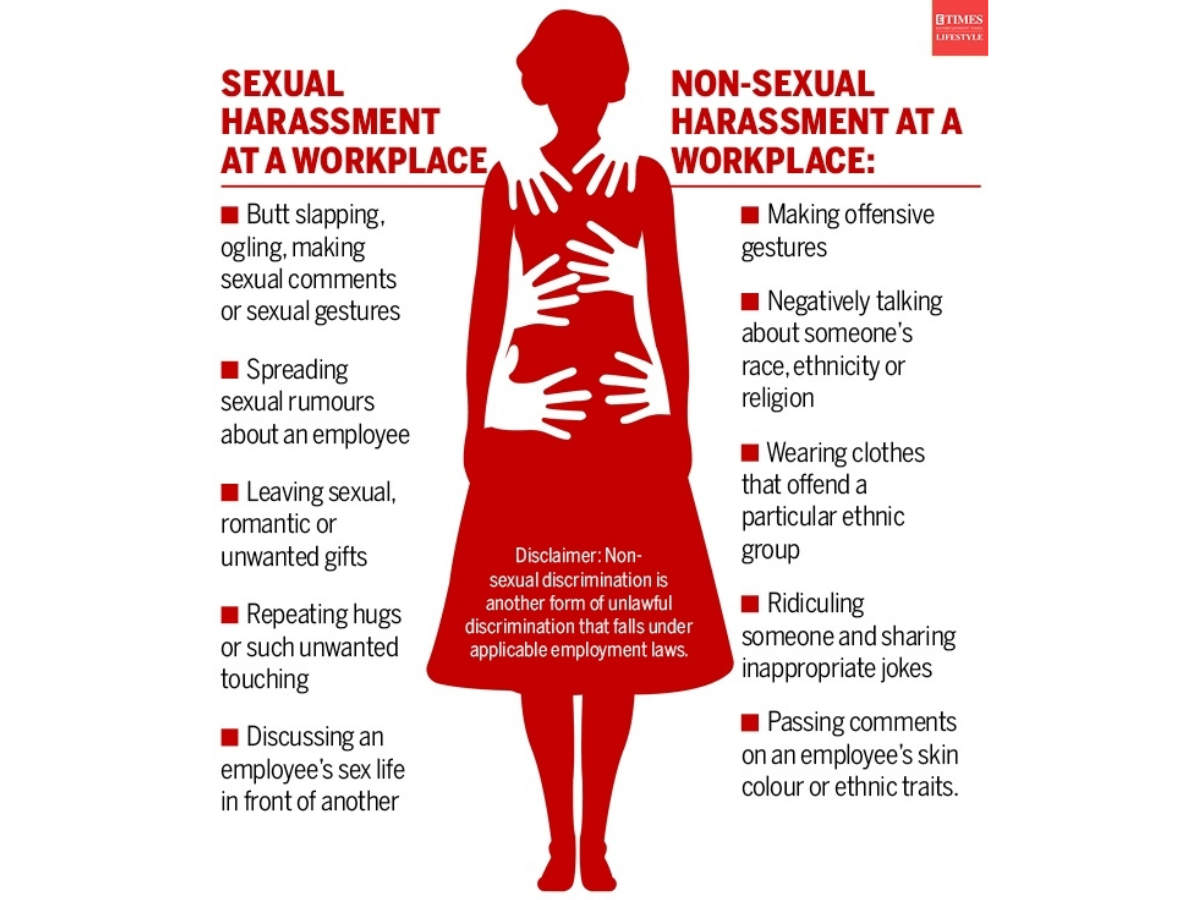
Kinds Of Behaviours That Are Considered Sexual Harassment At Workplace
https://static.toiimg.com/photo/77521562.cms

https://nvd.nist.gov › vuln
The Common Vulnerabilities and Exposures CVE Program s primary purpose is to uniquely identify vulnerabilities and to associate specific versions of code bases e g software and
https://en.wikipedia.org › wiki › Vulnerability_(computer_security)
Vulnerabilities are flaws or weaknesses in a system s design implementation or management that can be exploited by a malicious actor to compromise its security

Violence And Harassment At Work Violence Against Workers Is The Direct

How To Prevent Bullying And Harassment At Work Praxis42

Zero Tolerance For Workplace Harassment YouTube

Reporting Bullying And Harassment At Work in 2022 YouTube

Livingston Parish Gravity Drainage District 1 Denham Springs

WORKPLACE BULLYING IF YOU DON T STEP IN YOU RE SUPPORTING IT Yes

WORKPLACE BULLYING IF YOU DON T STEP IN YOU RE SUPPORTING IT Yes
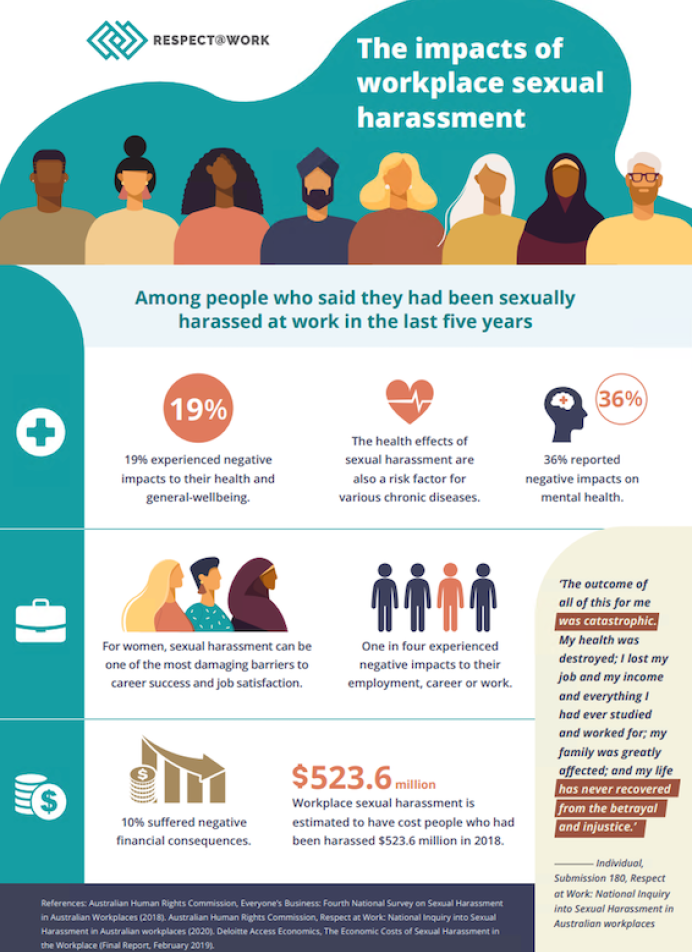
The Impacts Of Workplace Sexual Harassment Respect Work

Sexual Harassment Vector Art Icons And Graphics For Free Download

Harassment Support Vector Art Icons And Graphics For Free Download
What Constitutes Bullying And Harassment At Work - Datenbanken des Common Vulnerabilities and Exposures CVE Das amerikanische Pendant zum WID vergibt automatisch IDs f r neu erkannte Sicherheitsl cken