What Is Cyber Stalking Give Example This white paper unpacks the concept of cyber resilience outlining the evolution of the cyber paradigm and establishes a concept of successful cyber resilience
Cyber Security 58 Taking a holistic platform approach to security rather than a more traditional siloed one offers businesses a streamlined path to cyber resilience
What Is Cyber Stalking Give Example

What Is Cyber Stalking Give Example
https://pbs.twimg.com/media/Fb5Iv9bUYAA4Nng.jpg
Cyber Security SCI
https://enroll.scitexas.edu/wp-content/uploads/2023/02/THE-EDGE-INFO-GRAPHIC-1024x1024.png

Cyberbullying The Living Nightmare Bullying Cyberbullying
https://bullyingandcyberbullyingprevention.weebly.com/uploads/6/4/9/4/64943309/8734921_orig.png
The increasing threat of cyberattacks is prompting governments to toughen up laws and build resilience Here are some of the regulations that came into force in 2024 Leaders anticipate increasingly complex threat landscape in 2025 DeepSeek exposes cybersecurity blind spot US halts election security work amid cybersecurity review
Know the key insights tensions and trade offs that will likely shape the future of cybersecurity and can help an organization better prepare to face cyber threats Fraudsters used an AI deepfake to steal 25 million from UK engineering firm Arup Here Arup s Chief Information Officer Rob Greig talks about the lessons learned Cyber
More picture related to What Is Cyber Stalking Give Example

Cyber Stalking Infographic Safe Living
https://www.safeliving2.com/wp-content/uploads/2023/01/Cyber-Stalking-Infograph-1-600x1500.png

Cyber Stalking Infographic Safe Living
https://www.safeliving2.com/wp-content/uploads/2023/02/Cyber-Stalking-feature-image-1.png

Cyberstalking
https://cyberbullying.org/wp-content/uploads/2018/03/cyberstalking.jpg
The World Economic Forum s Cyber Resilience Compass aims to help organizations learn how to successfully confront threats through sharing good practices Geneva Switzerland 13 January 2025 The World Economic Forum s Global Cybersecurity Outlook 2025 report released today highlights the increasing complexity in the cyber
[desc-10] [desc-11]

Cyberstalking Vs Traditional Stalking Pyspring
https://cropper.watch.aetnd.com/cdn.watch.aetnd.com/sites/4/2022/05/AE-True-Crime-Cyber-Stalking-GettyImages-165002209.jpg

Gangster Stalking Narcissistic Gang Stalkers Use Anonymity To Exploit
https://i.ytimg.com/vi/Na9fV6TCur4/maxresdefault.jpg

https://www.weforum.org › publications › unpacking-cyber-resilience
This white paper unpacks the concept of cyber resilience outlining the evolution of the cyber paradigm and establishes a concept of successful cyber resilience
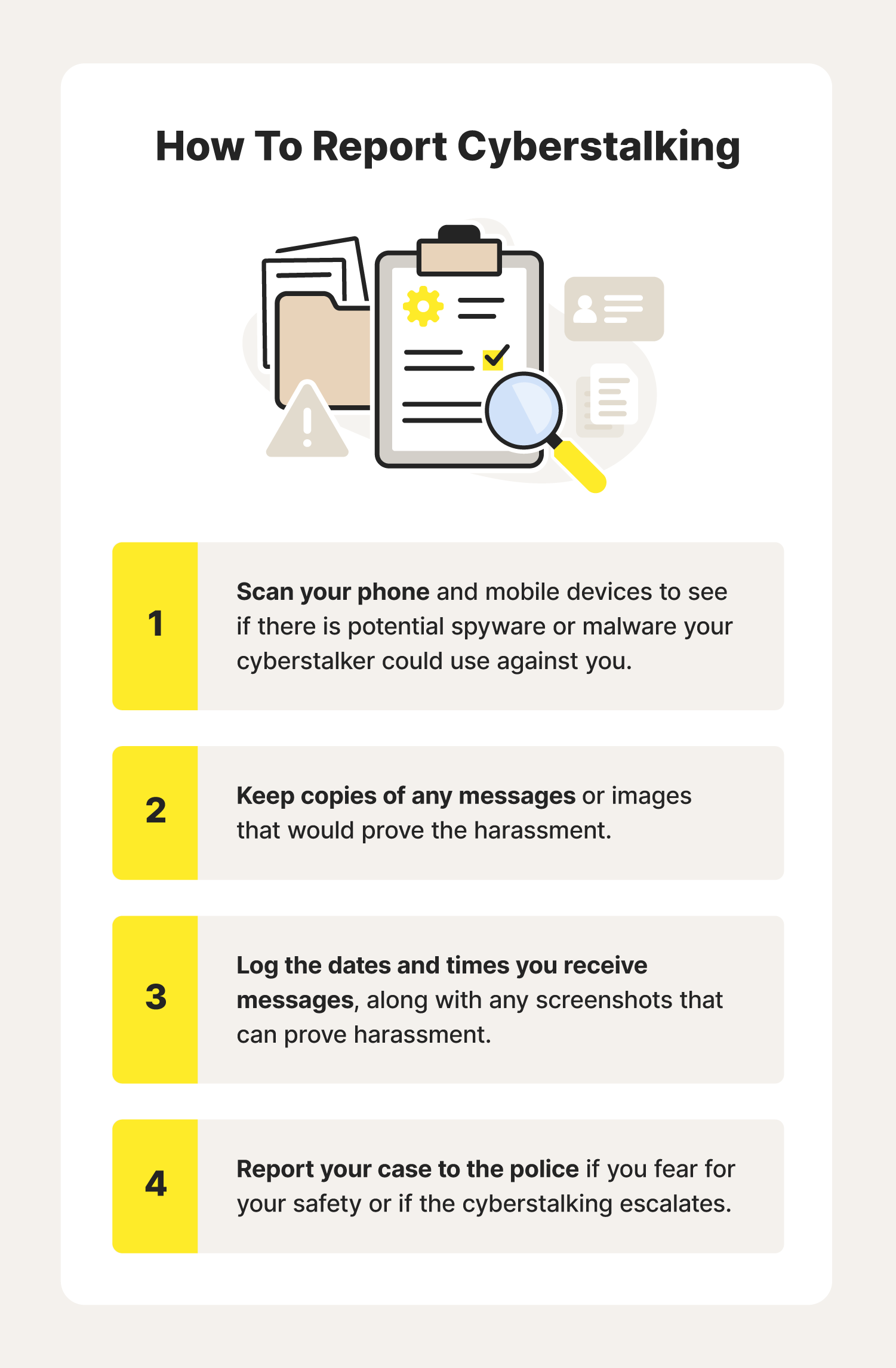
Cyber Stalkers

Cyberstalking Vs Traditional Stalking Pyspring
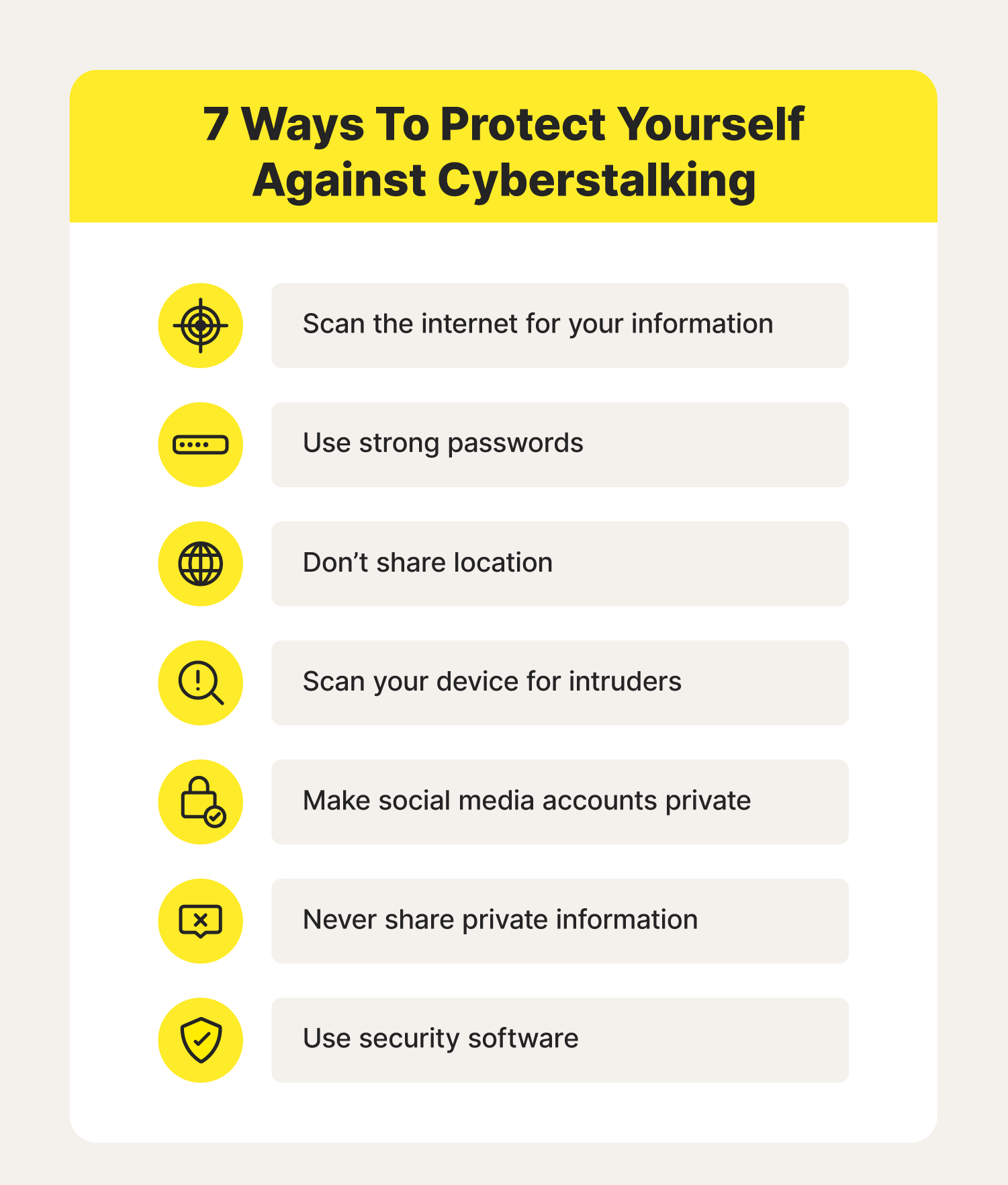
Cyberstalking Prevention

Stalker Person

Apa Itu Stalking Kepo Ya Info Hot Sex Picture
Hiding Lurker Man Mysterious Stalker Stalking Icon Download On
Hiding Lurker Man Mysterious Stalker Stalking Icon Download On

Is Cyberstalking A Crime What Makes You A Cyberstalker

Creeping On Facebook

Cybertruck 2025 Charlotte A Norton
What Is Cyber Stalking Give Example - Know the key insights tensions and trade offs that will likely shape the future of cybersecurity and can help an organization better prepare to face cyber threats