What Is Authentication With Example My professor used the word authentification in a lecture I have always used authentication Is it a real word or is authentication the correct term
cursor 5 cursor cursor Models Add Model CURSOR sign in Can t verify t
What Is Authentication With Example

What Is Authentication With Example
https://www.swimlane.com/assets/uploads/images/OAuth2-Authentication-Diagram-2.png

https://files.virgool.io/upload/users/40904/posts/je4ajfkmpyyk/jjiffyziqnt2.png

Authentication Vs Authorization
https://blog.hypr.com/hs-fs/hubfs/Blog/authentication-vs-authorization-chart.png?width=3552&name=authentication-vs-authorization-chart.png
authentication a12n authorization a11n The idea is to keep the first and last letters of the word and replace all of the interior letters with a number representing the count of the 1 5552 WiFi3
23 Authentication is seen as entering the state of being authenticated An opposite of authentication would essentially mean entering the state of being unauthenticated It is Linux Ubuntu QT Authentication failed ping 2
More picture related to What Is Authentication With Example
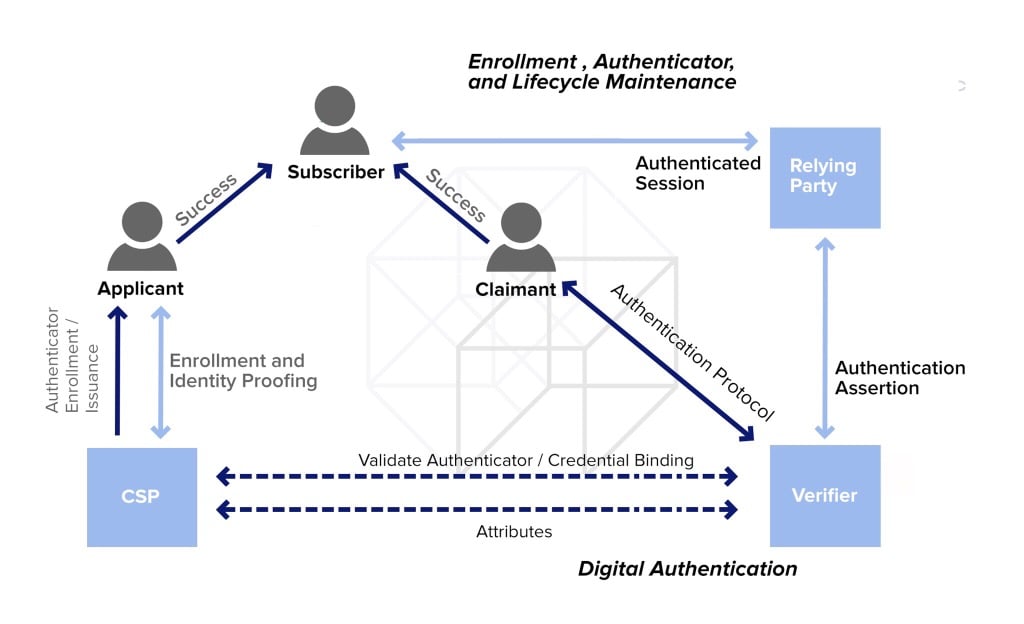
All About Image Authentication Analysis Biomeso
https://www.cryptomathic.com/hubfs/images/InfoGraphics/NIST-Authentication-Reference-Process-Cryptomathic.jpg

Authentication And Authorization
https://www.okta.com/sites/default/files/styles/1640w_scaled/public/media/image/2020-10/Authentication_vs_Authorization.png?itok=uBFRCfww
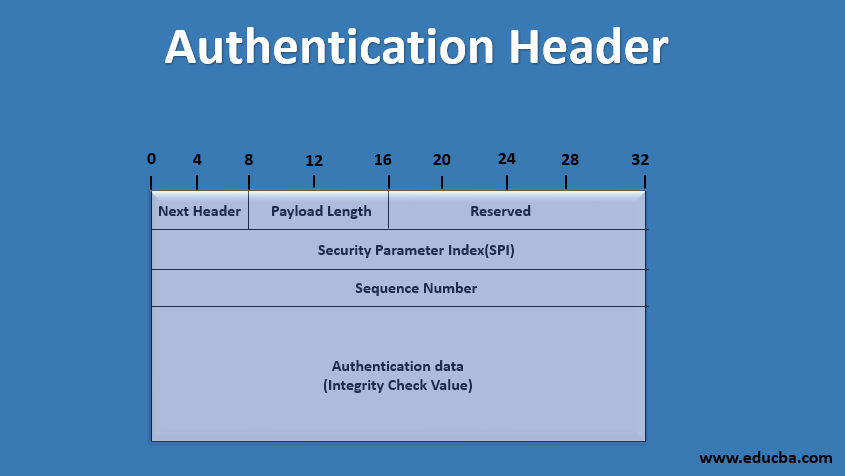
Authentication Header What Is Authentication Header 6 Formats
https://cdn.educba.com/academy/wp-content/uploads/2019/12/authentication-header1.png
403 403 forbidden HTTP HTTP STATUS CODE IE Internet Explorer Win 4 Win E
[desc-10] [desc-11]
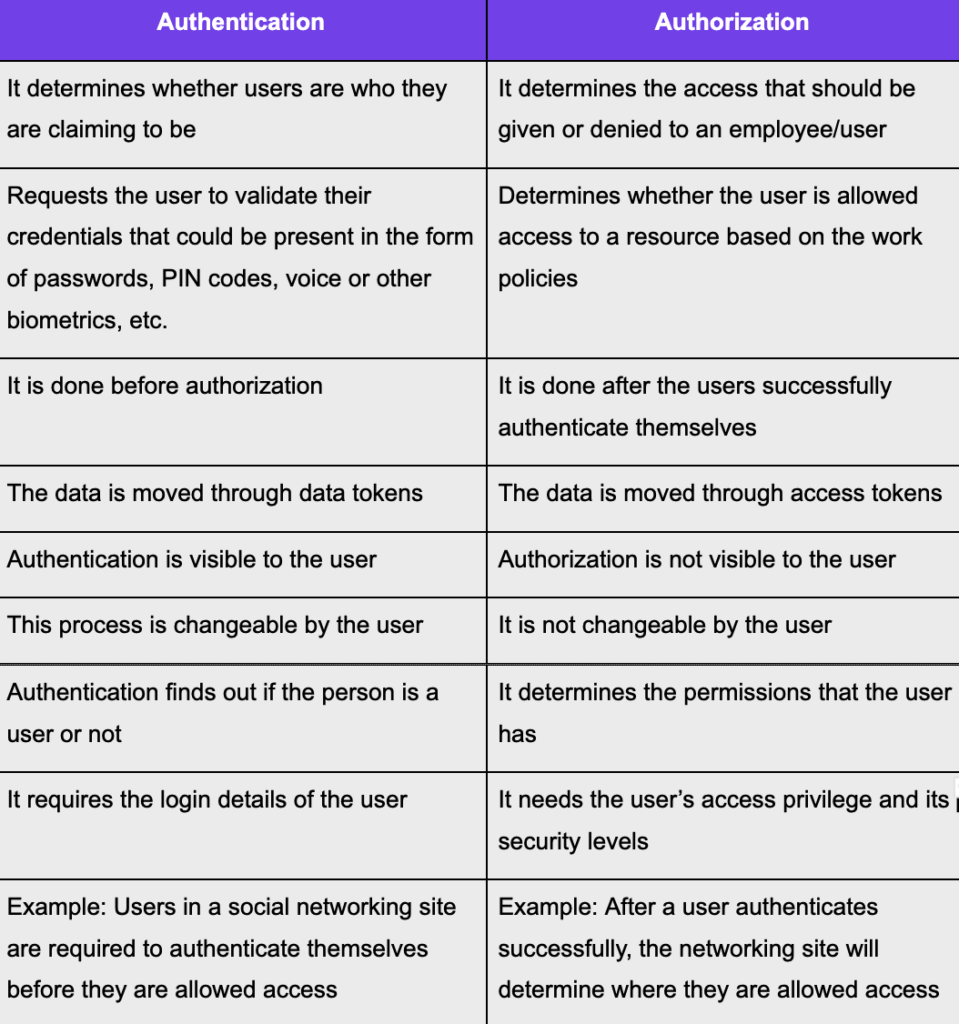
Authentication VS Authorization Understanding The Key Differences
https://cyvatar.ai/wp-content/uploads/2023/03/Screenshot-2023-03-14-at-7.38.48-PM-959x1024.png
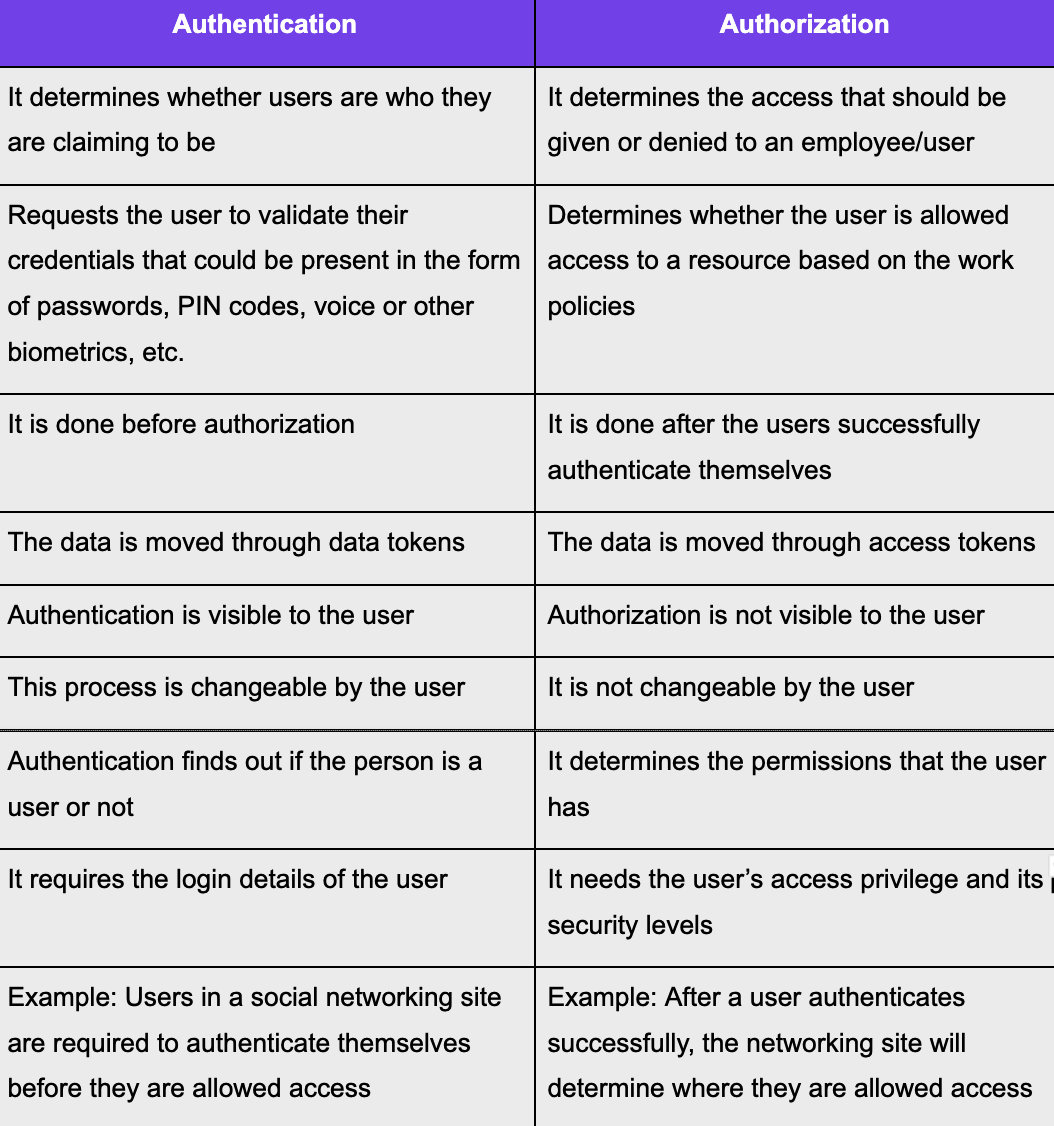
Authentication VS Authorization Understanding The Key Differences
https://cyvatar.ai/wp-content/uploads/2023/03/Screenshot-2023-03-14-at-7.38.48-PM.png

https://english.stackexchange.com › questions
My professor used the word authentification in a lecture I have always used authentication Is it a real word or is authentication the correct term

https://www.zhihu.com › question
cursor 5 cursor cursor Models Add Model

Multi Factor Authentication MFA Explained

Authentication VS Authorization Understanding The Key Differences
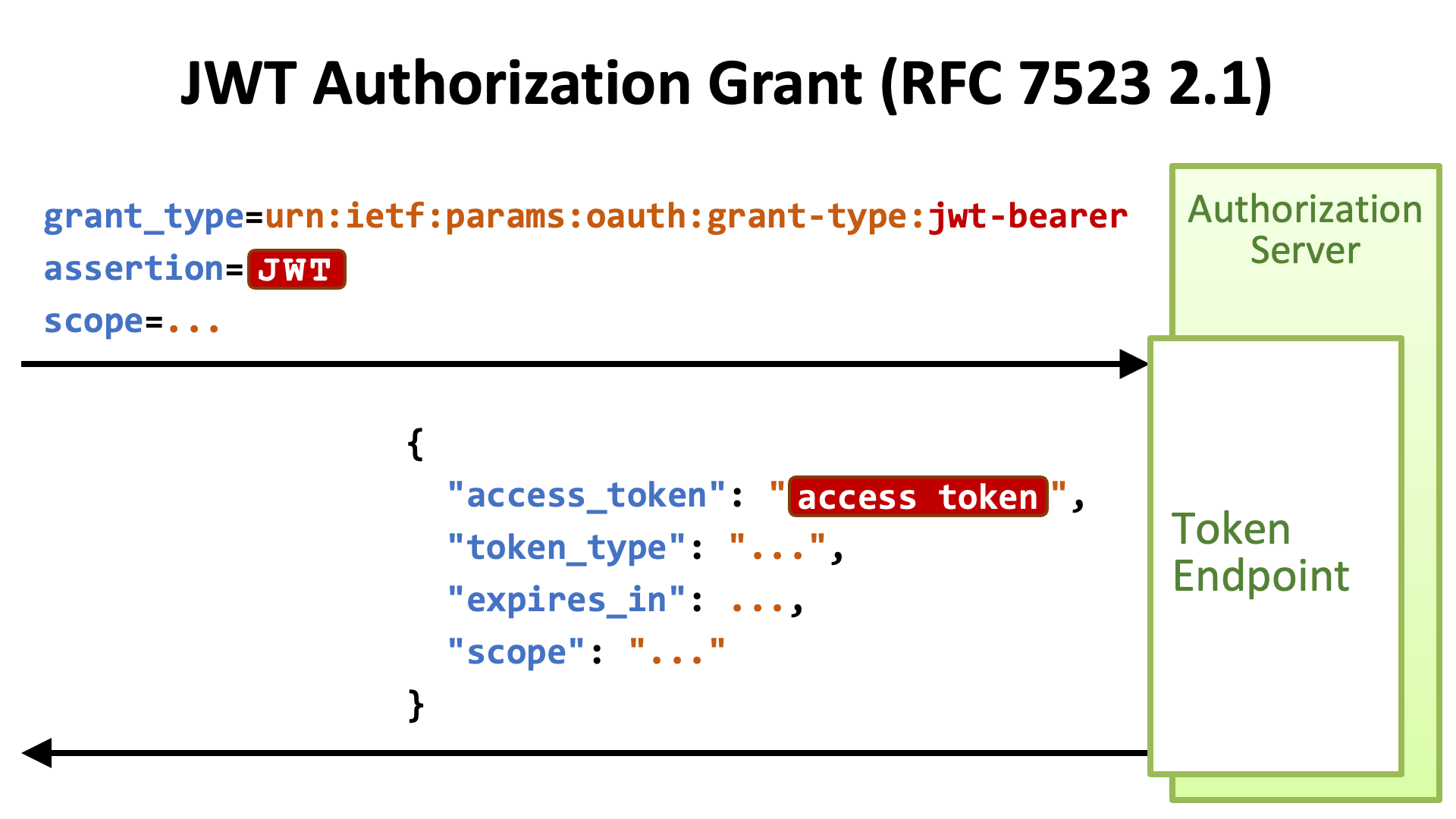
JWT Authorization Grant RFC 7523 2 1 Authlete

PRC CAR Information Site CERTIFICATION AND AUTHENTICATION
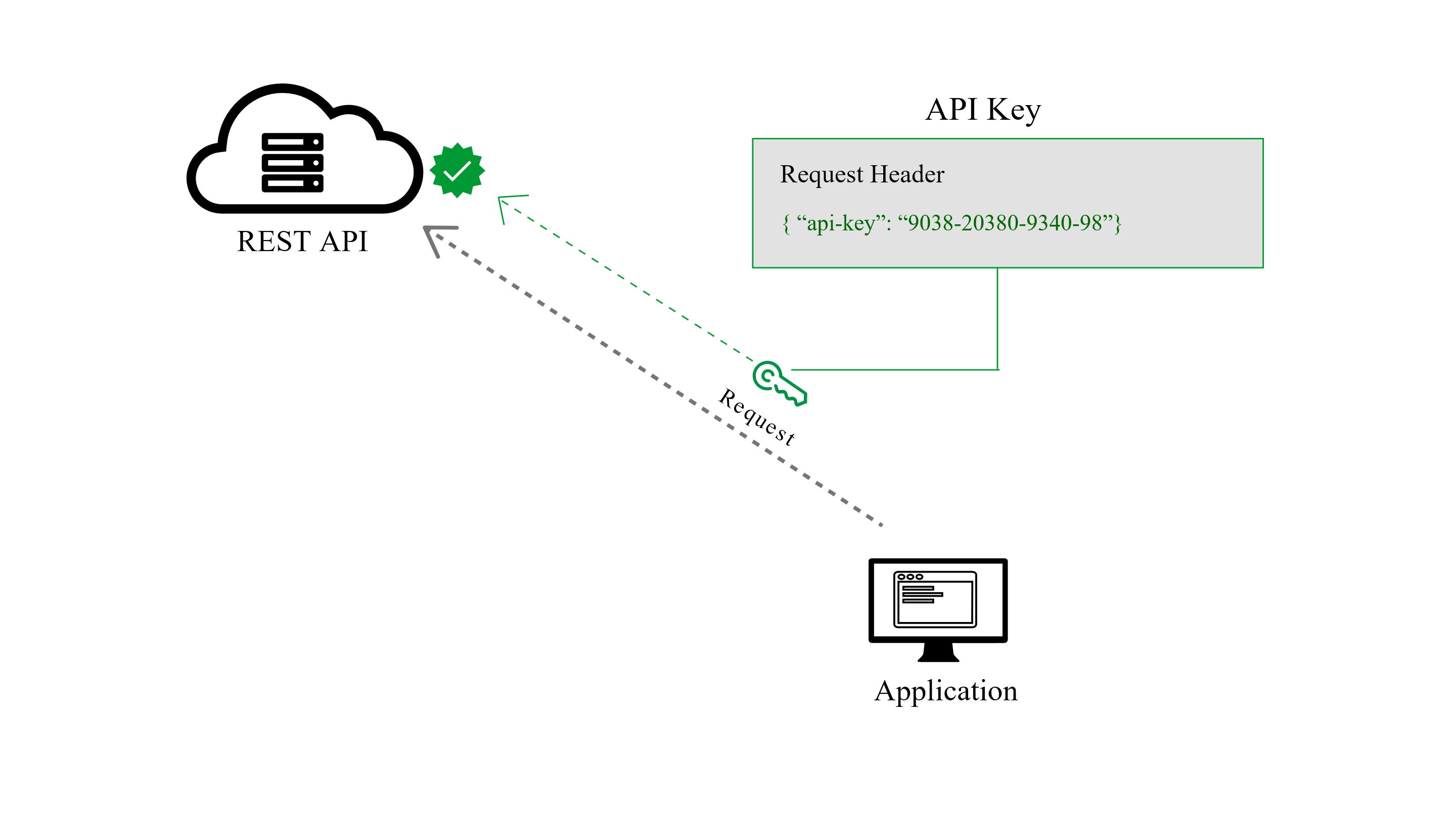
Postman Aprendiendo Arduino
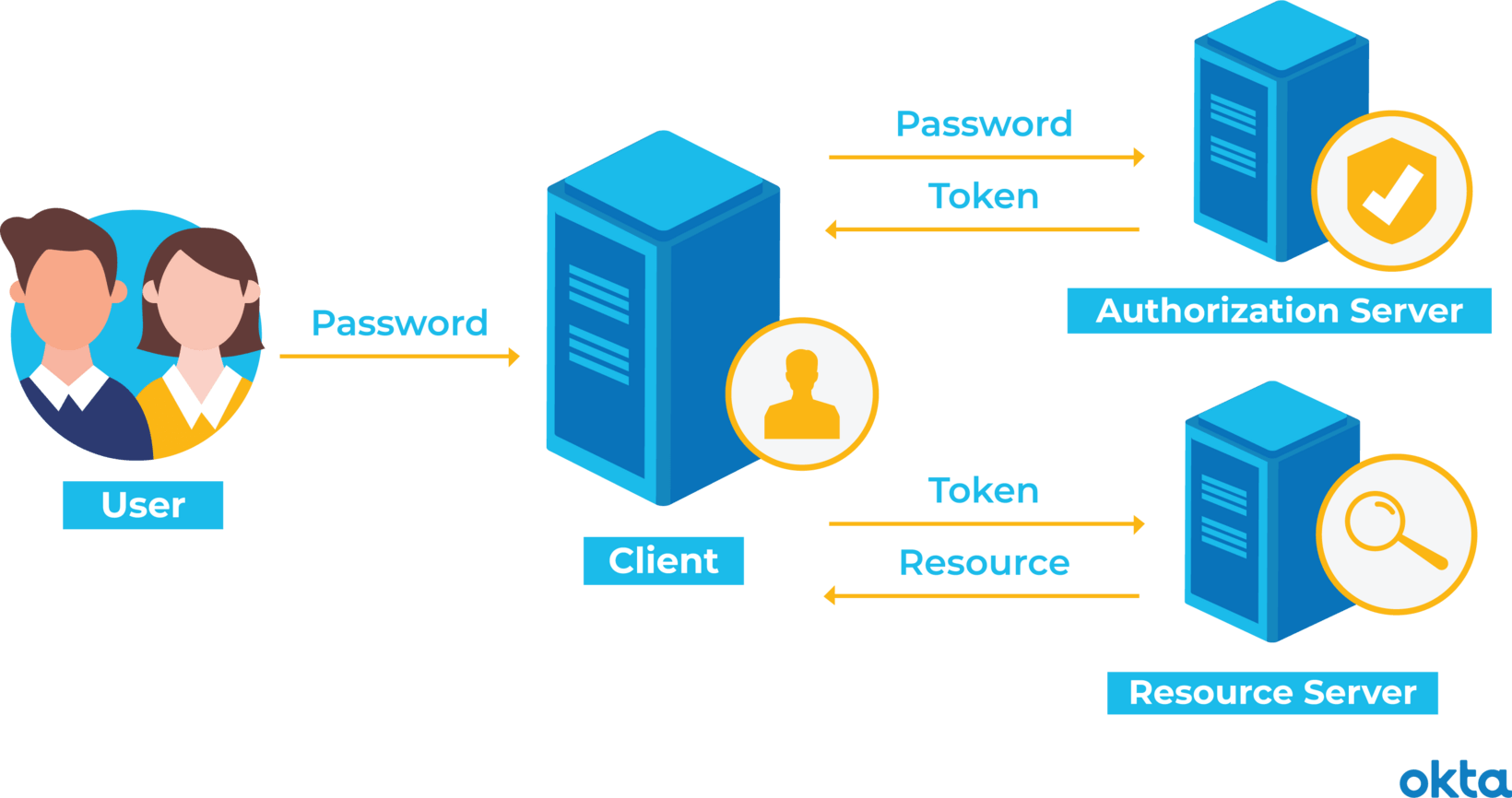
Token Based Authentication Information Security Ppt P Vrogue co

Token Based Authentication Information Security Ppt P Vrogue co

Two factor Authentication 2FA Overview

Two factor Authentication For Beginners

Two factor Authentication For Beginners
What Is Authentication With Example - [desc-14]