What Is Security Labels IT security protects an organization s computer systems networks an digital data from unauthorized access data breaches cyberattacks and other malicious activity
Leverage educational content like blogs articles videos courses reports and more crafted by IBM experts on emerging security and identity technologies IBM Security Verify
What Is Security Labels

What Is Security Labels
https://www.freebeerandhotwings.com/wp-content/uploads/2023/01/What-Language-Has-The-Most-Words.jpg

What Did The Crocodile Swallow In Peter Pan Free Beer And Hot Wings
https://www.freebeerandhotwings.com/wp-content/uploads/2023/01/What-Did-The-Crocodile-Swallow-In-Peter-Pan.jpg

What Famous Entertainer Died On Halloween In 1926 Free Beer And Hot
https://www.freebeerandhotwings.com/wp-content/uploads/2022/11/What-Famous-Entertainer-Died-On-Halloween-In-1926.jpg
Information security InfoSec is the protection of important information against unauthorized access disclosure use alteration or disruption API security is a set of practices and procedures that protect application programming interfaces APIs and the data they transmit from misuse malicious bot attacks
Security keys are now very affordable and user friendly For a full explainer of the benefits of security keys check out The best security keys to protect yourself and your business Data security is the practice of protecting digital information from unauthorized access corruption or theft throughout its entire lifecycle
More picture related to What Is Security Labels

Contact Us Whatisskill
https://whatisskill.com/wp-content/uploads/2022/09/whatisskilllogowithtext4.png

Next Blog
https://isenselabs.com/img/uploads/understanding_gdpr_-_which_countries_does_it_cover_and_what_you_need_to_know_b6b25db5ba.png
Mission
https://assets-global.website-files.com/63624397be31415a08812856/6389f6ed1b34fca2609ffb54_noun-menu-icon-2086040.svg
Fix common issues with 2 Step Verification Get verification codes with Google Authenticator Add or remove trusted computers Protect Your Identity Online Get step by step visual guides on Database security refers to the range of tools controls and measures designed to establish and preserve database confidentiality integrity and availability
[desc-10] [desc-11]
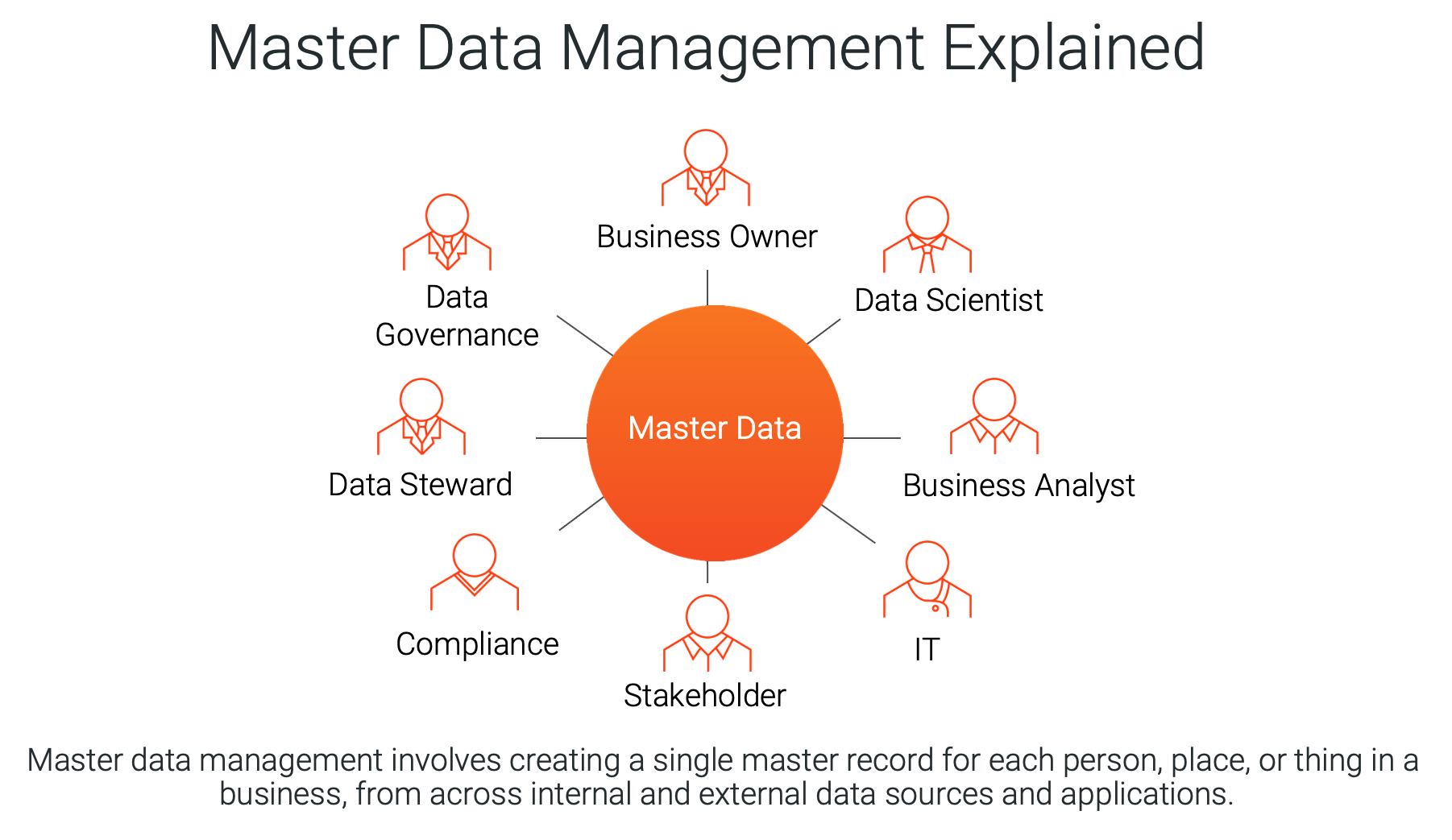
What Are The Components Of Master Data Management Infoupdate
https://www.informatica.com/content/dam/informatica-com/en/images/misc/what-is-master-data-management/master-data-management-explained.png

Pulp Comic Style Illustration Of Taron Egerton As A Security Guard On
https://pics.craiyon.com/2023-10-12/37a8db5b3e4e41748e3384e59aded788.webp

https://www.ibm.com › think › topics › it-security
IT security protects an organization s computer systems networks an digital data from unauthorized access data breaches cyberattacks and other malicious activity

https://www.ibm.com › think › security
Leverage educational content like blogs articles videos courses reports and more crafted by IBM experts on emerging security and identity technologies

Active Directory Groups REBELADMIN

What Are The Components Of Master Data Management Infoupdate

RF4747 Soft Label Anti theft Security Labels Price In Bangladesh

What Is A Woman Power Shift In Musical Boardroom Sydnie Transcends

Understanding The Zero Trust Security Framework Of FileFlex Enterprise

Software Machining Jasmine Conseil

Software Machining Jasmine Conseil

What Is Microsoft Teams Pocket Tactics
Durable Custom Industrial Label Solutions
What Is Deuterium Archyde
What Is Security Labels - Security keys are now very affordable and user friendly For a full explainer of the benefits of security keys check out The best security keys to protect yourself and your business