Types Of Security Policies In Information Security The Crossword Solver found 30 answers to place holder query for poll 5 letters crossword clue The Crossword Solver finds answers to classic crosswords and cryptic crossword puzzles
Answers for place holder query for quit poll quit crossword clue 6 letters Search for crossword clues found in the Daily Celebrity NY Times Daily Mirror Telegraph and major publications Check the balance Now both sides have 4 H atoms and 2 O atoms The equation is balanced Balancing with algebraic method This method uses algebraic equations to find the correct
Types Of Security Policies In Information Security

Types Of Security Policies In Information Security
https://safetytrainingandconsulting.ca/wp-content/uploads/2022/10/PPP.png

Musicloverwallpapersforandroid
https://s7280.pcdn.co/wp-content/uploads/2021/02/key-30.png

Citrus County Policies CREST
https://cdnsm5-ss19.sharpschool.com/UserFiles/Servers/Server_743215/Image/policy-shutterstock_359409938.jpg
We make use of Placeholder in forms to show data related to the entity For example let s say we have an EditUser page and form We are using Placeholder as an What is placeholder data Placeholder data allows a query to behave as if it already has data similar to the initialData option but the data is not persisted to the cache
If you want to add Poll below an existing block click on the Widgets and choose Ratings Under this you can drag and drop the Poll widget in editor Step 2 A poll with The REST end point I am hitting has a timestamp parameter which I need to use to poll the data from the endpoint I would like to update that parameter with every subsequent poll
More picture related to Types Of Security Policies In Information Security
10 Most Important Elements Of Information Security Policy Sprinto
https://sprinto.com/wp-content/uploads/2023/04/011.jpg

Cyber Security Policy Template
https://www.cm-alliance.com/hs-fs/hubfs/CTA_Images/CTA Images 1080 x 1080/Cybersecurity Policy Template Cover.png?width=2631&name=Cybersecurity Policy Template Cover.png
Security Policies List Of 6 Most Useful Security Policies
https://cdn.educba.com/academy/wp-content/uploads/2019/12/Security-Policies-1.jpg
This comes in handy for situations where you have enough partial or fake data to render the query successfully while the actual data is fetched in the background We are happy to announce that you can now use URL variables to dynamically display content in your survey URL variables are also called GET parameter query strings
[desc-10] [desc-11]
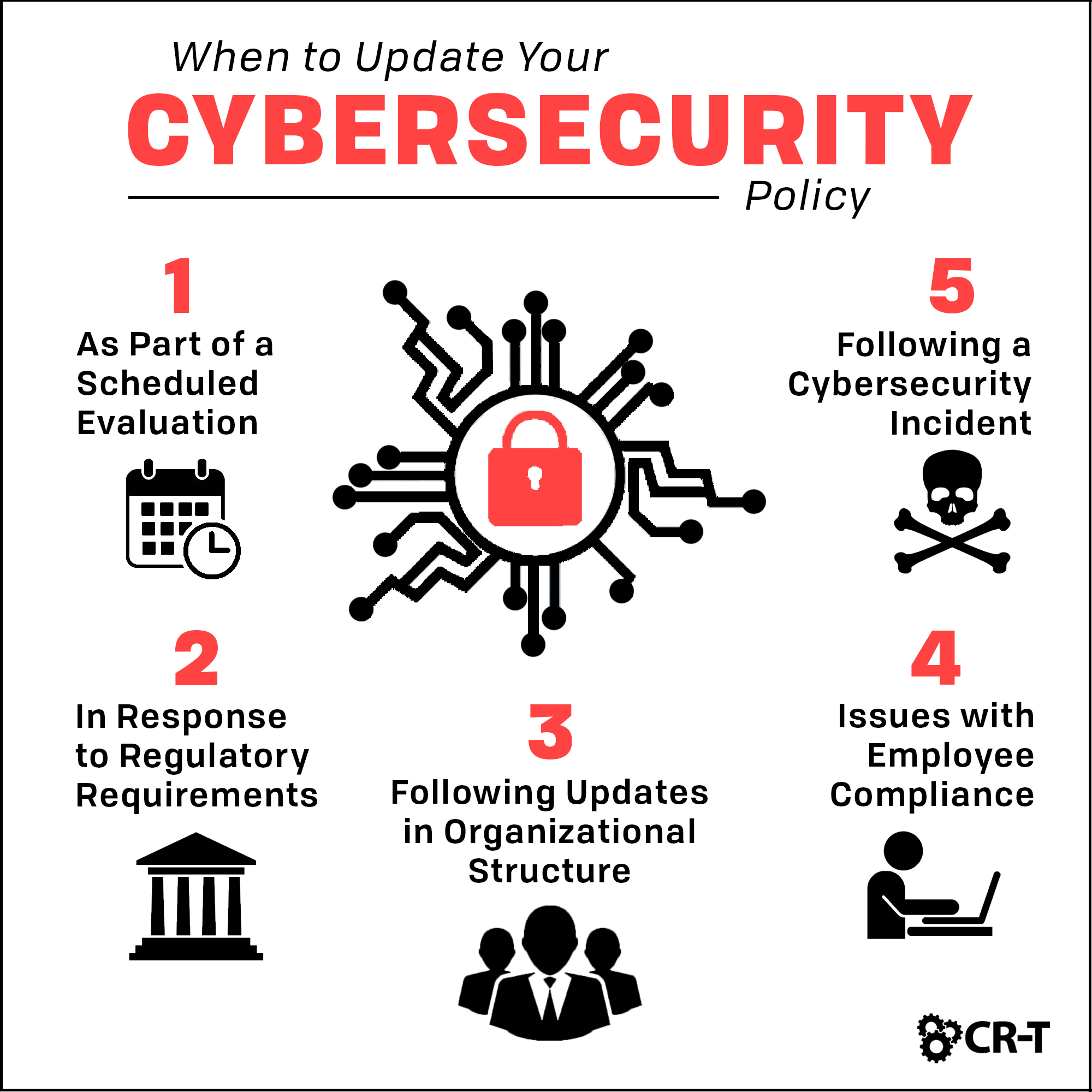
Cybersecurity Legislation 2024 Marty Shaylyn
https://www.cr-t.com/wp-content/uploads/2021/03/When-to-Update-Your-Cybersecurity-Policy-Infographic.jpg

Security Procedures Your Overall Security Documentation Library
https://linfordco.com/wp-content/uploads/2016/03/security-procedures.jpg?7ebf4b&7ebf4b

https://www.wordplays.com › crossword-solver › place-holder-query-fo…
The Crossword Solver found 30 answers to place holder query for poll 5 letters crossword clue The Crossword Solver finds answers to classic crosswords and cryptic crossword puzzles

https://www.wordplays.com › ... › place-holder-query-for-quit;poll-quit
Answers for place holder query for quit poll quit crossword clue 6 letters Search for crossword clues found in the Daily Celebrity NY Times Daily Mirror Telegraph and major publications
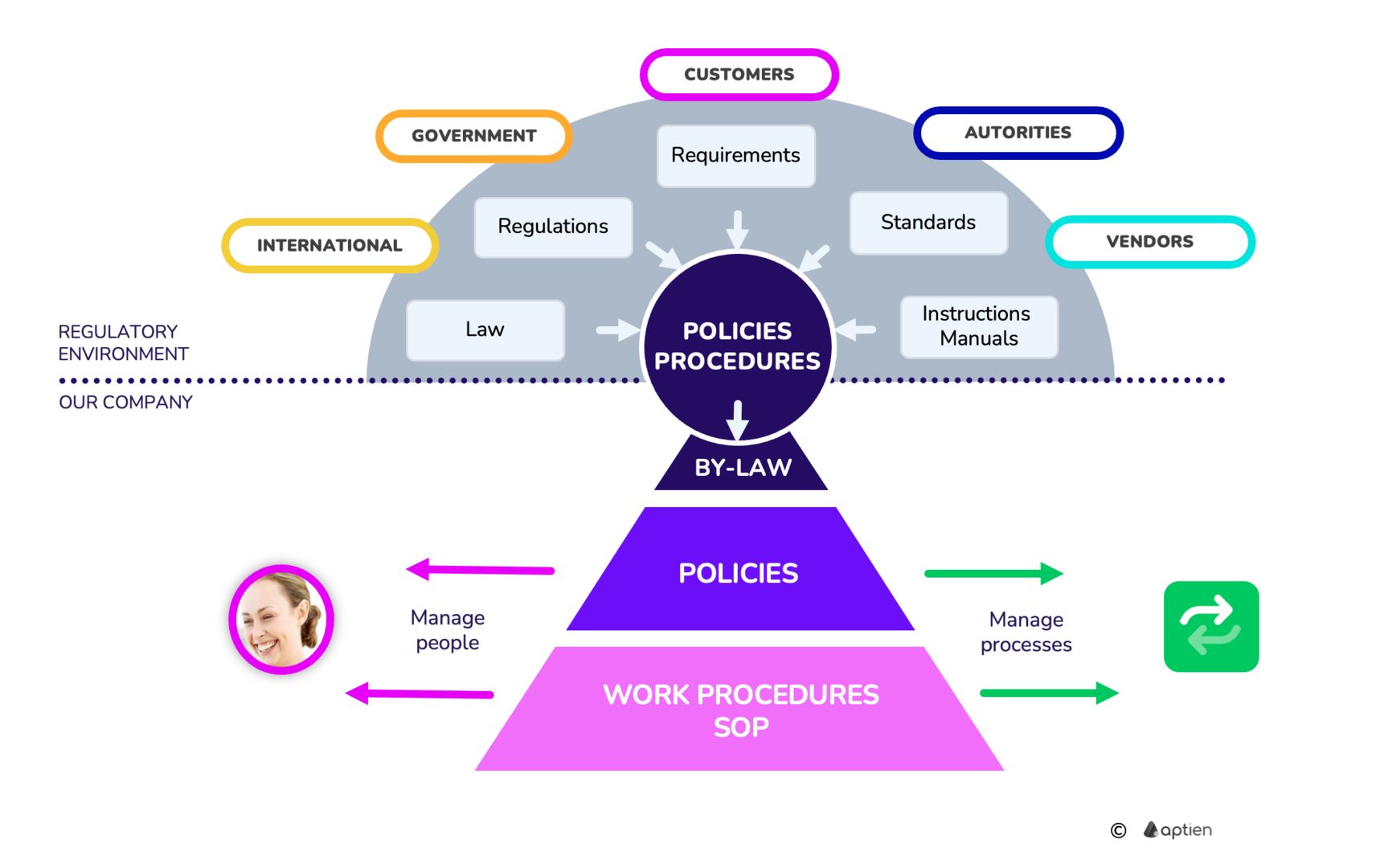
What Are Internal Company Policies GRC Glossary Aptien

Cybersecurity Legislation 2024 Marty Shaylyn
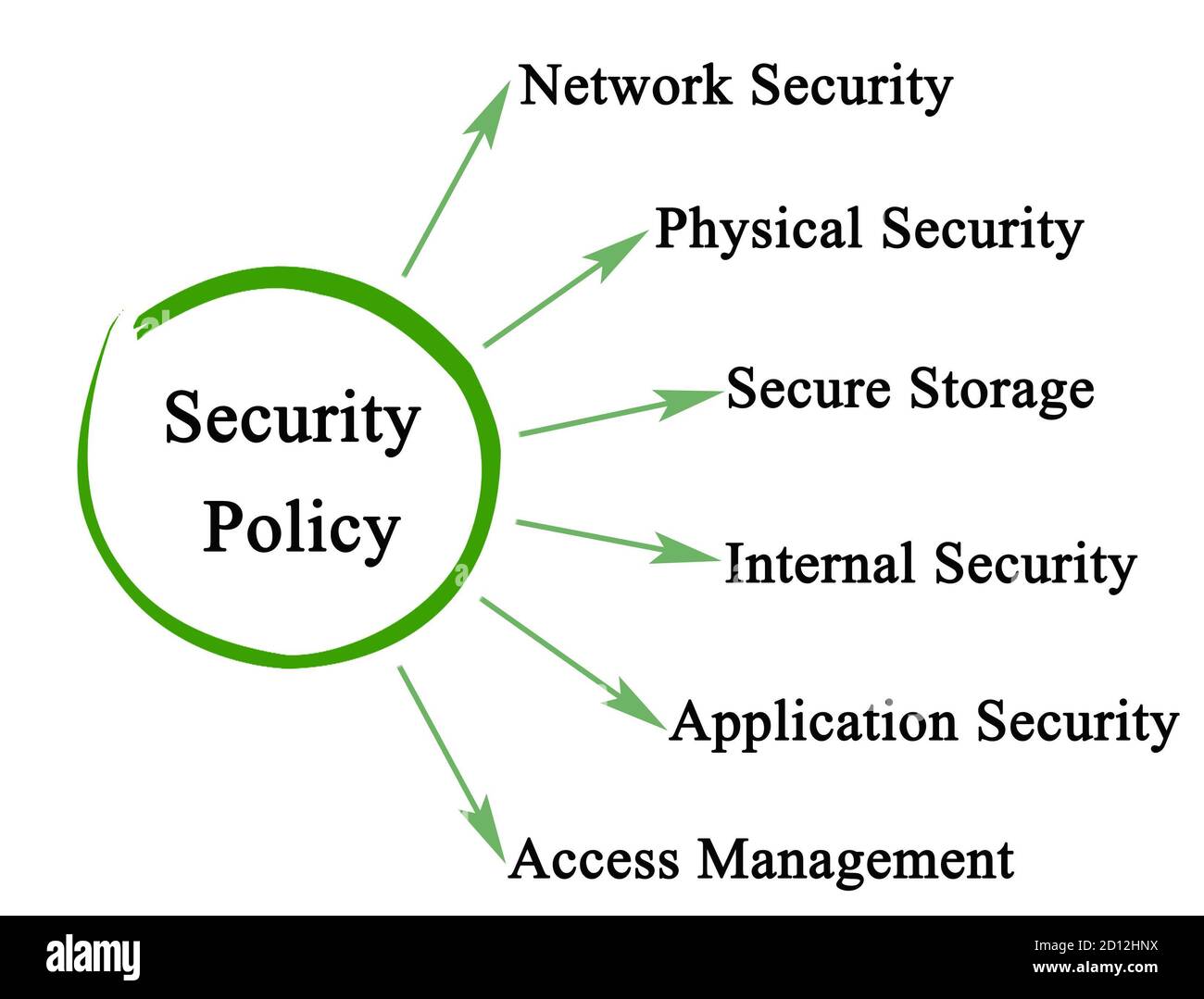
Six Types Of Security Policy Stock Photo Alamy
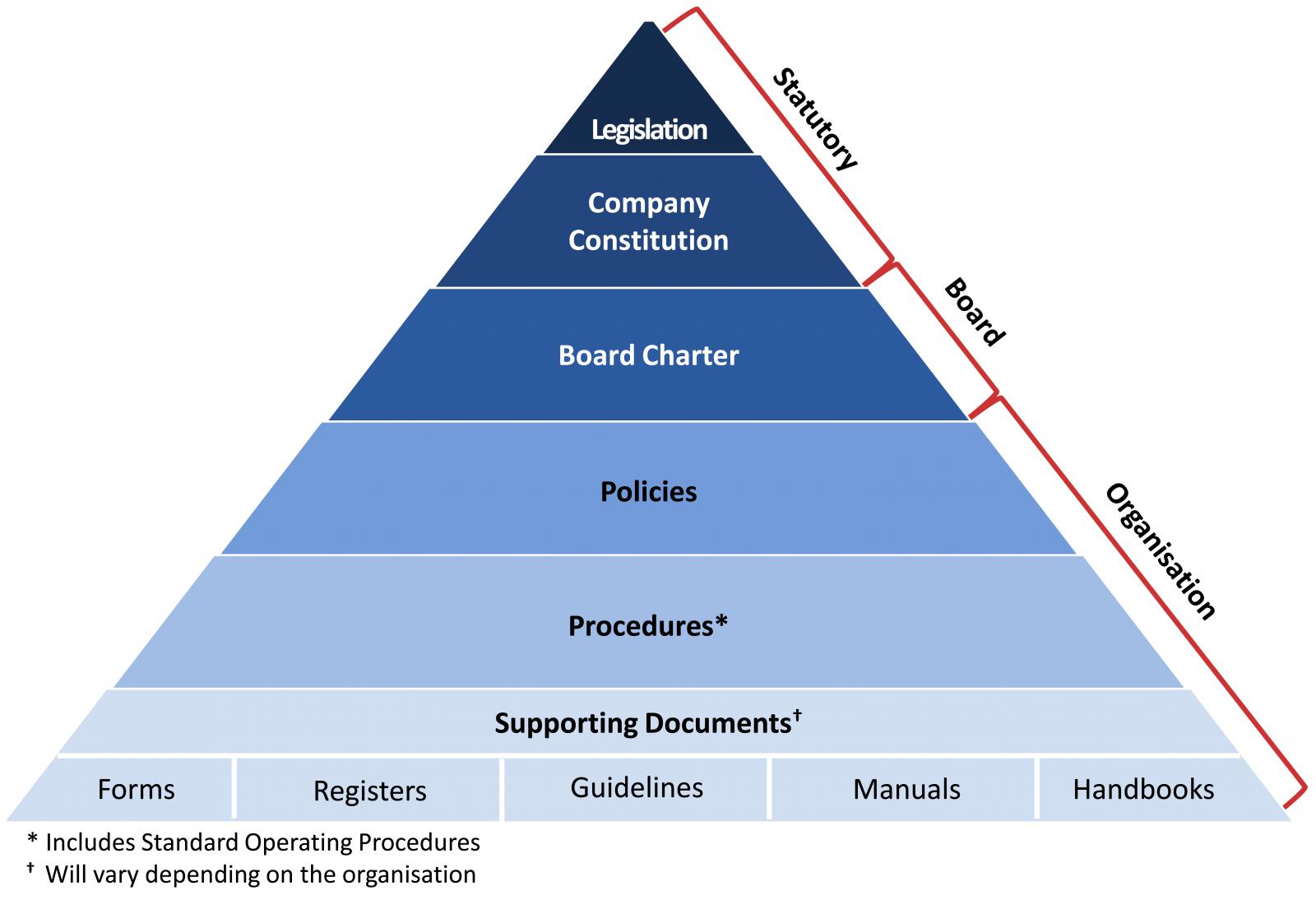
Data Governance Policy Template Prntbl concejomunicipaldechinu gov co
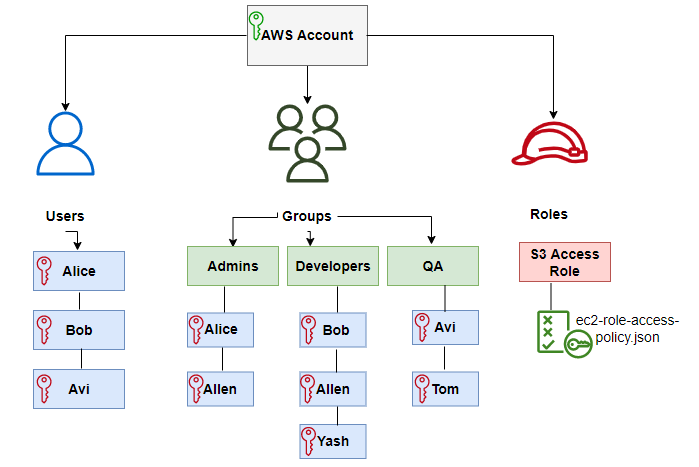
Aws IAM md At Main Gil son aws GitHub

25 Simplicity Pattern 1035 SaharaNusa

25 Simplicity Pattern 1035 SaharaNusa
Cyber Security CV Free Example Template Guide

Isms Policy Template Prntbl concejomunicipaldechinu gov co
Cybersecurity Plan Template
Types Of Security Policies In Information Security - The REST end point I am hitting has a timestamp parameter which I need to use to poll the data from the endpoint I would like to update that parameter with every subsequent poll