What Is Security Mechanism In Cryptography What is tokenization In data security tokenization is the process of converting sensitive data into a nonsensitive digital replacement called a token that maps back to the
IT security protects an organization s computer systems networks an digital data from unauthorized access data breaches cyberattacks and other malicious activity La seguridad inform tica protege los sistemas inform ticos las redes y los datos digitales de una organizaci n contra el acceso no autorizado las filtraciones de datos los ataques cibern ticos
What Is Security Mechanism In Cryptography

What Is Security Mechanism In Cryptography
https://i.ytimg.com/vi/e-ZwtnhSyFE/maxresdefault.jpg
Oscar oscar sercurityguard fbreelsb Paulo Pastera
https://lookaside.fbsbx.com/lookaside/crawler/media/?media_id=122197203374194856
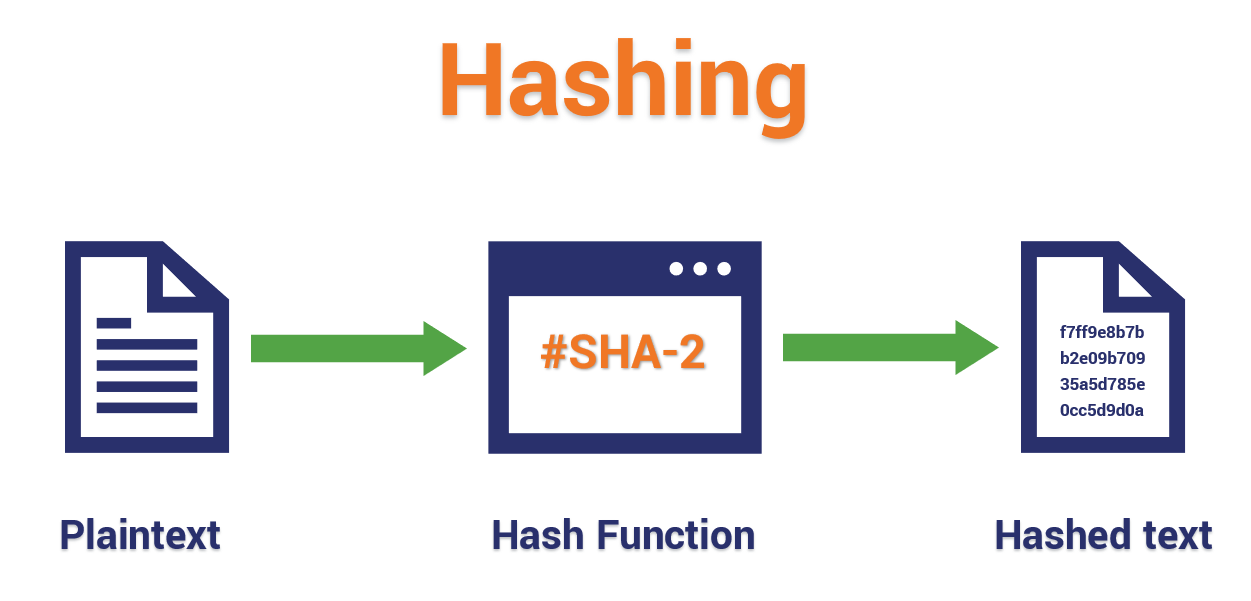
https://www.thesslstore.com/blog/wp-content/uploads/2018/12/Hashing-Example.png
Information security InfoSec is the protection of important information against unauthorized access disclosure use alteration or disruption API security is a set of practices and procedures that protect application programming interfaces APIs and the data they transmit from misuse malicious bot attacks
Most of us think of cybersecurity as a purely digital affair but cyberattacks can actually begin right here in the physical world Don t want to fork over 30 for a one year subscription to Windows 10 Extended Security Updates Microsoft is offering a couple of ways to avoid the fee But there is a catch
More picture related to What Is Security Mechanism In Cryptography

Cryptography FahrulRoup
https://scaler.com/topics/images/cryptography.webp

Beginners Guide To Cryptography Quick
https://editor.analyticsvidhya.com/uploads/96092Untitledcc1.jpg
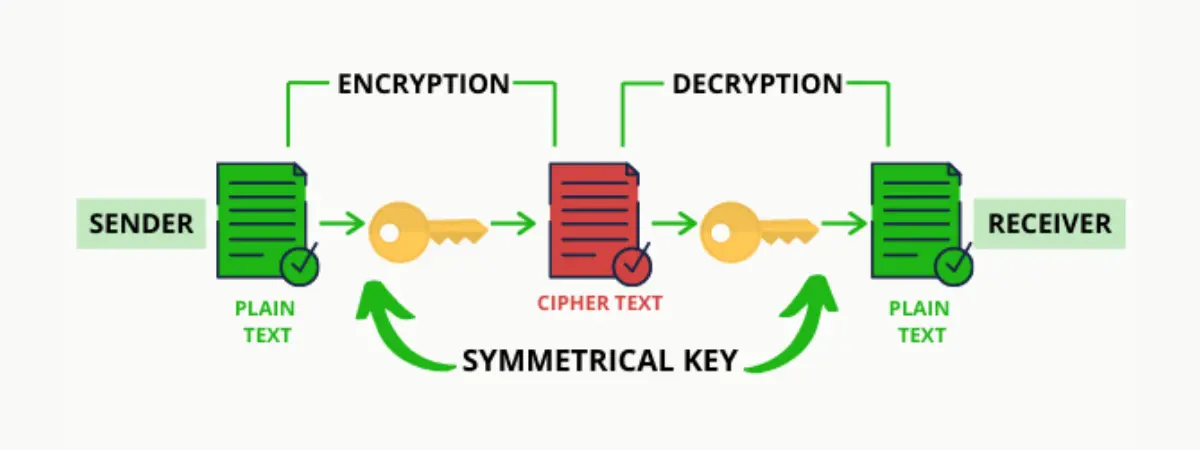
Beginners Guide To Cryptography Quick
https://101blockchains.com/wp-content/uploads/2021/04/Untitled-design-6.png
DevOps security or DevSecOps is a developmental approach where security processes are prioritized and executed during each stage of the software development ZDNET news and advice keep professionals prepared to embrace innovation and ready to build a better future
[desc-10] [desc-11]

Cryptography Simply Explained Bitcoinik
https://bitcoinik.com/wp-content/uploads/2019/05/crypt-graphy-1024x642.jpg
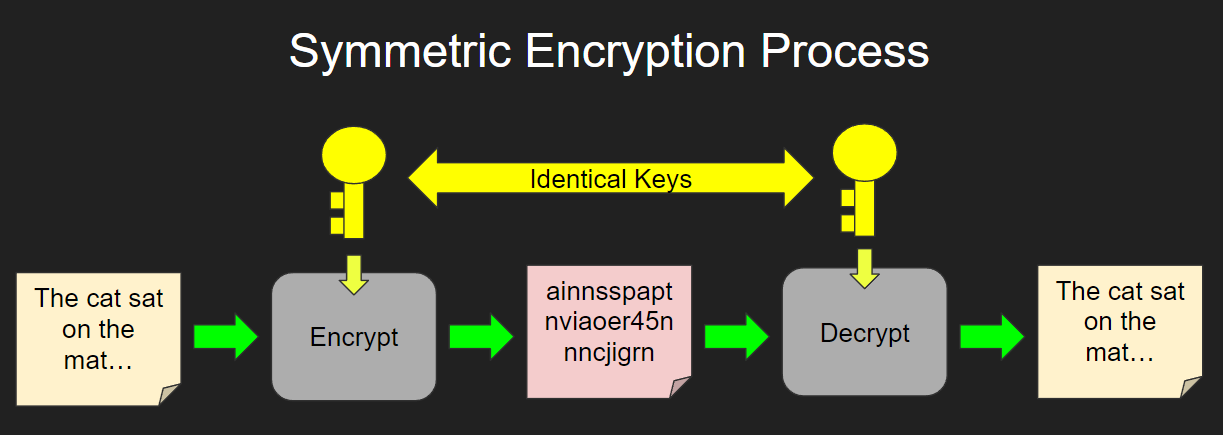
Symmetric Encryption IB Computer Science
https://learnlearn.uk/alevelcs/wp-content/uploads/sites/20/2022/03/symmetric-encryption-cie-alevel-computer-science-aqa.png

https://www.ibm.com › think › topics › tokenization
What is tokenization In data security tokenization is the process of converting sensitive data into a nonsensitive digital replacement called a token that maps back to the

https://www.ibm.com › think › topics › it-security
IT security protects an organization s computer systems networks an digital data from unauthorized access data breaches cyberattacks and other malicious activity
Cryptography Simply Explained Bitcoinik

Cryptography Simply Explained Bitcoinik

What Is Security By Design
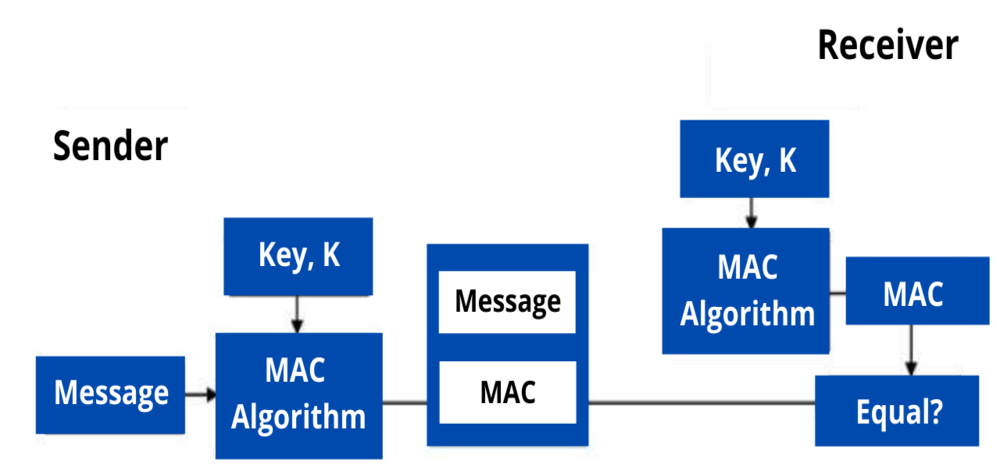
Message Authentication Code MAC In Cryptography UseMyNotes

Cryptography GiovanniIndio

Hash Function Cybersecurity Glossary Vrogue co

Hash Function Cybersecurity Glossary Vrogue co
Understanding Blockchain Security Looklify

Cryptography Basic Understanding Inviul

Is Quantum Cryptography Required Thinkbyte
What Is Security Mechanism In Cryptography - Don t want to fork over 30 for a one year subscription to Windows 10 Extended Security Updates Microsoft is offering a couple of ways to avoid the fee But there is a catch
