What Is Vulnerability In Cyber Security
Successful exploitation of this vulnerability requires an attacker to exhaust all the threads in the thread pool Thread Pool Thread In this case a Host Header IIS ASP NET
What Is Vulnerability In Cyber Security

What Is Vulnerability In Cyber Security
https://www.digitalregenesys.com/_next/image?url=https:%2F%2Fblog-api.digitalregenesys.com%2Fwp-content%2Fuploads%2F2024%2F09%2F12-july-24_Protect-your-Sensitive-Information-with-5-Pillars-of-Cyber-Security-1.jpg&w=750&q=75

What Is Vulnerability In Cyber Security Meaning Causes Types
https://www.finowings.com/admin/media/cybar-security.jpeg

What Is Vulnerability In Cyber Security Understanding Key Risks
https://www.digitalregenesys.com/_next/image?url=https:%2F%2Fblog-api.digitalregenesys.com%2Fwp-content%2Fuploads%2F2025%2F01%2F20-Jan-What-Is-Data-Privacy-Importance-Principles-and-Challenges.jpg&w=1920&q=75
p Microsoft Security Advisory 2416728 Vulnerability in ASP NET Could Allow Information Disclosure ScottGu Important
TLS 1 1 1 0 TLS Qualys SSL Labs Unix Linux Bash Shell Heartbleed iThome Bash specially crafted environment variables code injection attack Red Hat Security
More picture related to What Is Vulnerability In Cyber Security
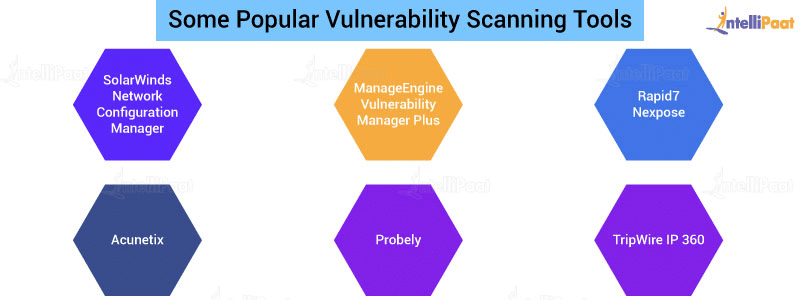
What Is Vulnerability In Cyber Security Types And Meaning 2022
https://intellipaat.com/blog/wp-content/uploads/2021/08/Some-popular-vulnerability-scanning-tools.png

What Is A Cyber Vulnerability YouTube
https://i.ytimg.com/vi/D0xSFFGFwE0/maxresdefault.jpg

OWASP Top 10 Vulnerabilities 2022 51 OFF
https://images.spiceworks.com/wp-content/uploads/2021/04/11121048/Security-Vulnerabilities1.png
Vulnerability 2019 iT HTML WYSIWYG HTML
[desc-10] [desc-11]

Vulnerability Scanning WebCheck Security
https://static.wixstatic.com/media/54de26_f2053a4133854230a045ddfe07483467~mv2.jpg/v1/fill/w_4000,h_2666,al_c/54de26_f2053a4133854230a045ddfe07483467~mv2.jpg
![]()
Cybersecurity Vector Illustration CartoonDealer 102066056
https://thumbs.dreamstime.com/z/abstract-cybersecurity-concept-red-icons-cubed-background-different-sizes-colors-aligning-to-row-glowing-79501604.jpg


https://blog.darkthread.net › blog
Successful exploitation of this vulnerability requires an attacker to exhaust all the threads in the thread pool Thread Pool Thread In this case a
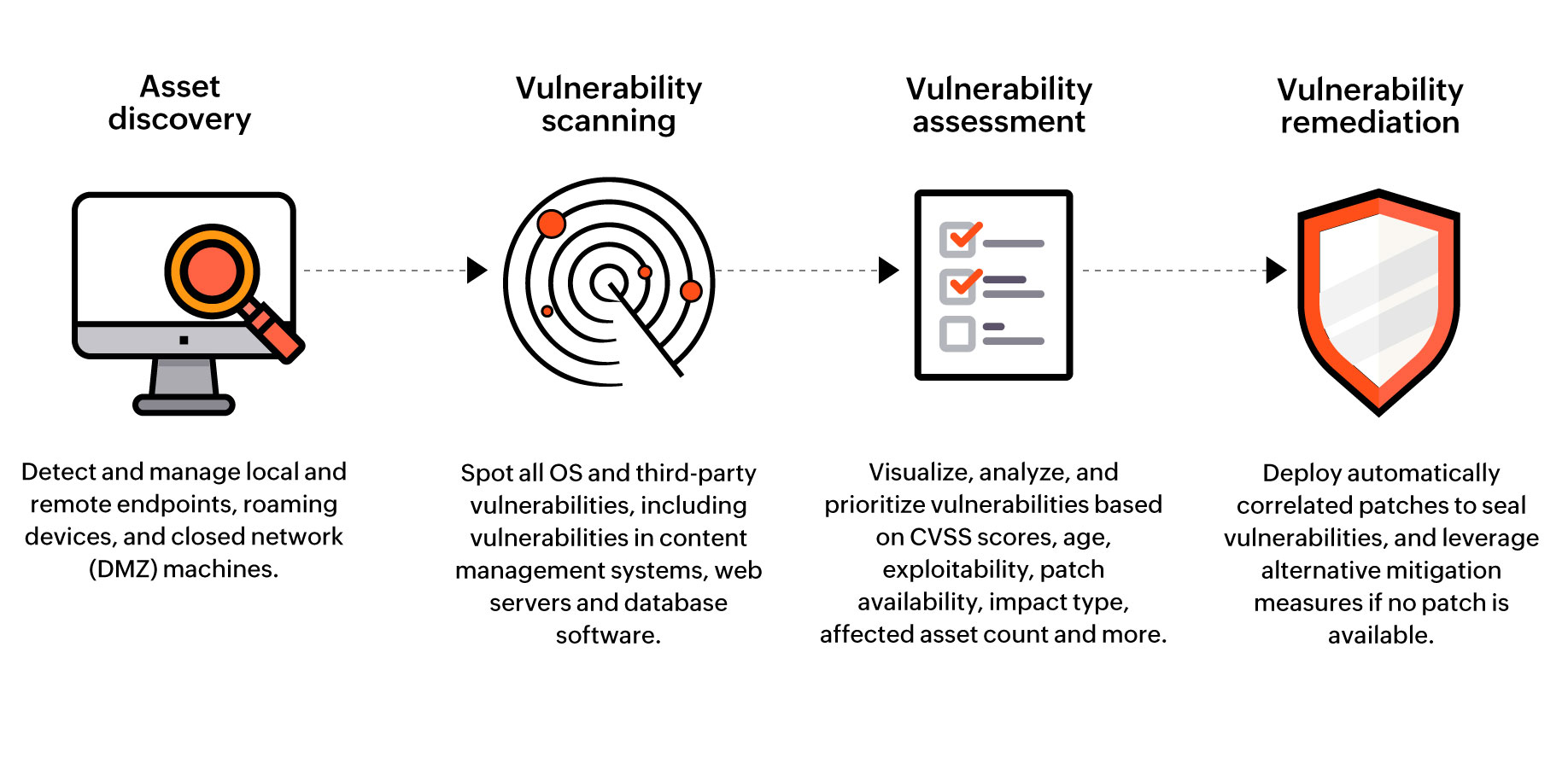
Vulnerability Diagnostic Platform Web Diagnostic

Vulnerability Scanning WebCheck Security

Vulnerability Assessment Lanworks

Cyber Risk Matrix Vrogue co

Vulnerability Management

Vulnerability Scanning

Vulnerability Scanning

Vulnerability Scanning
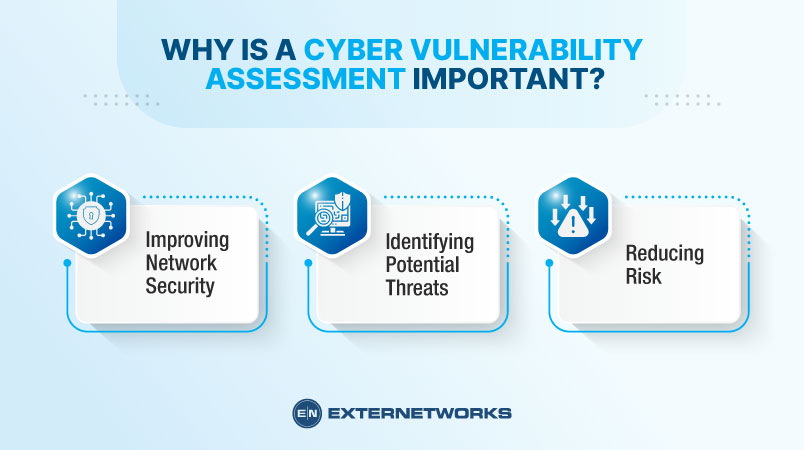
Vulnerability Assessment
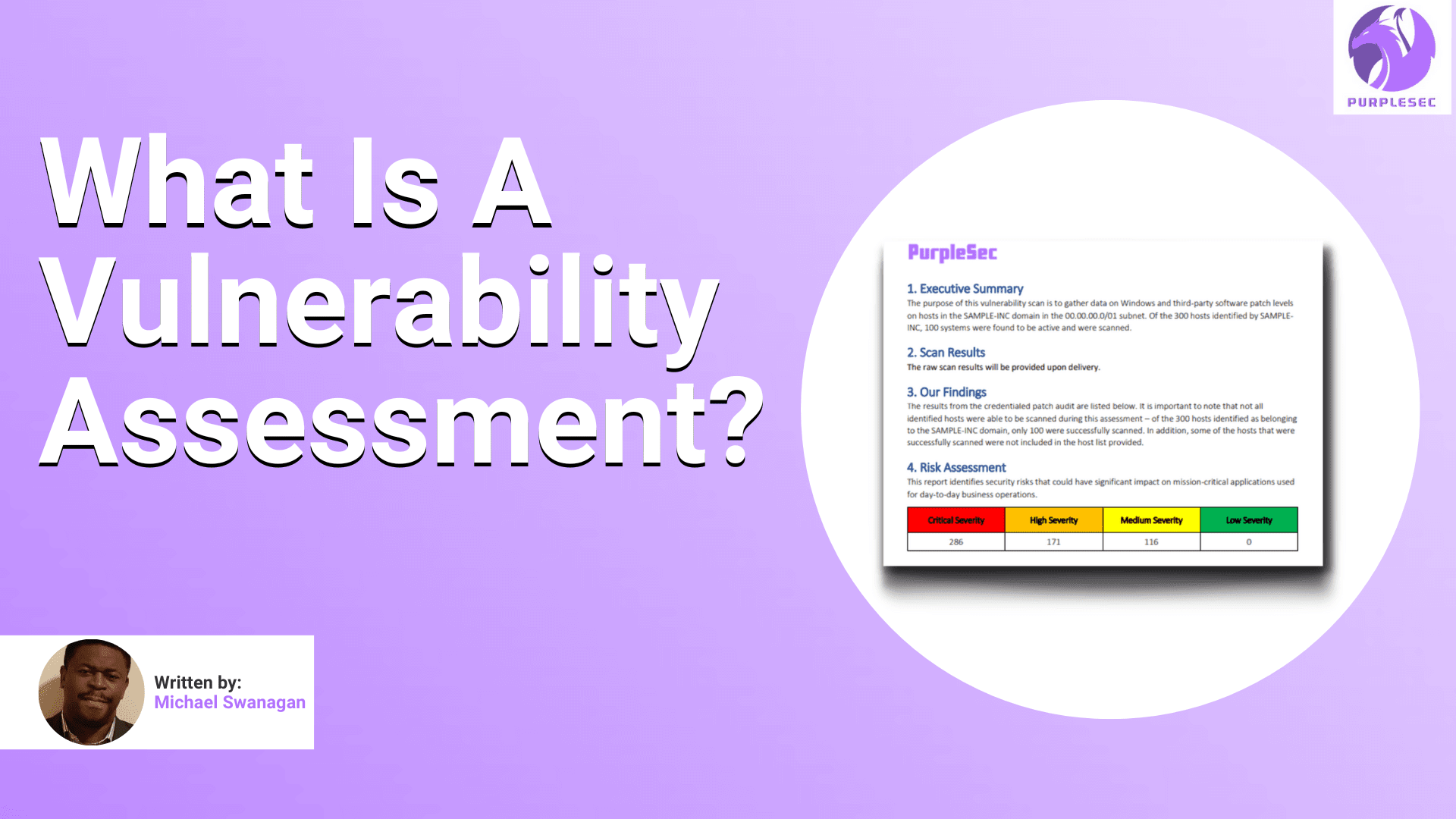
Vulnerability Assessment
What Is Vulnerability In Cyber Security - [desc-14]