What Is The Need Of Security In Cryptography Need needs needs need needs need needs 1 need
Need needn t don t need needn t You needn t trouble about that don t need needs need need need
What Is The Need Of Security In Cryptography

What Is The Need Of Security In Cryptography
https://scaler.com/topics/images/cryptography.webp

Beginners Guide To Cryptography Quick
https://editor.analyticsvidhya.com/uploads/96092Untitledcc1.jpg
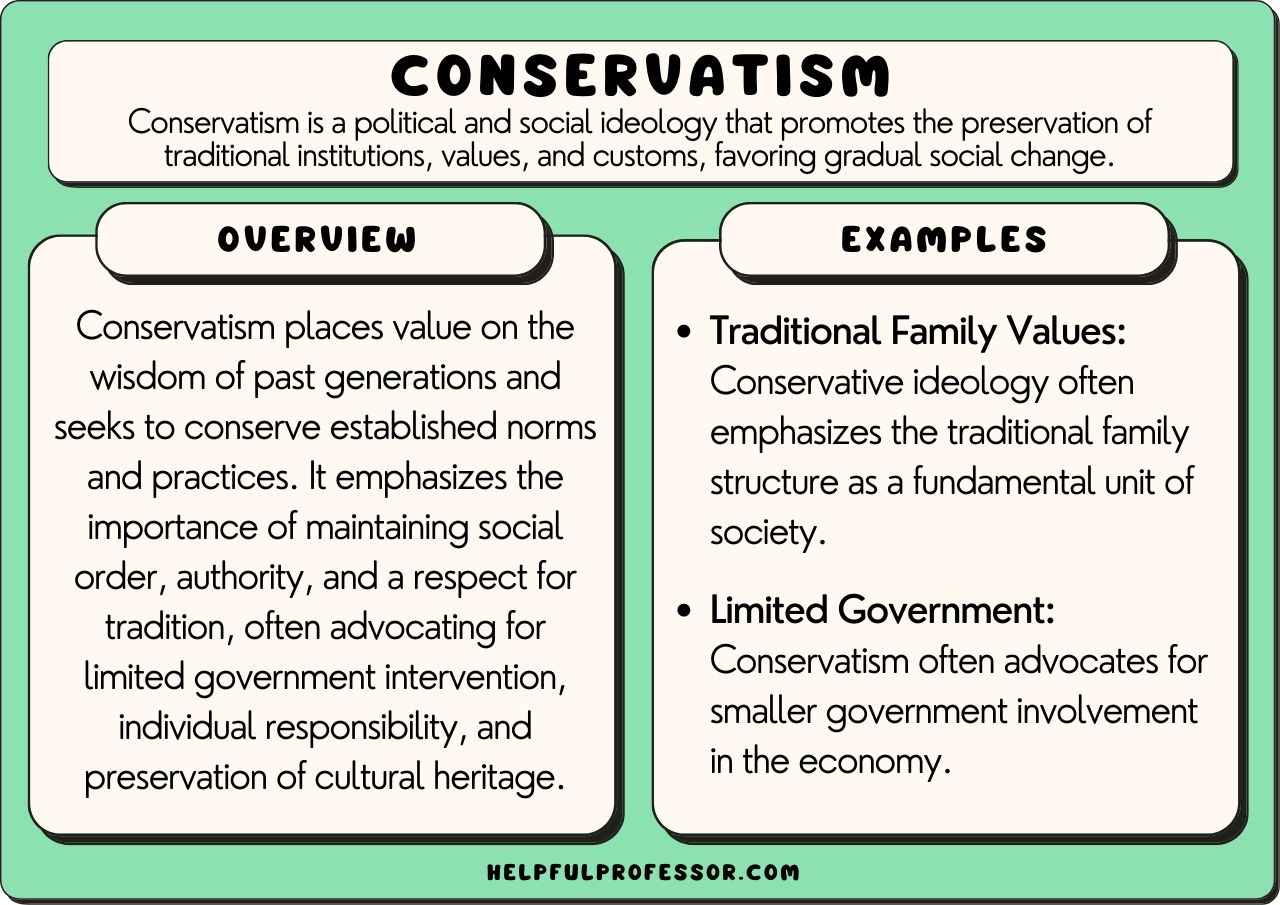
17 Conservatism Examples 2025
https://helpfulprofessor.com/wp-content/uploads/2022/09/conservatism-examples.jpg
Need for Need of Need for Be needed to do need to be donebe needed to do be needed in order to do A lot of time is needed to do this work
1 We need to collect the parcel before we leave for England 1 need to do 2 need doing 3 need to be done need ni d ni d need
More picture related to What Is The Need Of Security In Cryptography

What Is Cyber Security Benefits And More
https://www.marketwatchmedia.com/wp-content/uploads/2022/08/The-Benefits-of-Cyber-Security.jpg
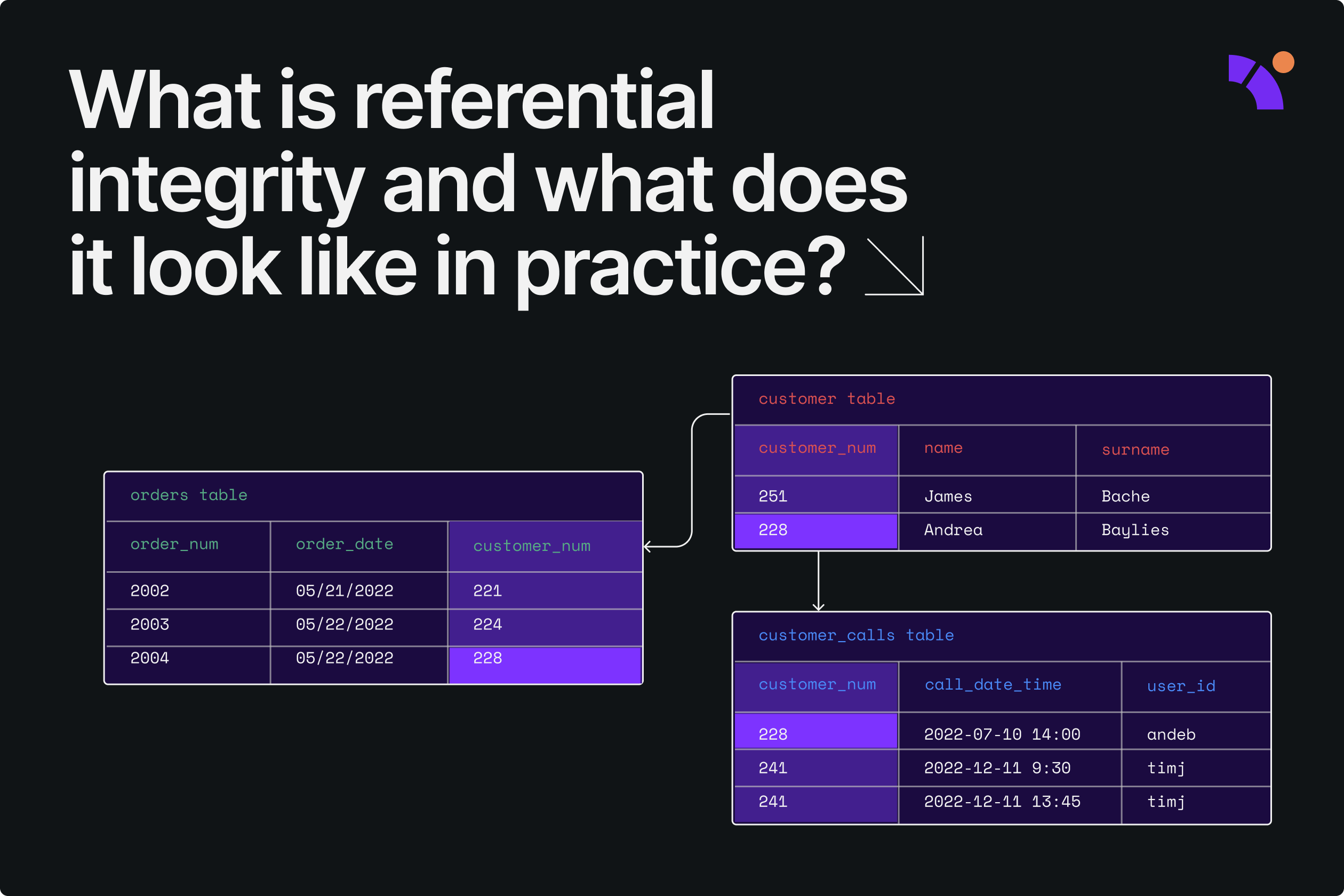
Integrity Examples
https://images.ctfassets.net/tlqfiok8qhck/18l3Un9B94nZklqpzlf6MO/6fd80732355411737d8cf3b16b5675bb/referential-integrity-banner.png
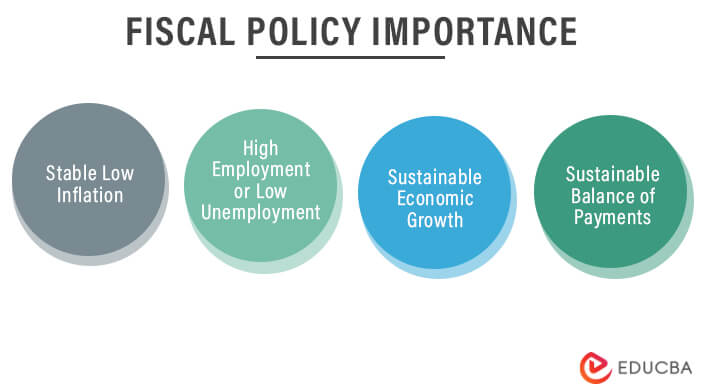
Fiscal Policy
https://cdn.educba.com/academy/wp-content/uploads/2022/10/Fiscal-Policy-Importance.jpg
Need in need of be in need of sth need I am in need of money I need money Need need 1 need
[desc-10] [desc-11]

Network Security Images
https://cdn.educba.com/academy/wp-content/uploads/2019/04/What-is-Network-Security.jpg

13 Social Institutions Examples According To Sociology 2025
https://helpfulprofessor.com/wp-content/uploads/2022/10/social-institutions-1024x724.jpg

https://zhidao.baidu.com › question
Need needs needs need needs need needs 1 need

https://zhidao.baidu.com › question
Need needn t don t need needn t You needn t trouble about that don t need
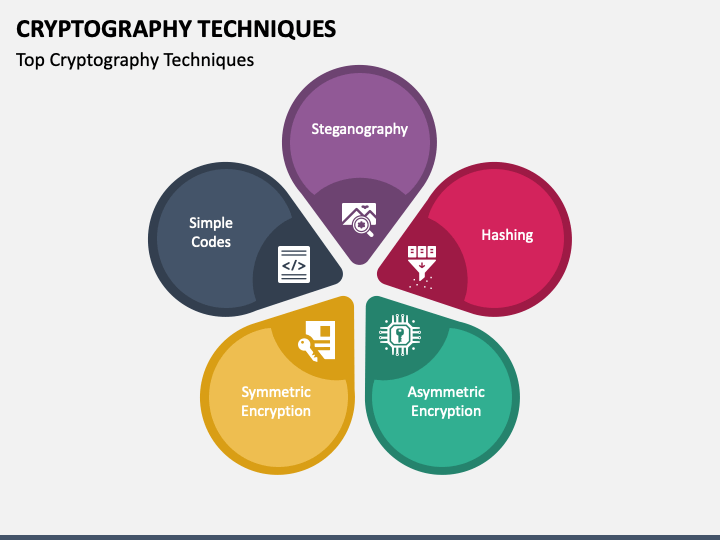
Cryptography Techniques PowerPoint And Google Slides Template PPT Slides

Network Security Images

How Proactivity Benefits Posture 4 Best Practices For Stronger

Public Key Cryptography Algorithms
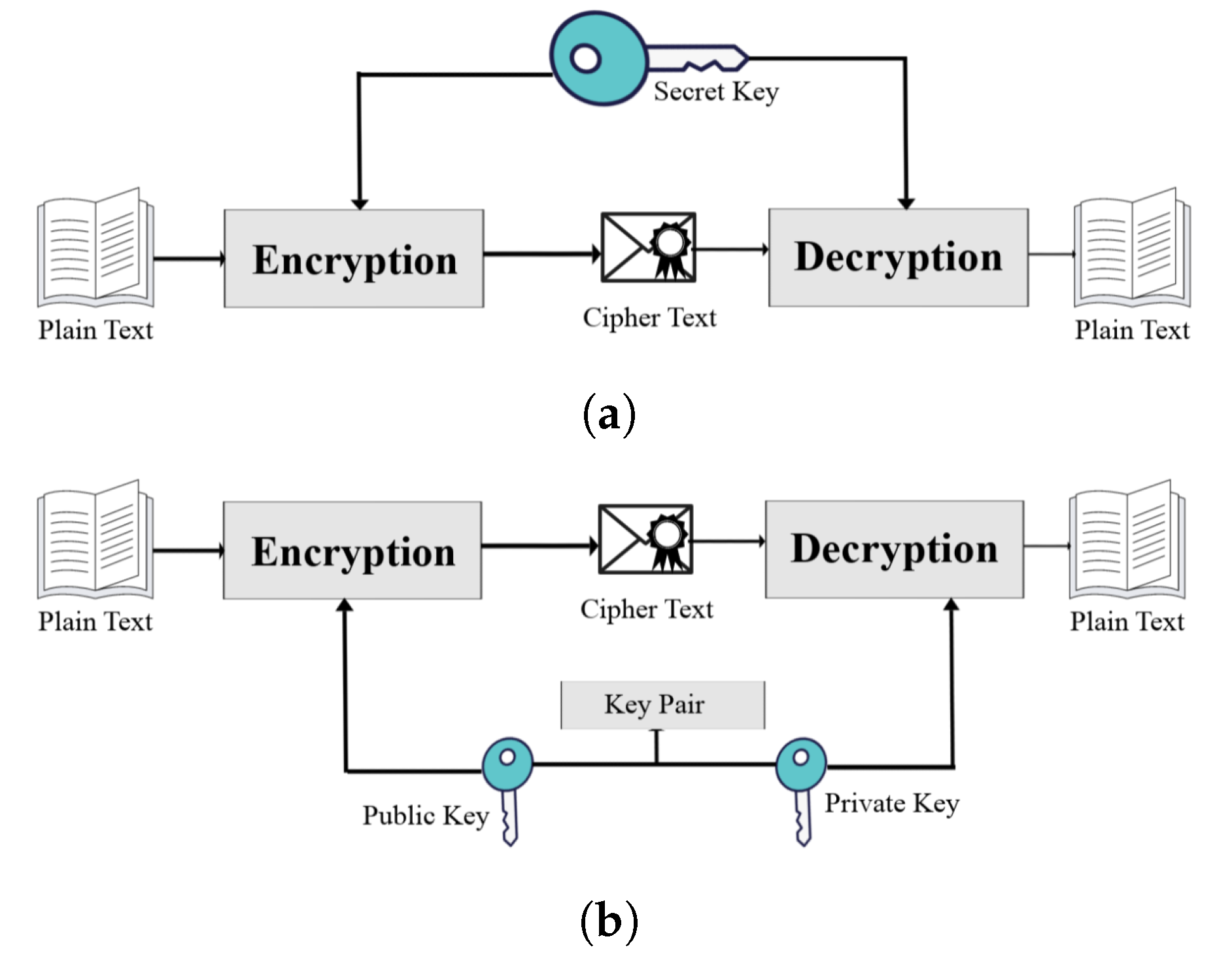
Public Key Cryptography Algorithms

INFIELES T 6 El Se or Del Fierro Ep 84 Parte 2 By Lizbeth Rodriguez

INFIELES T 6 El Se or Del Fierro Ep 84 Parte 2 By Lizbeth Rodriguez
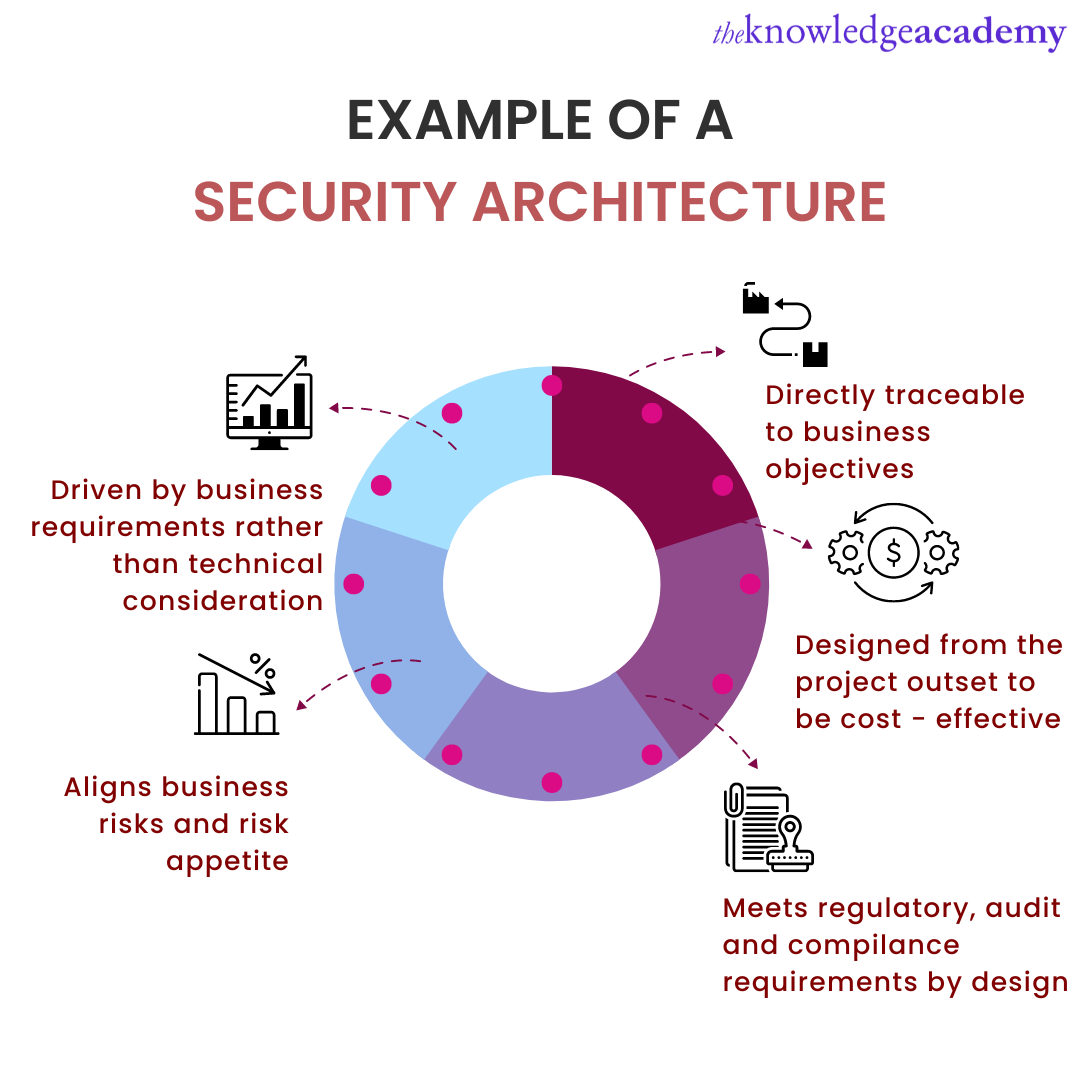
Cyber Security Architecture And Its Benefits

Common Encryption Types Protocols And Algorithms Expl Vrogue co
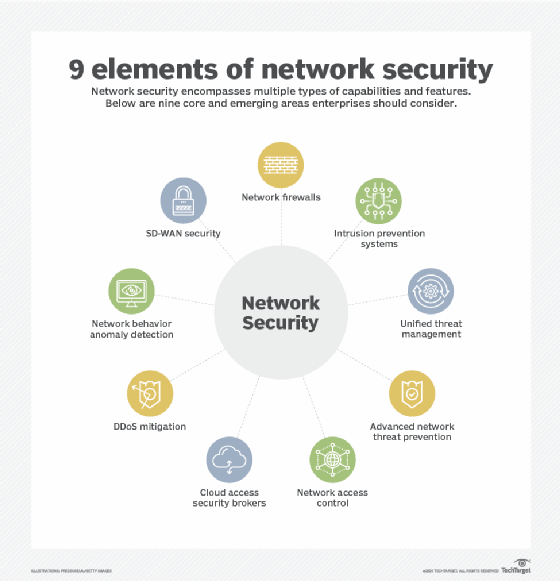
What Is Network Access Control NAC And How Does It Work
What Is The Need Of Security In Cryptography - 1 We need to collect the parcel before we leave for England