What Is Authentication And Authorization With Example cursor 5 cursor cursor Models Add Model
My professor used the word authentification in a lecture I have always used authentication Is it a real word or is authentication the correct term CURSOR sign in Can t verify t
What Is Authentication And Authorization With Example
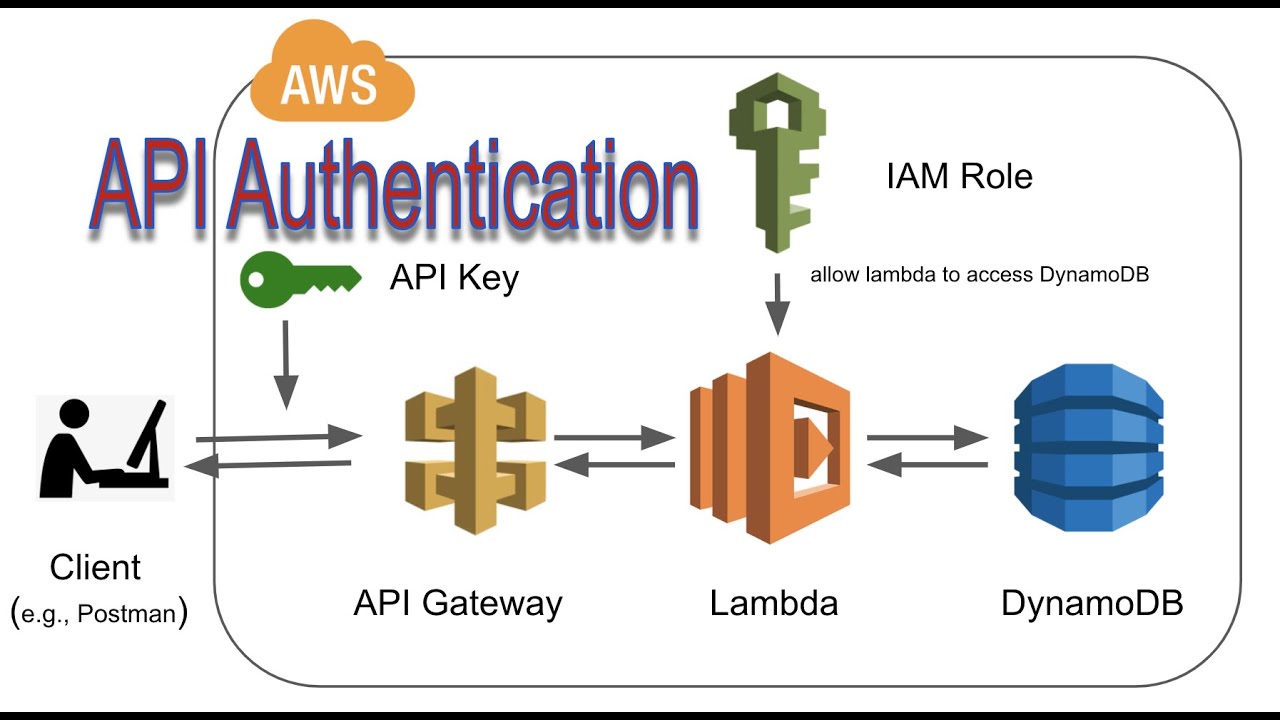
What Is Authentication And Authorization With Example
https://i.ytimg.com/vi/V-ac_ZvdAW4/maxresdefault.jpg

Confidentiality Integrity Availability Non Repudiation
https://i.ytimg.com/vi/K59Y3lbuU00/maxresdefault.jpg

Understanding Identification Authentication And Authorization In
https://i.ytimg.com/vi/vVN5YjU0eBw/maxresdefault.jpg
403 403 forbidden HTTP HTTP STATUS CODE authentication a12n authorization a11n The idea is to keep the first and last letters of the word and replace all of the interior letters with a number representing the count of the
23 Authentication is seen as entering the state of being authenticated An opposite of authentication would essentially mean entering the state of being unauthenticated It is Apple ID
More picture related to What Is Authentication And Authorization With Example

Authenticate
https://www.iproov.com/wp-content/uploads/2021/09/best-authentication-methods-v3-ai-1.png

Authentication Authorization HeadSec
https://rublon.com/wp-content/uploads/2021/10/howdoesauthwork2-1024x523.png

HTTP Request Authentication Diagram
https://www.researchgate.net/publication/294426154/figure/fig4/AS:337537219481601@1457486552465/Sequence-diagram-of-authentication-and-authorization-of-web-service-calls.png
Navicat MySQL 2059 authentication plugin caching sha2 password MySQL 8 APTCHA 1
[desc-10] [desc-11]

Common Auth
https://www.okta.com/sites/default/files/styles/1640w_scaled/public/media/image/2020-10/Authentication_vs_Authorization.png?itok=uBFRCfww
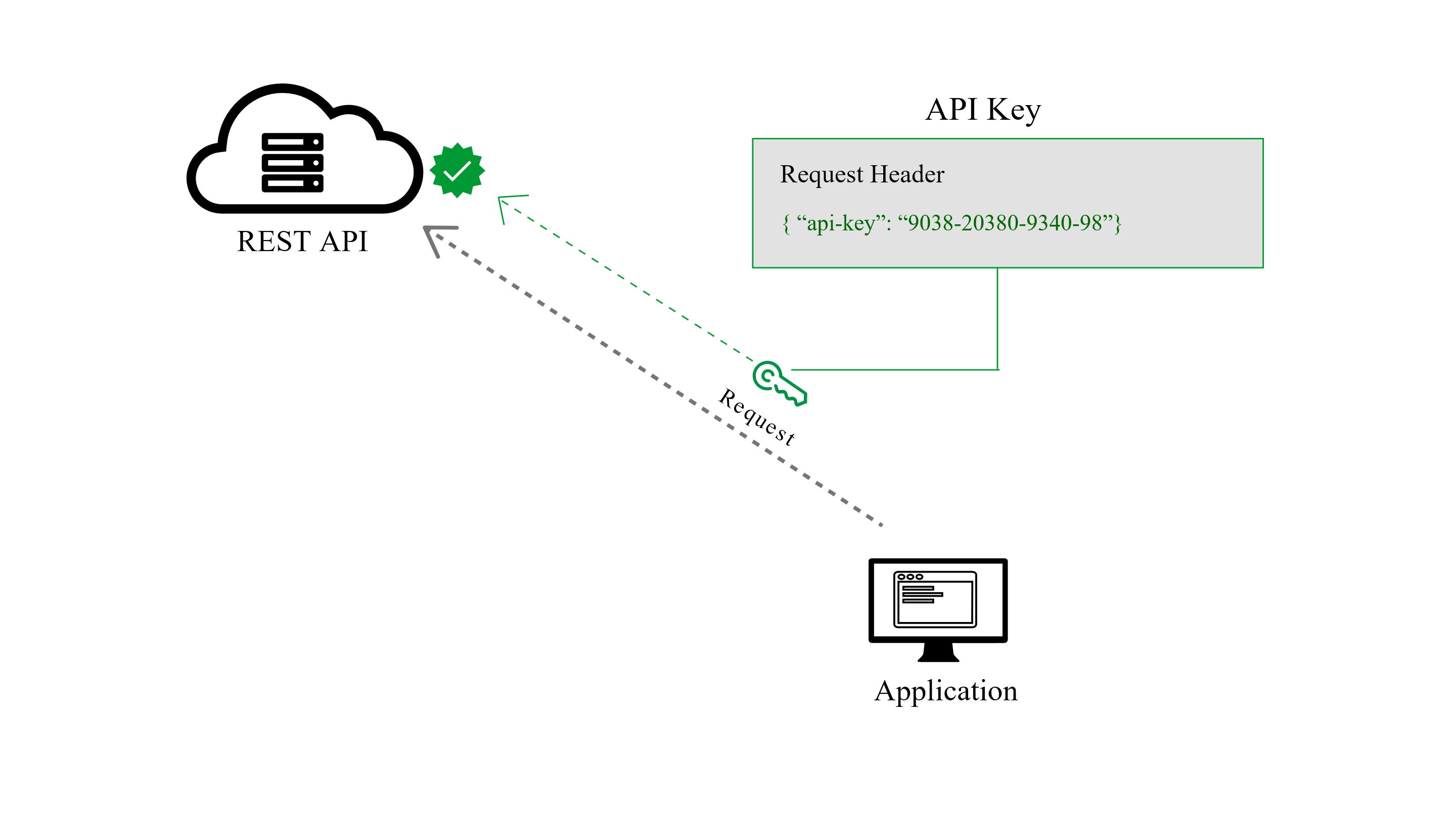
Rest Auth
https://blog.restcase.com/content/images/2019/07/nonref-docs-preso_apikey.png

https://www.zhihu.com › question
cursor 5 cursor cursor Models Add Model

https://english.stackexchange.com › questions
My professor used the word authentification in a lecture I have always used authentication Is it a real word or is authentication the correct term

Authentication Vs Authorization

Common Auth
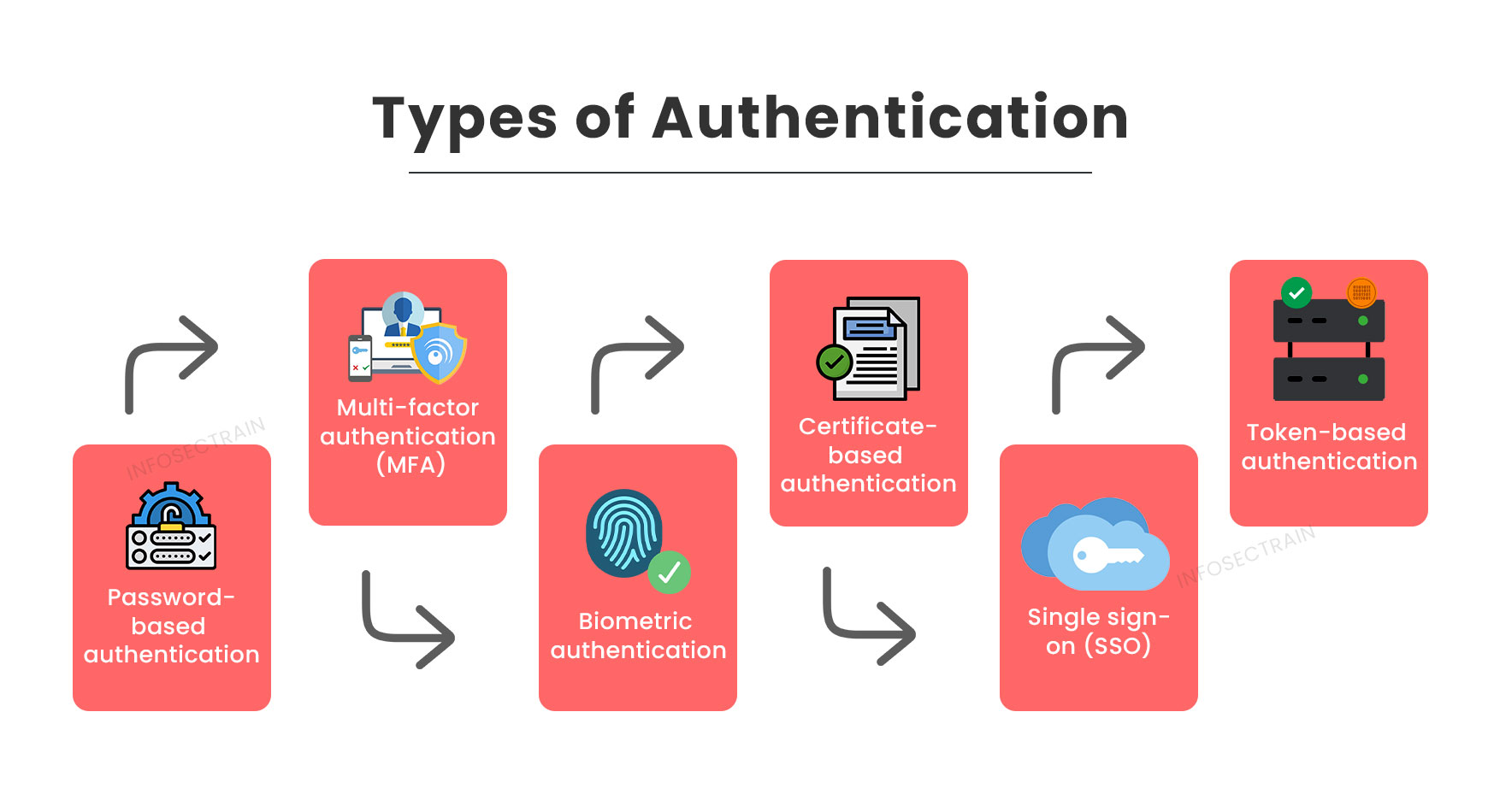
Authentication Acompanhe O EC S o Bernardo
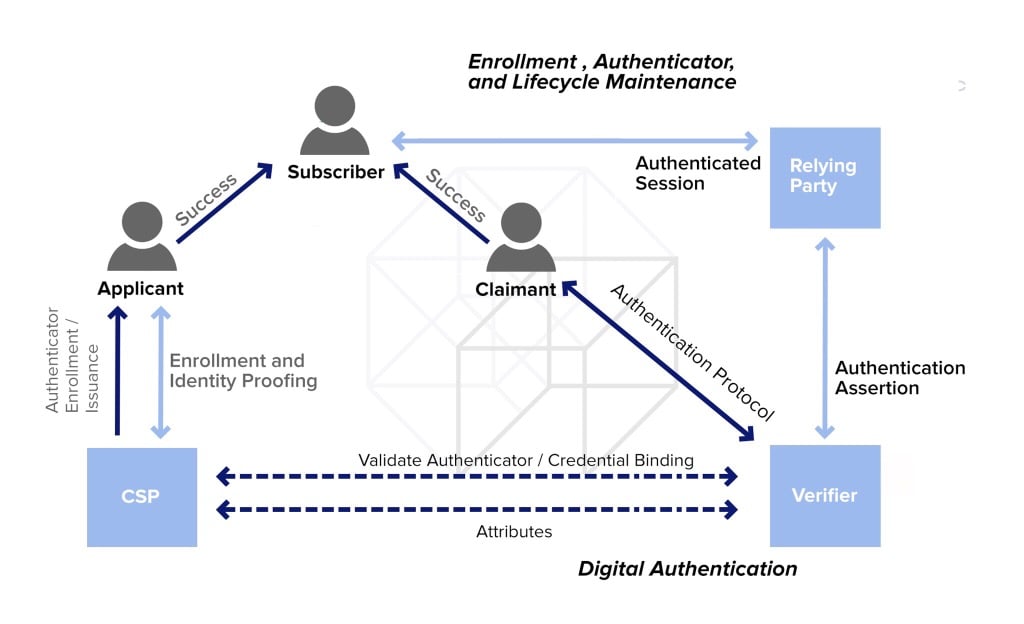
All About Image Authentication Analysis Biomeso

21 Free Authorization Letter Sample Example Best Letter Template
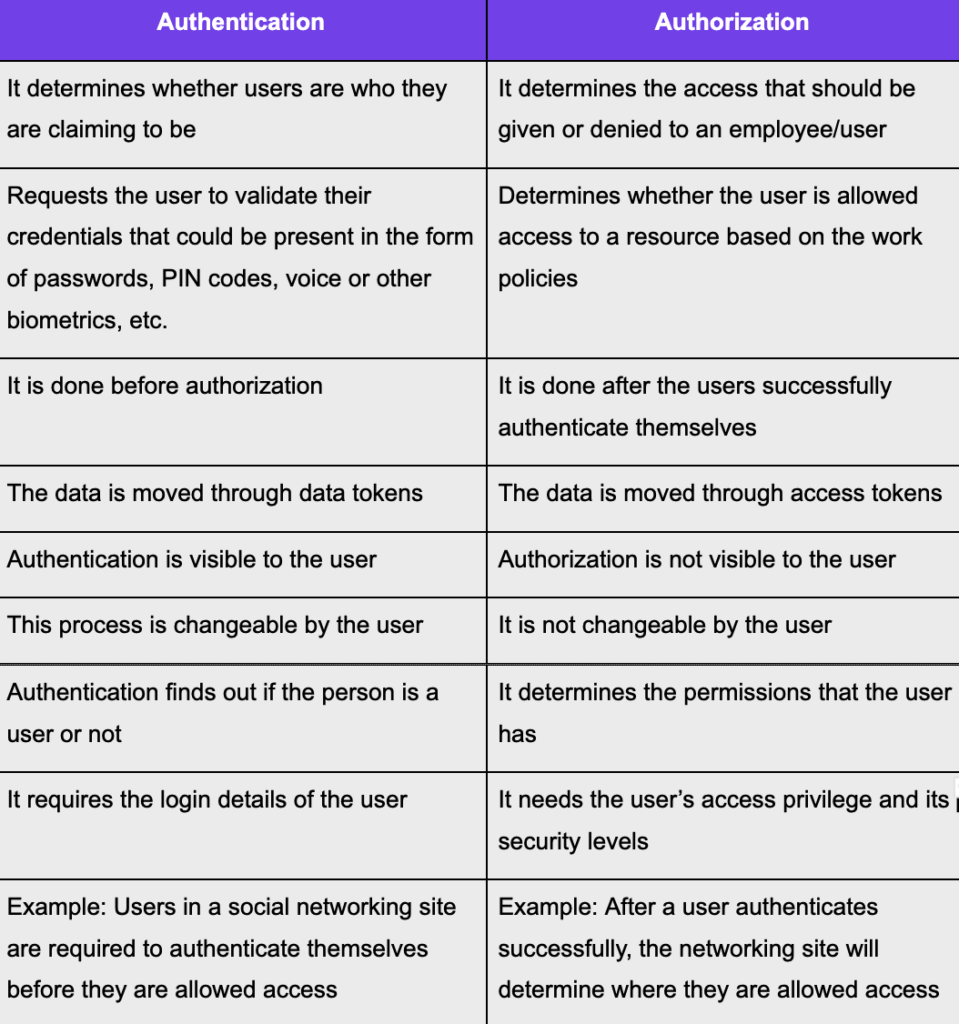
Authentication And Authorization

Authentication And Authorization
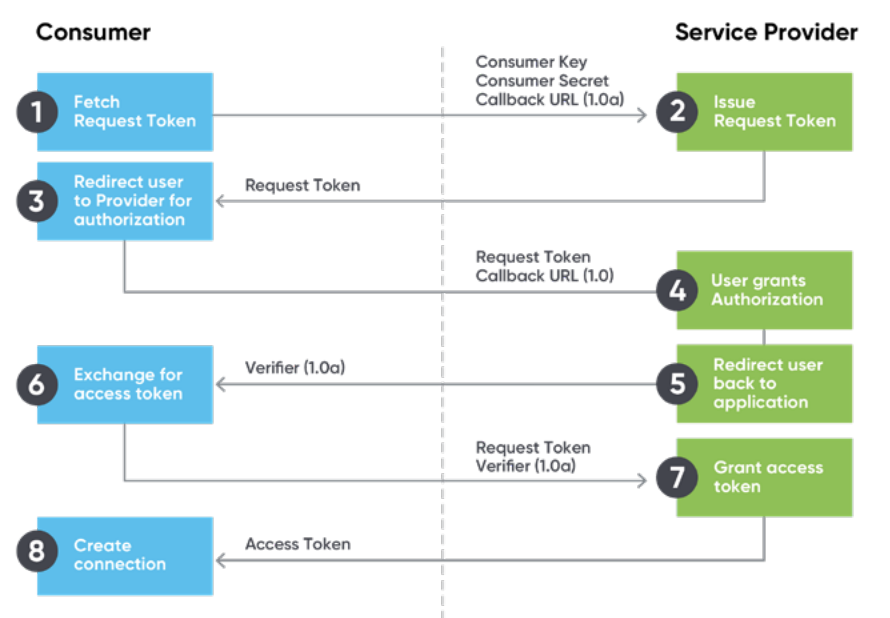
API Authentication Methods An Overview
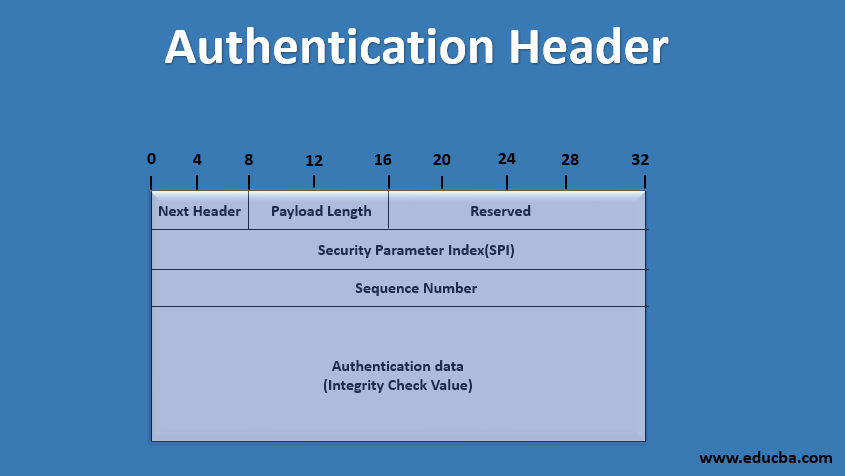
Authentication Header What Is Authentication Header 6 Formats
How To Get A Voided Check From Navy Federal Irving Sawyer
What Is Authentication And Authorization With Example - [desc-14]